Robinhood data breach: what happened and how to safeguard your information

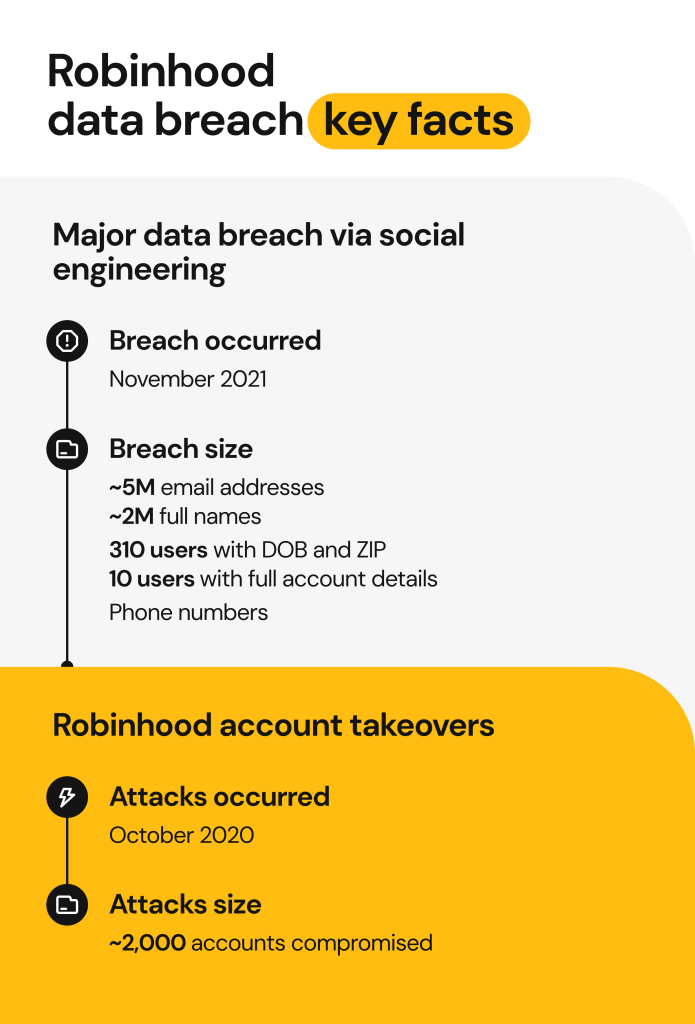
Robinhood, a widely used U.S. trading platform, has faced multiple security incidents. In November 2021, a social-engineering attack targeting customer support led to the Robinhood data breach, exposing roughly five million email addresses, about two million full names, and limited additional details for a small subset of customers. Separately, in 2020, about 2,000 customer accounts were taken over in a hacking spree, with some victims reporting unauthorized trades and withdrawals.
These events sparked significant backlash: class-action litigation over the 2020 account takeovers, regulatory penalties tied to safeguarding customer information, and broader scrutiny of fintech security practices.
This guide explains what happened in both incidents, how Robinhood and regulators responded, the real risks to customers, and practical steps you can take to minimize your exposure and protect your information.
What happened in the 2021 Robinhood data breach?
Was Robinhood hacked?
In November 2021, Robinhood disclosed a security breach that compromised customer accounts linked to its brokerage platform. The company confirmed that an unauthorized third party manipulated a customer support employee with social engineering, allowing access to its internal systems.
Then, the attacker used internal support tools to view customer information, gaining unfettered data access without having to breach Robinhood’s core systems. According to Robinhood, intruders exposed five million user email addresses, another two million full names, and additional sensitive details. This Robinhood data breach also impacted a smaller group of approximately 310, where bad actors stole additional personal data, including:
- Customer names
- Birthday
- Zip codes
Finally, 10 Robinhood users had more extensive account information exposed.
After investigation, Robinhood stated that the attacks didn’t reveal any Social Security numbers, bank details, or other financial data.
When Robinhood contained the intruders, they demanded a ransom payment. The company informed law enforcement and promptly continued their investigation with the help of Mandiant, an industry-leading cybersecurity firm. In response, Robinhood chose transparency and notified everyone of the ongoing investigation.
Yet, the question remains: Was Robinhood hacked? Technically, criminals didn’t directly attack Robinhood’s systems with malware or network exploitation. The breach happened because of social engineering, which relies on persuasive communication and preys on human behavior instead of software vulnerabilities.
In many cases, like the Twitter data breach, threat actors deceive customer support employees by convincing them that their request is urgent and legitimate, before they gain access to internal systems. During the Robinhood security breach, threat actors accessed customer lists through internal portals and exposed user credentials, leading to a widespread data exposure event.
The attack revealed that Robinhood’s online trading system reportedly lacked basic safeguards used by other broker–dealers, such as verifying changes in the linked accounts, or flagging unusual login activity before transferring funds.
This oversight made it easier for bad actors to exploit the gap, move between support systems, and ultimately expose millions of Robinhood users.
What data was exposed?
According to information security experts at HaveIBeenPwned, the Robinhood data breach exposed data that varied by the user. Attackers exposed 5 million user email addresses and their full names. Approximately 310 customers had their birthdays and ZIP codes revealed, and 10 users had highly-protected account details exposed, though Robinhood didn’t specify what details were compromised.
After a recent update, the company acknowledged that 4,400 phone numbers appeared in a stolen dataset, which only expanded the pool of impacted individuals. The company adamantly claimed that threat actors didn’t compromise users’ Social Security numbers, bank account information, or steal any other financial data.
How did Robinhood respond?
After detecting unauthorized access, Robinhood quickly assessed the scope of the incident and began its investigation. The company confirmed that attackers compromised no financial information but still hired Mandiant to evaluate and mitigate any long-term risks. The leading cybersecurity firm confirmed there were no direct financial losses linked to the breach; however, their investigation focused on tracing how threat actors gained access.
They analyzed all affected systems, noting specific ways to strengthen Robinhood’s internal controls and prevent similar events. Robinhood notified law enforcement and sent disclosures to everyone affected by the Robinhood data leak. The company also reinforced its internal security awareness training, worked to prepare for all types of incidents, educated its team on the benefits of multifactor authentication, and improved employee access to prevent social engineering attacks.
What happened in the 2020 Robinhood account takeovers?
Before the 2021 data breach, Robinhood users dealt with another security event in October 2020, when threat actors compromised over 2,000 trading accounts after a wave of unauthorized takeovers. Many customers reported stolen or transferred funds, but the fallout concerning the company’s nonresponsive customer support was severe.
It left many victims unable to confirm the status of their accounts. For a platform managing millions of retail investor funds, this communication gap fueled widespread criticism and raised questions about how fintech companies handle security crises. On Reddit, frustrated users voiced their anger and fear.
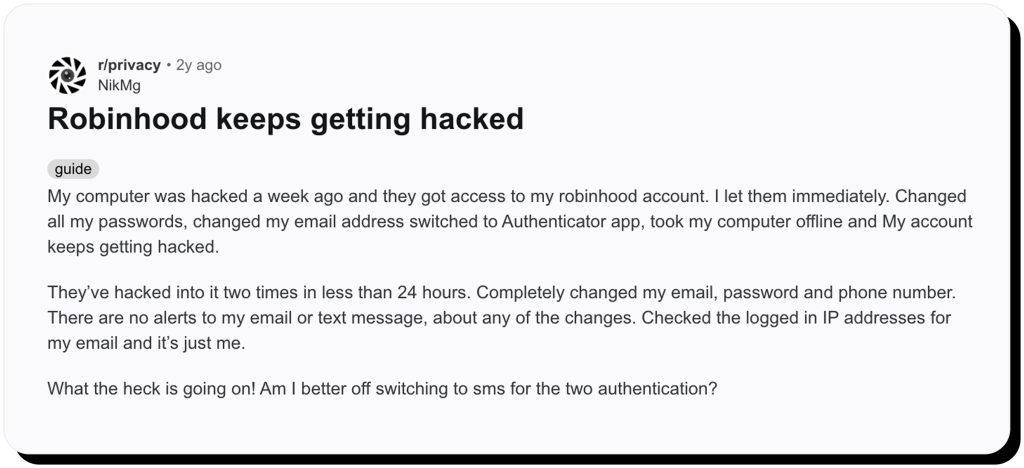
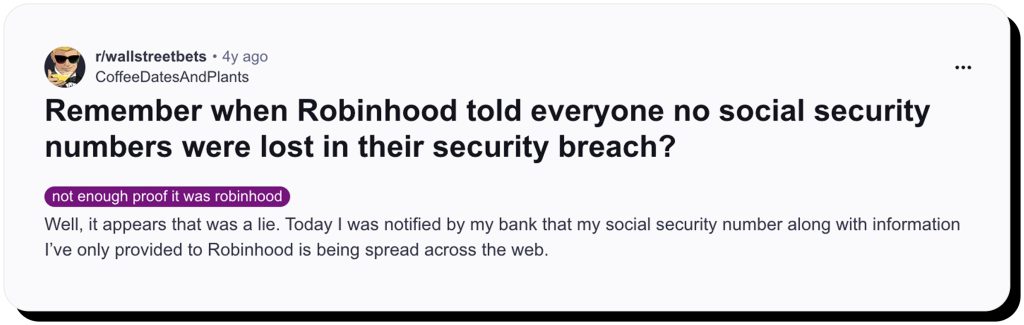
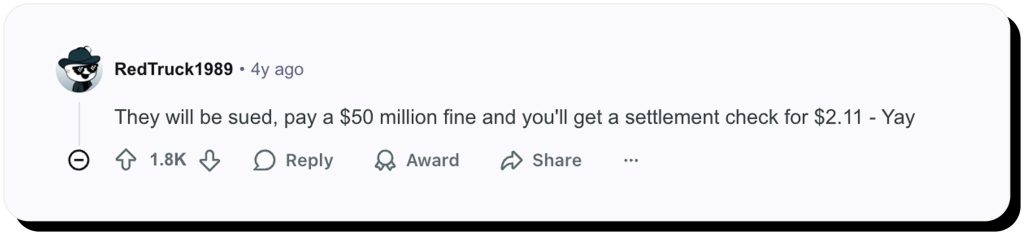
These reactions reflect how many users felt betrayed, not just by the Robinhood data leak, but by the company’s lack of transparency and class action lawsuit futility. Later, however, legal scrutiny highlighted the company’s failure to implement universal data security measures to limit the impact of cyberattacks.
To avoid further legal action, Robinhood agreed to a class-action settlement as a way to compensate all affected users.
The consequences following the Robinhood security breach
Robinhood’s repeated security incidents led to severe legal fallout, including class action lawsuits, regulatory fines, and long-term damage to its reputation. These outcomes reveal that, even when companies attempt to limit financial losses, using weak data security can lead to significant consequences.
The 2020 Robinhood data breach settlement
Last year, Robinhood agreed to pay a $20 million settlement to resolve the lawsuit filed by those affected by the account takeovers. The settlement compensation covered users affected by the Robinhood data breach between January 2020 and April 2022. This table explains the Robinhood class-action settlement in detail.
| Settlement Detail | Description |
|---|---|
| Total Settlement Amount | $20 million |
| Covered Timeframe | January 2020 – April 2022 |
| Eligible Users | The victims of account takeovers |
| Payouts | Up to $260 per claimant, plus complimentary credit monitoring services |
| Mandated Security Improvements | Supplemental two-factor authentication (2FA), password change prompts, and proactive account monitoring security to detect suspicious activity. |
The legal settlement naturally followed after the steadily growing public outcry for someone to be held accountable for data exposure incidents – a pattern often seen in similar cases, especially the Kronos data breach settlement and the Wells Fargo data breach.
The SEC fines Robinhood’s broker-dealer divisions
The U.S. Securities and Exchange Commission (SEC) fined Robinhood’s broker-dealer divisions a combined $45 million in 2025 for regulatory violations under Regulation S-P and Regulation S-ID. These regulations require firms to keep customer data secure and maintain identity theft prevention programs. Unfortunately, the violations overlapped with both breach periods, which only served to reveal Robinhood’s internal control weaknesses.
At the same time, these events also reinforced how regulators treat cybersecurity as an IT issue and as a central element of consumer protection.
Risks to watch for after the Robinhood breach and account takeovers
The Robinhood data leak provided threat actors with a foundation for target scams, impersonation schemes, and identity theft attempts. Yet, some red flags are easier to spot than others:
- Phishing messages and impersonation attempts – Cybercriminals use previously leaked information to create messages that appear legitimate and mimic Robinhood or other financial institutions. They want to trick users into handing over their login credentials. The Facebook data leak shows how threat actors weaponize exposed user data for widespread impersonation attempts.
- Credential reuse attacks – Unfortunately, many users tend to reuse passwords and other login credentials for other online accounts. When bad actors compromise credentials from one account, they gain access to more platforms. This online behavior has fueled other breaches like the PayPal data breach.
- Fraudulent tax filings and identity theft – Cybercriminals don’t need your full login credentials to commit fraud. Even when they can only steal limited PII from you, it’s still enough for identity thieves to build fraudulent profiles.
- Loss of trust in fintech safeguards – Repeated data breaches have caused many investors to question the safety of online investing platforms. The USAA data breach reflects how safety failures contribute to users losing trust in fintech applications.
What to do if your Robinhood account was hacked?
Even though Robinhood’s past breaches didn’t involve direct financial theft on a massive scale, these account takeovers may still lead to serious consequences.
Users should do this:
- Reset your password and use two-factor authentication. Change your Robinhood password to something unique. Turn on 2FA using authentication apps or security keys instead of using SMS methods, as they are vulnerable to SIM-swapping attacks.
- Do malware scans on your infected devices. If you suspect that your Robindhood account was compromised, try running a complete antivirus or anti-malware scan on the devices you used to log into your account. Infostealer malware, like those found in the Apple data leaks, can quietly capture stored passwords, cookies from your browsers, and even screenshots or user keystrokes.
- Report the incident to Robinhood and the authorities. Document everything about your experience, especially your trades and transactions, app messages, and timestamps, before reporting the incident through Robinhood’s in-app security team. After reporting the incident, immediately file a complaint with the FTC and the CFPB if your account remains compromised.
- Monitor your credit files and exposure potential. Start watching for signs of fraud on your credit reports and financial accounts. It’s best to freeze your credit file with Equifax, TransUnion, and Experian to limit the long-term damage by thieves opening fraudulent loans or new accounts in your name.
- Minimize your online footprint. The best way to gain long-term protection from cyberattacks that harm your financial future after a breach is to reduce the size of your digital footprint.
How to protect your information going forward
Once your account is secure, it’s vital to protect your information, not just on Robinhood, but on every online financial service you use. Performing each of these steps can reduce the amount of sensitive data threat actors have to use against you.
Stay alert for phishing and fake support messages
Scammers impersonate real customer service representatives using any attack vector they can to trick their targets, forcing them to share passwords, recovery codes, or payment details. Always verify the message’s origin and never send your data using unsolicited links. Exposed contact details can fuel large-scale impersonation scams.
Use strong passwords for more secure authentication
Reusing the same passwords is a bad idea. When threat actors expose one of your profiles, they can quickly compromise other online accounts too. Try using 1Password or other trusted password managers to secure your accounts.
Enable two-factor authentication features through apps like Authy or Google Authenticator. Consider using additional protection methods, like hardware keys that use FIDO2/WebAuthn standards, to prove your identity without revealing your secrets and to prevent cyberattacks. If using hardware keys, look for:
- Trusted brands and firmware transparency, including Yubico, Feitian, or GoTrust.
- Tamper-resistant designs that protect the chip against physical attacks.
- Compatibility is a necessity, and devices should work with Google, Microsoft, GitHub, and more.
Update your software and devices often
Many cyberattacks exploit reported software and device vulnerabilities. Close out your browsers often and update them when prompted. Use an online calendar with notifications or set frequent reminders to check for updates to your operating system. Check developer notes or your online app stores to ensure that your trading apps have the latest patches and updates.
Check your online accounts more frequently
Even months after a data breach, your sensitive information can resurface. You must diligently review your account statements, credit reports, and sign-in activity for anything unusual. Pay attention to any minor or unexplained changes, as they are usually early indicators of scams.
Protecting your data isn’t a one-time event; it should be an ongoing habit. Staying cautious while using the internet is the key to maintaining long-term privacy.
Remove your information from public data brokers
Cybercriminals are persistent when it comes to targeting vulnerable individuals.
They use every resource available to learn more about their intended victims — including data brokers and people-search sites — to build detailed digital profiles that can later be exploited for identity theft or convincing social engineering scams.
Onerep helps reduce your exposure and lower the risk of cybercrime by automatically scanning 230+ privacy-breaching websites and removing your personal information from them. The platform also continuously monitors your personal information for reappearance and makes sure your data stays hidden from the prying eyes.
Run a free Onerep scan to evaluate your data exposure
FAQs
Did Robinhood have a data breach?
Yes, Robinhood officially disclosed a data breach in November 2021 after a social engineering attack gave an intruder access to internal tools. The attacker exposed millions of user details, including email addresses and full names.
What happens if your Robinhood account gets hacked?
If your Robinhood account is compromised, don’t hesitate to change your password, especially if you’ve reused login credentials elsewhere. Use two-factor authentication wherever possible and contact Robinhood customer support when reporting unauthorized activity or account misuse.
What is the security issue with Robinhood?
Targeted cyberattacks revealed some weaknesses in Robinhood’s employee access controls. Attackers tricked a customer support employee into providing access, which allowed bad actors to view customer lists. Earlier incidents also proved Robinhood’s lack of “universal” safeguards that many broker-dealer platforms use.
Did Robinhood pay $45 million SEC settlement for multiple data violations?
Yes, in 2025, the SEC fined Robinhood’s broker-dealer divisions $45 million for failing to protect user data and adhere to identity theft prevention regulations (Reg. S-P and Reg. S-ID).
Will Robinhood return money if scammed?
Robinhood support will investigate fraudulent transactions, but will only reimburse customers, based on specific circumstances or if its platform was compromised. However, reimbursement isn’t guaranteed if customers lose funds because of phishing attempts or other scams.





Mikalai is a Chief Technical Officer at Onerep. With a degree in Computer Science, he headed the developer team that automated the previously manual process of removing personal information from data brokers, making Onerep the industry’s first fully automated tool to bulk-remove unauthorized profiles from the internet.