Okta data breach: what happened and what it means for your security

Whether you’ve heard of Okta or not, you’ve probably used it to log into apps like 1Password, Cloudflare, Twilio, DoorDash, or even your company’s healthcare platform.
Okta is the identity provider behind logins for thousands of applications. It’s primarily used by organizations to manage employee access, meaning millions of workers rely on it daily to enter corporate systems securely.
We’ve witnessed several Okta data breaches in the past few years. Despite growing scrutiny, the company remains deeply embedded in business infrastructure, making it nearly impossible for many enterprises to move away.
This article breaks down what happened in the Okta security incidents, what data was exposed, what experts and users are saying, and, most importantly, how you can protect your information.
What is Okta and why it matters to everyday users
Okta is a widely used identity and access management (IAM) platform. Founded in 2009, the company works with approximately 18,800 organizations, including the three largest cloud providers — Amazon Web Services, Microsoft, and Google Cloud.
You might already be familiar with Okta as the authentication service behind your work apps. It functions as both a single sign-on (SSO) platform and an identity provider (IdP). In other words, it verifies who you are and lets you sign in just once to access all of your work apps.
Okta may be designed for workplace use, but its impact goes far beyond corporate IT. Because millions of employees rely on it daily, any Okta compromise can put vast amounts of credentials, authentication tokens, and other sensitive data at risk.
Understanding Okta data breach incidents: 2022 – 2024 in focus
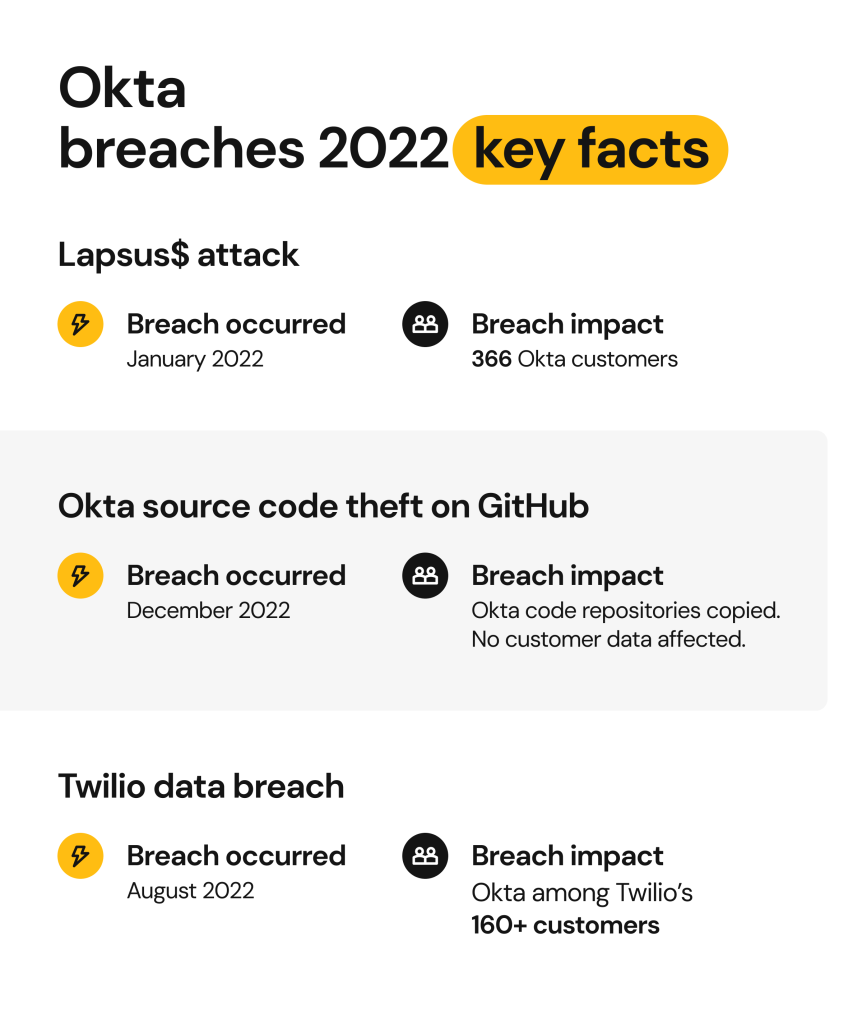
January 2022 Lapsus$ breach via third-party (Sitel)
We are conducting a thorough investigation into the recent LAPSUS$ claims and any impact on our valued customers. […] After a thorough analysis, we have concluded that a small percentage of customers – approximately 2.5% – have potentially been impacted and whose data may have been viewed or acted upon.
On March 22, 2022, Lapsus$ posted screenshots of Okta’s internal systems on their Telegram channel. The extortion cyber gang has a reputation for breaching large corporations, such as Microsoft and NVIDIA.
This Okta security breach was a vendor-related incident. Gang members gained limited access to Okta’s internal systems via Sitel, a customer service outsourcing company. They misused a Remote Desktop Protocol (RDP) to access a CS employee’s work computer.
Okta initially stated that the incident, dating back to January 2022, was contained before threat actors could do any damage. Later, Okta CSO issued a notification confirming the breach. The attack lasted about 5 days and affected 366 companies (2.5% of Okta customers).
The notification also included a detailed timeline of events. It turns out that Okta discovered the security incident back in January, but waited for the full investigation report before notifying its users.
After the breach was made public by Lapsus$, Okta reached out to the affected customers and shared a report that shows all actions performed by Sitel CS for the duration of the attack.

August 2022 Okta security incident: Twilio phishing attack
In August 2022, Okta was impacted by a phishing attack via its communications and multi-factor authentication provider, Twilio. The Twilio data breach affected approximately 163 organizations, including Cloudflare. Food delivery company DoorDash was also impacted.
Through Twilio’s internal console, bad actors were able to search for phone numbers that belong to Okta customers. They found a small number of phone numbers and SMS messages (OTPs).
December 2022 Okta Source code theft on GitHub
In early December 2022, Okta’s GitHub repositories containing its source code were accessed by an unauthorized party. The code was for Workforce Identity Cloud, Okta’s security solution for enterprises.
Okta revealed the source code leak in a notification posted on its website. GitHub, a code hosting platform, alerted the company about the incident. As source code theft was confirmed, Okta locked its GitHub repositories and suspended all GitHub integrations with third-party applications. They also notified law enforcement.
Despite the incident, Okta was business as usual. They claimed that code confidentiality is not how user security is maintained, and emphasized that hackers didn’t compromise any customer data.
Experts warn that incidents like this allow hackers to study the source code, find its vulnerabilities, and use them in future attacks.
August – September 2023 social engineering attacks on Okta customers
Between August and September 2023, multiple US-based Okta clients were hit by social engineering attacks. Some of them were successful, leading to super administrator Okta accounts being compromised.
What exactly happened? Threat actors got their hands on high-level employees’ login credentials. They successfully targeted four Okta clients.
Hackers made calls to IT departments posing as legit employees and convinced the IT workers to reset MFA for those accounts. They added new numbers or passwords, obtaining access to Okta’s super administrator accounts. These accounts have many functions, such as adding, modifying, or removing other Okta users.
Following the regulations, Okta filed a report with the SEC. The company officials also wrote a post about the incident and provided recommendations to users.
September 2023: The MGM Resorts data breach
A couple of weeks after Okta detailed the security incident in the SEC filing, its client, MGM Resorts, was targeted in a similar way. The hacking group responsible is called AlphV, also known as BlackCat. They used social engineering to gain access to the casino and hotel giant’s Okta environment, specifically the super admin accounts.
MGM Resorts had to shut down its Okta integrations to contain the incident. This caused massive disruptions in service. As the attack was carried out in a similar way, many people believed it was part of the same campaign.
Read more about AlphV/BlackCat attacks:
Prudential security breach: what you should know and do
Loan Depot data breach: what happened and how to protect your financial info
September 2023 Employee health information leak
This wasn’t a direct Okta data breach; what got Okta compromised this time was a vendor.
Rightway Healthcare, a healthcare company working with Okta, was breached in September 2023. They informed Okta about the incident a month later, on October 12.
The breach exposed sensitive health information of approximately 5000 current and former Okta employees. They accessed employee names, SSNs, and health insurance plan numbers.
The incident, however, didn’t affect any Okta customers.
September – October 2023 CS system breach (HAR file incident)
Between September 28 and October 19, 2023, a threat actor gained access to the Okta customer support (CS) management system. They used stolen access credentials and malware.
Threat actors likely got the credentials by hacking into the personal Google account of an Okta employee.
How could that have led to a breach? Well, the employee used their personal account on an Okta laptop, and Google picked up the login credentials.
From there, they exposed the HAR files, short for HTTP Archive Record, that capture all network activity (like cookies and tokens). Okta customers typically share these files with CS during the troubleshooting process.
Okta discovered the incident and on October 19, 2022, notified BeyondTrust, Cloudflare and 1Password that they had been impacted by a data breach. At that time, Okta believed incident affected less than 1% of their customers. Later reports revealed that the Okta security breach exposed files of all customers.
Also, the hackers downloaded the reports with the names and emails of all CS users and hijacked the legitimate sessions of five Okta clients.
2024 Sign-on policy bypass vulnerability
Between July 17 and October 4, 2024, a bug in the new version of the Okta Classic app allowed attackers to bypass strict sign-on policies. They still needed to have valid usernames and passwords though.
Okta usually approves logins from trusted devices and networks only. The July 17 app update allowed users to log in using an unknown script or an unknown browser.
Okta discovered the vulnerability on September 27, 2024, and patched it by October 04, 2024. They also advised users on how to review the Okta system log for unfamiliar authentications in a post about the incident.
What data was compromised in the Okta security breaches?
| Okta security incident | Data types exposed |
|---|---|
| 2022 Lapsus$ incident | Limited CS data for 366 Okta clients (organizations) |
| 2022 Twilio phishing scam | SMS OTP messages and phone numbers tied to Okta |
| 2022 GitHub source code theft | Workforce Identity Cloud source code |
| 2023 Support system data breach | Files of 134 Okta clients, including HAR files with session tokens;Report of all CS users’ names and emails |
| 2023 Rightway Healthcare data breach | Health information of approximately 5000 current and former Okta employees |
Okta response: did they do enough?
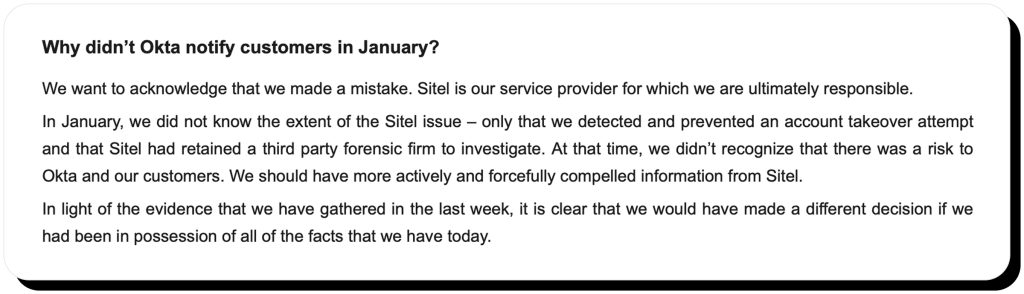
Lapsus$ attack: denial, backlash and belated apologies
In January, we did not know the extent of the Sitel issue – only that we detected and prevented an account takeover attempt and that Sitel had retained a third-party forensic firm to investigate. At that time, we didn’t recognize that there was a risk to Okta and our customers. We should have more actively and forcefully compelled information from Sitel.
After Okta detected a failed attempt to hack the account of a third-party CS agent, they terminated the user’s session and suspended their account. The incident was reported to Sitel, who launched an external investigation. Two months have lapsed, and Okta hasn’t notified the public about the incident until Lapsus$ posted the log screenshots. The company acknowledged their mistake in an FAQ release regarding the incident.
GitHub source code theft downplayed
After the source code leak, Okta secured its GitHub repositories and disabled third party GitHub app integrations. The company issued only a brief statement on its website.
According to the post, the confidentiality of source code isn’t relied on for customer security. Some experts thought that was downplaying the significance of the incident. Whenever a source code is exposed, it leaves the app vulnerable to customized, targeted attacks.
Support system breach: lessons learnt?
Upon discovering the support system breach, Okta hired a leading cybersecurity forensics firm, Stroz Friedberg, to thoroughly investigate the incident. The findings revealed the full scope of the incident and found no further malicious activity.
This time around, the company implemented security upgrades. They wrote about it in the last incident update:
- Zero-standing privileges for administrative roles; They are assigned only when necessary and for a limited time.
- MFA is required for high-impact administrative tasks.
- Improved session security: requests from anonymizers are blocked, and IP blinding is applied to Okta products and the Admin Console.
- API access is restricted to prevent unauthorized access.
- Customers are urged to rotate tokens and credentials.
What experts and users are saying
Despite us all knowing and understanding what Risk is and that there is always a likelihood of attack, we are very hard on any organization that gets breached…How an organization responds to an event, including how it communicates, is the larger issue. OKTA can’t even tell me the truth about the impact?
Okta’s relationship with clients and end-users was bruised in the many cybersecurity incidents. The company built a reputation for delays in notification, changing statements, and repeated incidents.
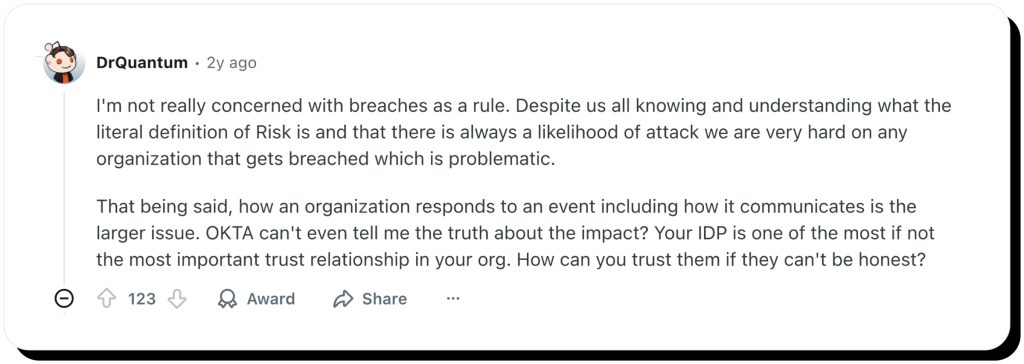
Although companies are seemingly not happy with Okta’s data breach track record, switching to a different ID provider and access management tool would be a huge endeavor. Okta is deeply rooted in many systems and corporations. For many, rebuilding their environment and integrations would be very difficult, time-consuming, and costly.
Why are Okta data breaches dangerous?
Although no Okta data breach exposed the end-users’ sensitive information, there are inherent risks, as with any data breach.
- Credential reuse risk: If your Okta-linked work login matches your personal passwords elsewhere, a stolen token or credential can expose your other accounts.
- Targeted phishing: Attackers can use leaked emails and company domains to create convincing fake MFA or password reset messages. These often mimic Okta login pages or MFA prompts, requesting credentials or the approval of fake login requests.
- Session hijacking: Stolen session tokens (like in the 2023 breach) let attackers skip MFA entirely. They act as digital “keys” and keep them logged in, so they can act as the real user.
- Reputation risk: Repeated security issues also raise concerns about Okta’s internal controls and transparency. With each new breach, customers are becoming nervous about relying on Okta as their identity provider.
How to protect yourself if your data is in the Okta breach
Change passwords and don’t reuse them
It’s important to keep your work and private logins separate. This applies to recycling passwords as well as using a corporate email for personal accounts, and vice versa. If your company has been affected by a recent Okta security incident, make sure to change all of your reused passwords.
Enable phishing-resistant MFA wherever possible
Besides having a complex and unique password, using MFA is the best way to protect your accounts. But, receiving the MFA code via SMS makes you vulnerable to SIM swapping. Use hardware security keys (like YubiKey and Titan) or device-based passkeys instead.
Watch for phishing and impersonation attempts
Phishing attacks are a natural sequel to data breaches. Expect more “Okta verification” or “Support ticket” emails in the weeks following a breach. Remember that the goal of these attacks is to obtain your credentials or get you to verify an MFA request. Don’t ever approve unexpected MFA prompts.
Monitor your personal data exposure
When it comes to data breaches, some data is more sensitive than others, but no data is safe to distribute. Even admin emails can be cross-referenced with other leaks to build a better victim profile.
You can check if your email or phone number has been exposed in a known data breach using tools like HaveIBeenPwned. As of recently, Onerep offers the same service along with all of our subscription plans.
Remove personal data from data broker sites
After major data breaches, attackers often gather personal information (address, phone number, family details and many more) from people-search websites and data brokers. They do it because they know perfectly well that private information can fuel scams. The more bad actors know about you, the more convincing their phishing scams are.
Onerep automatically scans over 230 privacy breaching websites and removes your information from all that expose your information, helping reduce spam, social engineering, and identity theft risks.
Start your privacy protection with a free Onerep scan
Lessons from Okta’s repeated breaches
Data breaches of large organizations, and especially security firms, make for insightful case studies. Here is what we can learn from the Okta security incidents:
- Security fatigue is real: Every provider will get breached eventually, so why bother? Even experts joke about how frequent these incidents have become. People are getting used to cybersecurity failures, which can be detrimental. User awareness is just as important as a platform’s technical defenses.
- Transparency counts: When a breach happens, users often care more about how a company communicates than how the incident happened. Delayed disclosures and unclear or fabricated statements can erode trust faster than the breach itself. Clear and timely updates on what happened, who was affected, and what’s being done help organizations preserve credibility even in times of crisis.
- No provider is immune: Even large security companies can be compromised. Identity is the new attack surface. This means that your personal vigilance (password protection and MFA) matters more than the brand name of the company.
Final thoughts
Okta’s story is a reminder that even security companies are vulnerable to cybercrime, and there is no definitive way to prevent data breaches. Organizations can only control how well they respond in light of these incidents.
For most everyday users, this means two things. First, you can’t rely blindly on corporate security policies. Second, you should protect yourself by limiting your personal data exposure.
Make a habit of having a simple password security routine, breach monitoring, and removing personal data from public sites. This isn’t paranoia, just baseline cybersecurity hygiene in the world we live in.





Mikalai is a Chief Technical Officer at Onerep. With a degree in Computer Science, he headed the developer team that automated the previously manual process of removing personal information from data brokers, making Onerep the industry’s first fully automated tool to bulk-remove unauthorized profiles from the internet.