What is dark web monitoring? Benefits, limitations, and how to protect your personal data

Dark web monitoring is a cybersecurity data scanning technique for uncovering information in the dark web — the hidden part of the internet that’s inaccessible for common search engines and browsers. The goal of this technique is to track down the personal details of individuals and organizations that’ve been stolen or leaked in data breaches, such as credentials, personally identifiable information, hacked emails, intellectual property, and more.
Providing that in 2023 alone over 353 million people were affected by data compromises in the US, there’s a high chance your personal details might surface on the dark web too. The consequences? Potential risks of identity theft, financial fraud, account takeover and reputational damage.
This guide will help you understand how dark web monitoring works and how it can help you better protect your personal information from being exploited.
Understanding the dark web
To understand what dark web monitoring is, let’s position it in relation to the two other layers of the internet — the deep web and the surface web.
The dark web is the deepest layer of the internet that exists on overlay networks and is only accessible with special software, configuration and authorization. The dark web content is not indexed by search engines and is typically hidden there intentionally.
The dark web is part of the deep web that also contains unindexed, encrypted information that’s hidden behind logins and passwords and is thus non-searchable — think email messages, paywalled content, private databases, bank account details, and so on.
Lastly, the surface web is the layer you’re most familiar with as this is where you find websites and tools you use day to day. It’s visible, accessible, and indexed by search engines.
How does dark web monitoring work?
Dark web monitoring services scan darknet websites, forums, data dumps and marketplaces continuously to find any traces of specific compromised information, such as Social Security numbers, email addresses, passport numbers, medical identification numbers, bank account numbers, phone numbers, driver’s licenses, leaked corporate data and so on.
How do they do it? Using a range of techniques, from automated web crawlers similar to search engine bots to advanced machine learning methods, these tools are trained to access and sift through millions of records to find mentions of the target.
Data sources and scanning techniques
Automated dark web monitoring tools scan for specific keywords, phrases or information related to an individual or an organization. Once there’s a match, the tool will send an automated alert to take action.
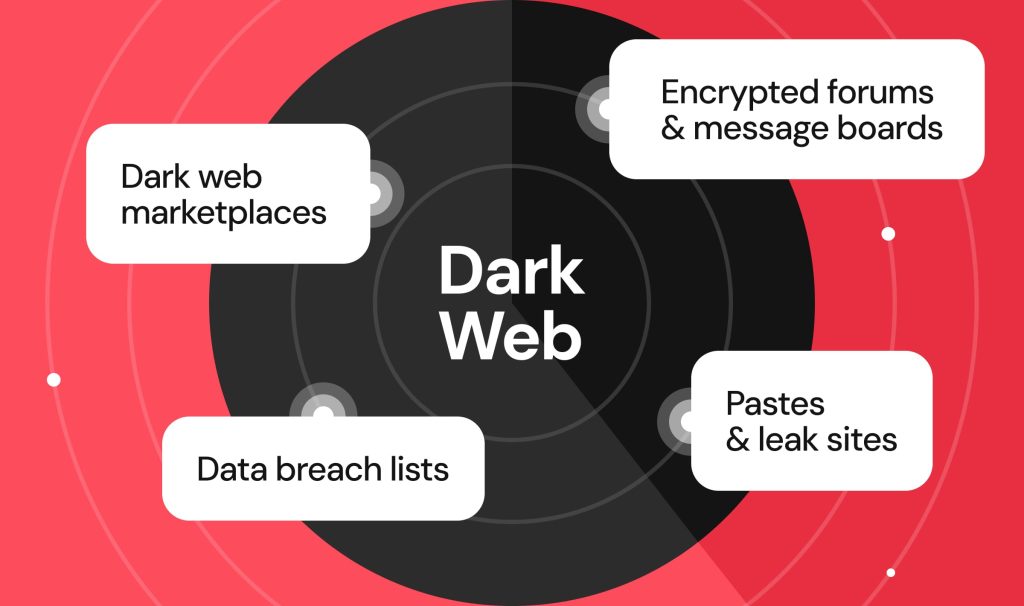
The typical data sources scanned by dark web security monitoring software include:
- Dark web marketplaces
- Encrypted forums and message boards
- Data breach lists
- Pastes and leak sites
Deep web monitoring tools use a range of techniques to scan and identify compromised data. They include web crawling, keyword monitoring, data fingerprinting (creating unique identifiers for sensitive data and then searching for the ‘fingerprints’ of this data), social listening and community monitoring, among others. Advanced techniques include the use of machine learning and artificial intelligence to uncover suspicious patterns, monitor for new threats and even predict emerging risks.
Automated monitoring vs. manual investigation
Not all information can be successfully uncovered using only automated monitoring.
While automated tools can tirelessly scan millions of records and trigger immediate alerts upon detecting a suspicious activity, they’re also context-blind and may trigger false positives.
The next level of dark web monitoring is what can be called dark web surveillance — a holistic investigation of cybercriminal activities on the dark web involving both automated and manual information analysis. Dark web surveillance marries automated tools with human intelligence, where human security analysts manually inspect dark web sources, validate automated alerts and even interact with threat actors undercover to gather insider intel.
The majority of mature corporate security operations centers use the combination of both automated and manual dark web monitoring solutions. For individual use, however, a simple dark web scanner will often be enough to ensure peace of mind.
Why is dark web monitoring important?
While dark web monitoring sounds like something only corporations and governments might be interested in, it can be tremendously useful for everyone cautious about their safety online.
A lot of personal information ends up on the dark web without the victims being aware, and this can often have real-life consequences when the data is sold to cybercriminals, used in scams and identity thefts, or exploited in phishing attacks to gain unauthorized access to corporate networks.
Let’s explore key benefits of monitoring the dark web both for companies and individuals.

Preventing identity theft and fraud
Gaining access to your full name, address and Social Security number can be enough to steal your identity. Criminals exploit such information to take out loans and open credit cards in victims’ names.
If any of this personally identifiable information is found on the dark web, it can be a huge red flag that someone could be preparing to exploit it against you.
Using a dark web scanner, you can detect this early and take preventive actions such as freeze your credit, notify your bank, change passwords, enable two-factor authentication, and start monitoring for fraud before the damage is done.
Detecting data breaches early
Monitoring the dark web can be the fastest way to learn that a data breach has occurred. Both businesses and individuals can use it to see if their sensitive information has been leaked, often before a data breach is even publicly disclosed.
The sooner you uncover this and start acting, the harder it will be for cybercriminals to gain anything from it. When running the dark web scans 24/7, it’s possible to detect a data breach almost instantly and mitigate the risks as soon as possible so that malicious actors have less time to act on the stolen data.
Safeguarding personal and professional reputation
As an extension of who you are online, your digital identity is extremely important. Monitoring the dark web for any traces of your contact details, messages, medical information and other private data can help avoid potential impersonation scams, harassment and doxxing (revealing your private information publicly without your consent).
Dark web monitoring services are equally useful for protecting professional reputation. In case of leaked corporate details, such as emails, internal documents, or customer credentials, you can flag this internally as early as possible and take timely action before this data makes your company a target of a phishing scam or extortion.
Challenges and limitations of dark web monitoring
The limitations of dark web monitoring tools come down mostly to the inaccessibility of data for dark web scanners:
- When communication happens in end-to-end encrypted platforms (for example, Telegram), or in private chats, password-protected marketplaces, and invite-only forums, accessing this data may require a human analyst infiltrating these channels.
- If the service is new, hidden or otherwise unmapped to the scanning tool that relies on crawling only known sources.
- Automated scanners can’t understand context as they only search for keywords or patterns, so when threat actors use slang, codewords or obfuscation, the scanners might overlook a threat or trigger a false positive.
- Not all tools scan 24/7. In some cases, the intervals are daily or even weekly, which can be critical in case of a data breach that requires immediate action.
- Compromised data may be fragmented, corrupted or incomplete, leading to limited information about the scope of leaked details.
Lastly, the number one limitation of dark web monitoring is that it can’t protect your data from appearing on the dark web in the first place. It’s reactive, not preventative, and often only sends alerts for data that has already been compromised. The rest depends on how swift and effective your mitigation steps are.
Ways to protect your information from the dark web
Prevention is the best remedy, and it starts with the simplest steps available to everyone. Make the following part of your cyber hygiene, and your personal details will have far less chance of ending up in the wrong hands, on the dark web and elsewhere.

Use unique, strong passwords
Leaked credentials are the most common type of data found on the dark web, and they can also lead cybercriminals to multiple accounts if you have this bad habit of reusing the same passwords.
If you want a simple way to come up with unique passwords every single time and also store them effortlessly, use a password manager. Many are free, and some of them even offer a way to alert you if your credentials are found in known data breaches.
Enable two-factor authentication (2FA)
2FA gives you an extra layer of protection, so please enable it wherever possible. For added security, tie it down to an authenticator, like Google Authenticator. Even if your password does get leaked, cybercriminals will have a hard time accessing your accounts.
Limit the information you share online
Oversharing might have been good in the early days of social media, but now it’s simply unsafe. Birthdays, addresses, pet names, your mother’s maiden name can all tip off cybercriminals about the answers to common security questions and make you more susceptible to impersonation scams.
Remove personal data from the surface web
As counterintuitive to our sharing culture as it sounds, this step will minimize the scope of your personal details floating out there in the regular web. Data removal services like Onerep help trace down and remove your personal information from the internet, including Google and people-search websites acting as data brokers. This makes it harder for bad actors to target you with all sorts of scams and robocalls while also protecting your data from appearing on the dark web, too.
FAQ
What are the best dark web monitoring services?
The best dark web monitoring services for individuals include Norton LifeLock and Bitdefender Digital Identity Protection, while solutions for businesses feature SpyCloud, Constella Intelligence and ZeroFox, to name a few.
What is dark web surveillance?
Dark web surveillance is the next-level dark web monitoring that includes systematic observation and analysis of dark web assets using a combination of automated tools and human intelligence.
How does dark web surveillance differ from monitoring?
While dark web monitoring can be a one-time action to detect the presence of specific sensitive information on the dark web, surveillance campaigns are more broadly reaching. Their goal is to monitor and pin down cybercriminal activities as part of law enforcement or holistic enterprise-level cybersecurity activities. Dark web surveillance is also carried out with humans in the loop, not only automated scanners.
Can individuals use dark web monitoring tools?
Absolutely! Many dark web monitoring tools are consumer-grade and some of them are free, letting you quickly check the safety of your personal details with no cybersecurity skills required.




Dimitri is a tech entrepreneur and founder of Onerep, the first fully automated data removal service. Top cybersecurity CEO of 2021 by The Software Report.