Is Tor safe to use in 2025? What you need to know about privacy, security, and risks
Tor – aka The Onion Router – is generally considered safe to use in 2025. The browser employs decentralized, multi-layered encryption to hide your IP address, therefore protecting your location and identity. However, Tor cannot guarantee complete anonymity when using the Internet, as advanced attacks and human error can still expose you while using the browser.
What is Tor Browser and how does it work?
Tor is a browser that allows you to securely and anonymously surf the Internet. Unlike traditional browsers (think Chrome, Firefox, and Safari), Tor routes traffic through a global network of volunteer relays designed to keep your identity hidden.
Tor’s primary goals are to:
- Protect your anonymity
- Circumvent censorship
- Prevent surveillance
- Promote freedom of information
Tor does this by blocking trackers and by routing your traffic through multiple encrypted nodes:
- Entry node: Your traffic is first routed through the entry node, which can view your IP address – but not your destination (like a website).
- Middle node: Sends your traffic to the exit node, but cannot view your IP address or your destination.
- Exit node: Sends your traffic to your destination, but cannot view your IP address and therefore cannot decipher your identity.
Think of it like three layers of an onion. The first and third layers never touch, as they’re separated by the second layer, so they never expose where you’re coming from or where you’re going.
As for the architecture of it all, Tor is open source and community-driven:
- Open-source code ensures transparency
- A strong developer community is committed to improving the browser and fixing bugs
- Volunteers operate worldwide servers, decentralizing Tor traffic
However, despite its robust privacy features, it’s important to understand that Tor doesn’t guarantee absolute anonymity, nor does it protect against all threats. Unfortunately, criminals can also use Tor for illegal activities on the dark web.
What is Tor used for?
Tor can help protect your online privacy, as it can keep your identity anonymous even if your traffic is being monitored. It’s critical software for journalists, activists, and whistleblowers who use Tor to pass important information, communicate with sources, circumvent censorship, coordinate protests, or access sites (such as news media) banned in certain countries.
Some famous examples of Tor use include:
- Edward Snowden used Tor to blow the whistle on US government surveillance activities
- Major news outlets such as The Washington Post and The Guardian run .onion sites for whistleblowers
- BBC provides an onion service – or “dark web mirror” – for unrestricted access to its content in countries that block it
Tor also allows users to access .onion sites. These sites work exclusively with Tor and are designed to hide both your identity and the websites themselves. When you browse to a .onion site, both your traffic and the website pass through three encrypted nodes – making it a total of six nodes – and meet in the middle at a “rendezvous point.” This helps prevent anyone monitoring network traffic from spying on you or the destination website.
Popular .onion sites include Facebook, SecureDrop, and Torch. But remember that you should only access .onion sites from addresses listed on websites you already know and trust – and never click random links.
Note that Tor can be slow due to routing traffic through multiple relays. It’s best for browsing and sending secure documents, but it’s not a great option for high-bandwidth activities such as streaming videos or for financial applications, since they require you to submit your login and/or other personal information.
How secure is Tor Browser?
Tor provides strong anonymity compared to regular browsing. But as described above, it’s not bulletproof. Here are the features that make Tor secure:
- Layered, encrypted relay network: By routing your traffic through multiple encrypted nodes (remember the onion layers, where the first and third layers never touch), Tor can prevent your IP from being tracked. No single node knows both who you are and which site you are visiting.
- Decentralization: A global relay network also means there is no single server or location for hackers to attack or entities to spy on.
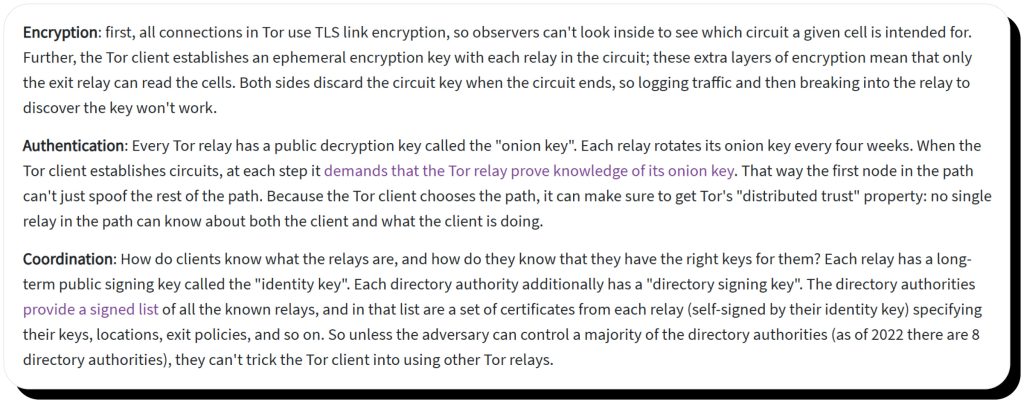
- Multiple keys: Tor uses encryption, authentication, and coordination keys to protect data privacy and ensure proper, secure relay routing.
- Frequent path changes: Tor changes circuits – the three-node hop that keeps you secure – every ten minutes, preventing long-term surveillance.
- Open source: Because Tor is open source, its code is frequently reviewed by security and privacy experts who can quickly identify and resolve vulnerabilities. In comparison, closed-source software vulnerabilities can remain under the radar for years.
Known vulnerabilities and limitations
Even with Tor, your identity could be exposed, your activity monitored, and even your identity stolen through:
- Malware: Spyware installed on your device can track your behavior.
- Exit node monitoring: If you’re browsing normal sites without HTTPS, your activity could be tracked.
- End-to-end correlation attacks: It’s possible, if unlikely, for both your traffic and your destinations to be monitored, so that your traffic patterns and visit timings can be matched to reveal your identity.
- Logins and forms: If you log in to websites or fill out forms with personal information while using Tor, you reveal your identity.
- Downloads: Downloading files and opening them outside of Tor.
- Malicious relays: Some relays are operated by hackers posing as volunteers.
- Browser fingerprinting: If you customize Tor browser, it could make it easier to identify you.
Thus, Tor should be considered more secure than traditional browsing, but not 100% foolproof. That said, for most users, the biggest potential vulnerabilities are related to user error – logging into personal accounts, filling out webforms, and other activities in which you willingly share your personal data.
So, is Tor safe to download?
Yes, Tor is safe to download from the official Tor website (https://www.torproject.org) and trusted app stores. Be wary of fake versions that are distributed via third-party sites and forums. These versions might look legit, but they’re likely infected with malware designed to track you, access your device, or even steal your money.
Is Tor Browser legal?
Yes, Tor is legal in most countries, including the United States. However, some countries restrict or block access to it, including Russia, China, and Iran. Authoritarian regimes often block Tor to maintain surveillance and control, censor ideas, and prevent citizens from organizing protests.
However, people living in those countries can still access Tor through bridges, pluggable transports, special operating systems, and even VPNs designed to mask Tor usage and prevent it from being blocked.
Of course, even though Tor itself is legal, cybercriminals can abuse it to carry out illegal activities, including:
- Darknet markets for drugs, weapons, and counterfeit money
- Ransomware payment portals (and data leaks, if ransoms go unpaid)
- Malware distribution
This puts Tor at a crossroads between privacy protection, activism/whistleblowing/journalism for the common good, and criminal activity that spurs ongoing debates about regulation and surveillance. Law enforcement leaders have legitimate concerns about Tor’s role in cybercrime, including the drug market and even child abuse and human trafficking, while privacy advocates argue that Tor is critical to maintaining freedom of the press and even democracy itself.
The question is, should Tor be forced to weaken its security to help law enforcement identify criminals, or should its security be maintained and even strengthened to protect users’ anonymity?
Common myths about Tor
Let’s dispel some common myths about Tor:
Myth #1: Tor is only used by criminals
While some criminals do use Tor for its anonymity, it’s mostly used by law-abiding citizens who wish to protect their privacy and prevent being tracked. It’s also heavily used to circumvent censorship and by journalists, activists, and whistleblowers who need to protect their identities when reporting and sharing sensitive information.
Myth #2: Tor makes you 100% anonymous
Typically, Tor does a great job of hiding your identity by masking your IP address. However, user mistakes (such as logging into social media accounts) and advanced attacks can still identify you.
Myth #3: it’s the same thing as the dark web
Though some use Tor to access the dark web, it’s not the same thing, and most people use Tor to browse legitimate, legal websites. Tor is a browser that provides anonymous access to the internet, while the dark web is a hidden part of the internet that isn’t indexed by search engines and can only be accessed with special tools.
Myth #4: Tor is illegal
Tor is legal in most countries, though some – particularly authoritarian regimes – block or restrict it.
Myth #5: the Tor network is run by basement computers
Many Tor relays are hosted on professional servers operated by volunteers, nonprofit non-government organizations (NGOs) like the Foundation for Applied Privacy, and college universities, not hackers living in their parents’ basements.
Tor vs VPNs: what’s the difference?
Like Tor, Virtual Private Networks (VPNs) attempt to hide your IP address and protect your identity. However, they work a bit differently.
Where Tor routes your traffic through three different nodes, VPNs route it through a single server. VPNs can see your IP address, and some (but not all) even log it. In other words, the VPN can see you, even if the rest of the Internet can’t.
That said, VPNs tend to be faster than Tor, and they’re good for streaming videos. In fact, many users use VPNs to “change” their locations so they can access geo-blocked content.
Ultimately, Tor offers anonymity through decentralization, while VPNs offer privacy through trust, as you must place your trust in your VPN company. You can even use Tor and VPNs together if they are properly configured, and some VPNs have special Tor features, including ProtonVPN and NordVPN.
Best practices for using Tor securely
Here are ten best practices for using Tor securely:
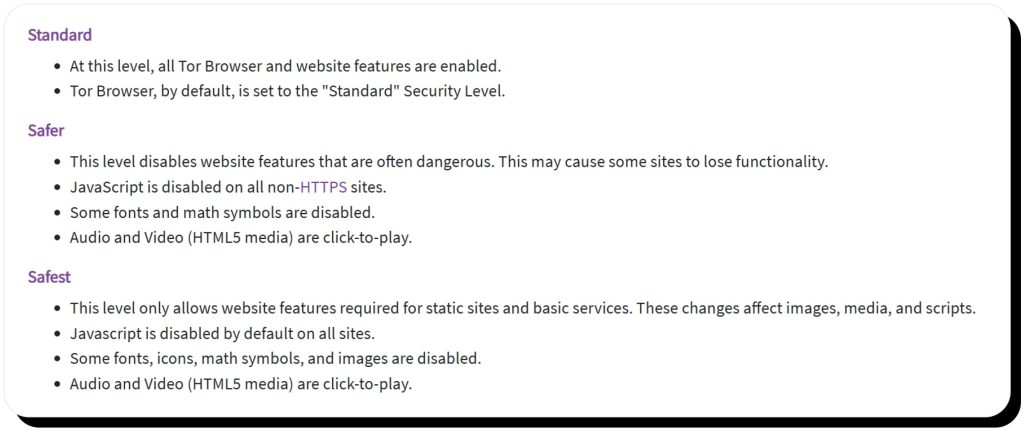
Consider setting Tor to “safer” or “safest”
By default, the Tor browser is set at its standard security. It’s pretty good, but you can browse even more securely by changing the security level to safer, which disables certain website features, and safest, which is even more aggressive. Learn more about security levels and change your setting by opening the Tor browser and selecting Settings > Privacy & Security.
Do not use proxy browsers
Only use the official Tor browser, not browsers that use Tor as a proxy, since they might not be properly configured.
Never log in to your accounts or fill out online forms
When using Tor, avoid logging in to any website – especially social media and banking apps – and never submit personally identifiable information to online forms. Revealing your identity in this manner defeats the purpose of using Tor in the first place.
Be careful when filesharing
Don’t use BitTorrent over Tor, which isn’t secure. Instead, use OnionShare. In addition, you should never open documents downloaded online while using Tor, as doing so could expose your IP address.
Always use HTTPS and never install browser plugins
Never browse to unsecure HTTP websites. Always make sure any sites you visit are HTTPS (Tor should force this by default). You should also avoid installing or using browser plugins, as third-party plugins could spy on your activity and use it to identify you.
Use a bridge
Tor doesn’t necessarily stop someone from viewing your Internet traffic or determining that you’re using the Tor network. If you want another level of security, consider using a bridge.
Don’t use a VPN (unless you know what you’re doing)
Misconfigured VPNs could complicate security and even expose your IP address, location, and identity when used with Tor. Only use a VPN if you absolutely know what you are doing.
Do not use Tor for shopping, banking, or other sensitive purposes
Never make purchases or conduct any financial dealings when using Tor, as these platforms typically require you to log in and/or share your payment information, which instantly exposes your identity.
Be careful of .onion sites
While there are plenty of legitimate .onion sites, some are designed to steal your information or spread malware. Only follow .onion links from well-known, legitimate websites to ensure you know where you’re going before you get there.
Protect your online privacy
Staying safe on Tor goes beyond browser best practices. Hackers, scammers, and other criminals often use people-search sites – data brokers that publicly publish personal information about you – to piece together data they can use to identify you, guess your passwords, or impersonate you to gain access to your accounts.
The best way to prevent that is to make sure people-search sites don’t have your information in the first place. You can remove your records manually or use an automatic service like Onerep.
FAQs
Is Tor browser safe?
Yes, the Tor browser is safe when you download it from the official Tor Project website. However, while Tor can protect your privacy and identity, it’s important to remember that the browser cannot guarantee complete anonymity.
Is Tor legit?
Yes, Tor is a legitimate browser maintained by the Tor Project, a nonprofit organization, and a strong community of privacy advocates. People all over the world use Tor to protect privacy, circumvent censorship, and blow the whistle on government and corporate misconduct.
Is Tor dangerous?
While Tor isn’t inherently dangerous, it can be used to access dangerous sites on the dark web. It’s also true that criminals can use Tor to hide their identities. Tor is a tool, and how it’s used depends on the user.
Is Onion Browser safe?
Yes, Onion Browser for iOS is generally considered safe. It’s even recommended by Tor (along with Orbot, a Tor VPN for smartphones). However, it doesn’t have the exact same privacy protection as Tor because Apple requires all iOS browsers to use WebKit.
Is it illegal to use Tor?
No, it is not illegal to use Tor in most countries (including the US). However, some governments restrict or block access to Tor – typically to censor ideas or prevent organized protest.
Is Tor legal in the US?
Yes, Tor is legal in the US. The United States does not block Tor, and there are no restrictions on its use. In fact, Tor originated from the US Naval Research Lab in 1995.





Mark comes from a strong background in the identity theft protection and consumer credit world, having spent 4 years at Experian, including working on FreeCreditReport and ProtectMyID. He is frequently featured on various media outlets, including MarketWatch, Yahoo News, WTVC, CBS News, and others.