Bank of America data breach: what to know and how to avoid damaging consequences after a third-party data breach

Bank of America (BoA), the second-largest financial institution in the U.S., has faced numerous data breaches in previous years. Each of the incidents involved third-party vendors, whether as targets of cybercrime or mishandlers of paper documents. These recurring incidents emphasize the risks of using third-party service providers and highlight the fundamental flaws in the quality of BoA vendor oversight.
This article will explore the Bank of America data breach incidents, what information was compromised, and how the company handled the breaches. It will also provide expert advice and practical tips on what you can do to stay protected.
What is the Bank of America data breach: understanding the incidents
Timeline and third-party vendor vulnerability pattern
Over the years, Bank of America’s customers have suffered several data breaches that originated at BoA’s third-party service providers.
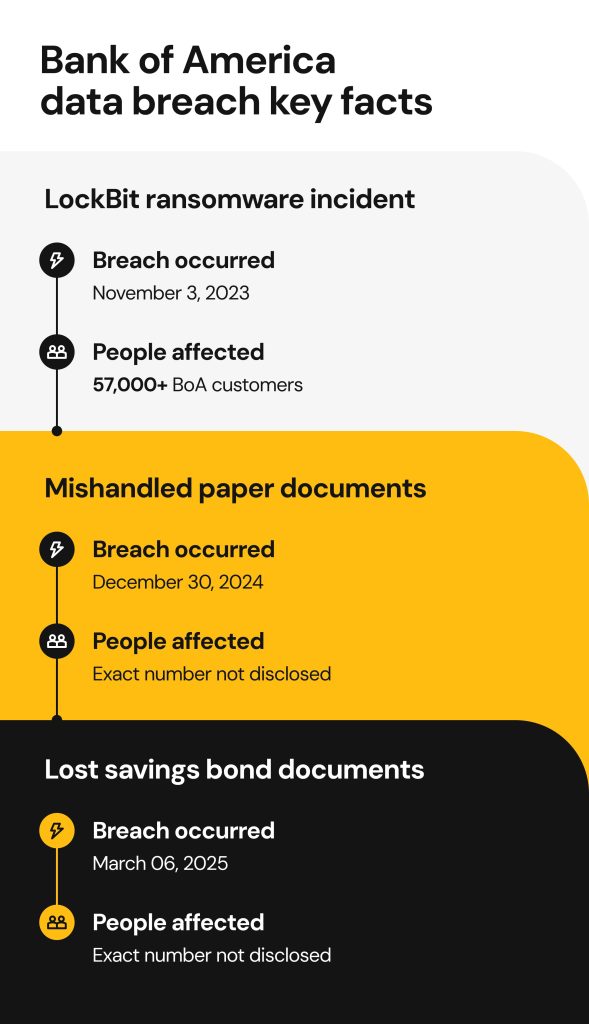
2023: The LockBit ransomware incident
On November 3, a ransomware group LockBit targeted Bank of America’s third-party service provider Infosys McCamish Systems. Personal information of 57,028 BoA clients was exposed during the breach.
Although the full extent of the incident wasn’t disclosed, the data compromised allegedly included names, street addresses, DoBs, SSNs, account information, and business emails. It’s not certain whether the hackers have exploited the data, posted it on dark web forums or otherwise misused it.
2024: Mishandled paper documents
The Bank of America data breach 2024 involved an unnamed third-party document destruction vendor who failed to secure confidential paper documents they were transporting. On December 30, the mishandled banking materials were left outside the vendor’s facilities, taken out of the secure transportation containers.
The extent of the exposure was difficult to determine. As reported, the compromised information included BoA customers’ account details and could have included customers’ names, DoBs, gender, home and business addresses, phone numbers, email addresses, SSNs, government ID numbers, as well as financial information.
The Bank of America notified a fraction of its customers whose accounts were being closely monitored. At least two clients from Massachusetts were affected by the incident. Potential breach victims were offered free Experian identity theft protection service for two years.
2025: Lost savings bond documents
In March 2025, Bank of America revealed that physical files related to the savings bonds of its customers were lost in transit. Despite the efforts to locate the lost documents, the confidential files could not be recovered.
The incident may have exposed the customers’ names, addresses, telephone numbers, SSNs, account numbers, and more.
The affected customers were offered credit monitoring free of charge.
Historical note: the 2012 incident
The long-standing problem with BoA’s third-party vendors dates back to 2012, when the institution disclosed a merchant data breach incident compromising the credit card information of its customers.
“Security for our customers is a top priority, and we take proactive steps to protect our customers from fraud,” the Bank of America spokesperson stated.
Although the exact number of affected account holders was not disclosed, the bank notified the impacted customers, blocked the compromised credit cards, and reissued new ones.
What data was exposed and who was affected in the Bank of America data breach incidents?
The data exposed across incidents included both non-sensitive and highly sensitive personally identifiable information (PII):
- Full names, home addresses, emails, and DoBs
- Social Security numbers and government-issued IDs
- Account numbers, credit card numbers, and other financial details
During the LockBit attack alone, about 57,000+ Bank of America customers were impacted. The number of people affected in other breaches remains unclear. Victims spanned multiple states, with confirmations from Massachusetts, New York, Oregon, and D.C.
Bank of America’s response: too little, too late?
Following the breaches, the Bank of America sent out notifications (see the 2025 breach notice here), and offered its potentially impacted customers two years of free identity theft protection services through Experian IdentityWorks, which included credit monitoring, dark web monitoring, and identity protection services. While BoA’s gesture acknowledged the seriousness of the incidents, many critics on social media argued that the Bank of America failed to address the core issue: third-party vendor access to customers’ private sensitive data.
Many also thought that the response to the 2023 LockBit breach was overly delayed: the Bank of America waited 90 days to start notifying the customers who may have been affected by the breach, potentially violating state laws.
Legal and reputational consequences after the Bank of America breach incidents
Free credit monitoring isn’t enough, these companies need to be sued for negligence…
Large-scale cybersecurity incidents, such as any Bank of America breach, often carry legal repercussions. Class action lawsuits were filed against Infosys McCamish Systems and other related vendors. Furthermore, the privacy claims are being investigated by Edelson Lechtzin, a national law firm specializing in class actions, and Morgan & Morgan, one of the largest personal injury law firms in the country.
The Bank of America itself hasn’t escaped criticism. While the breaches didn’t stem from its internal systems, many argue that the bank should be held accountable for choosing and overseeing vendors that failed to protect sensitive private data. The biggest complaint? Communication. Customers weren’t notified until weeks or even months after the Bank of America cyber attack, which has led to public frustration and a growing sense of distrust. On forums like Reddit, users have openly criticized the bank’s slow response and lack of transparency, some even referencing older incidents, saying this feels like “just another breach.”
Critics have demanded stronger data protection laws and real consequences for financial institutions’ negligence. One Reddit user wrote: “I don’t need another year of credit reporting and a $29 check. I need banks to be held accountable for their lack of security.”
It’s not just Bank of America: other banks under attack
Security incidents that happened at Bank of America are part of a broader trend in cybercrime. Other large financial institutions, such as Loan Depot, Truist Bank, Fidelity Investments, Mr. Cooper Group, Chase Bank, and American Express, also suffered data breaches recently.
Cybercriminals may take advantage of third-party vendors and supply chain vulnerabilities (products or services the bank uses) that often have weaker security systems, as well as insider threats (targeting employees) and social engineering scams (phishing emails and malicious phone calls). All financial institutions remain vulnerable to security incidents, regardless of how big they are.
The danger of bank breaches and third-party risks
Banks deal with highly sensitive personal and financial data, which bad actors can use to perpetrate identity theft (credit fraud, tax fraud, benefits scams), account takeover and unauthorized financial transactions, as well as sophisticated phishing campaigns.
Third-party vendors often fail to implement adequate cybersecurity measures, making them a high-stakes target for cybercrime. As the supply chain attacks and ransomware scams rise in popularity, financial institutions should prioritize vendor oversight as a top-tier security precaution. Until banks consistently enforce tighter controls, regular audits, and access limitations across their vendor networks, data breaches like the ones at BoA will likely continue, and customers will keep paying the price.
What to do if you’re a Bank of America customer
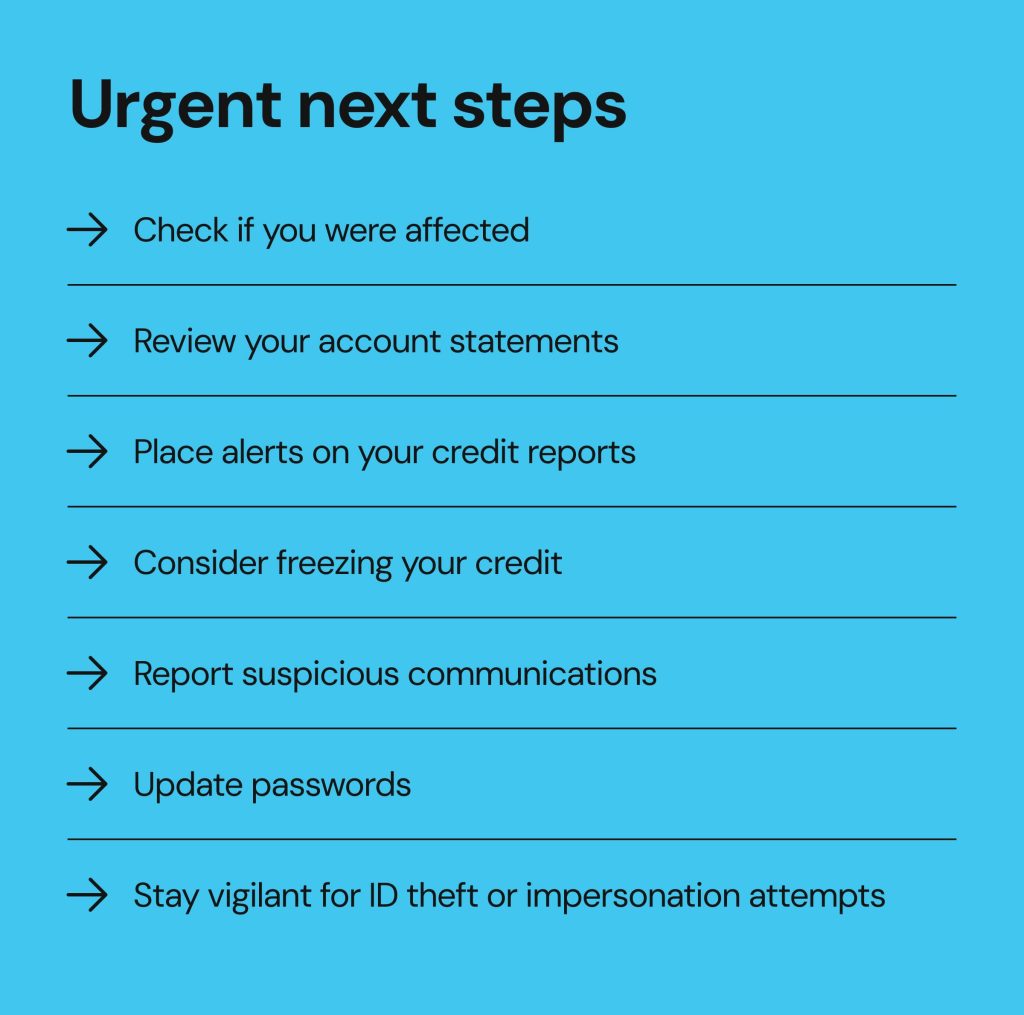
Check if you were affected
Check if you have received an official breach notification from your bank or call Bank of America customer service at 800-432-1000.
Review your account statements
Keep an eye on your bank and credit card statements for suspicious transactions. If you notice any unfamiliar charges, report them to your bank right away.
Place alerts on your credit reports
Setting up a fraud alert with the major credit bureaus is a clear indication for creditors to take the extra steps to verify your identity before approving credit or opening new accounts in your name.
Consider freezing your credit
Freezing your credit with all the major credit bureaus prevents bad actors from opening accounts or getting loans in your name. Once you want to apply for credit, you’ll have to lift the freeze.
Report suspicious communications
If you’ve experienced phishing or scam attempts, don’t forget to report it to your bank by sending an email to abuse@bankofamerica.com.
Update passwords
Make sure to create new, strong, and unique passwords for each of your accounts. Consider using a password manager for password creation and safe storage.
Stay vigilant for identity theft or impersonation attempts
Keep an eye out for signs that someone may be trying to impersonate you or steal your identity, such as messages from unknown services, unexpected bills, or denied credit.
How to prevent future risks

Don’t overshare financial info online
This might sound like a no-brainer, but people still post loads of sensitive information online. Avoid even casual mentions of your banking institution, income, or credit card usage on social media or forums.
Minimize personal information exposure
Reveal as little as possible about yourself online, including information like your full name, street address, phone number, or date of birth. These tidbits are often used in the so-called “dictionary attack”, a common password-cracking technique where bad actors collect lists of likely passwords into attack, augment them with numbers, letters or characters, and then use automated scripts to try each password on a username.
In addition, set all of your social media profiles to private so that only friends you trust have access to your posts, photos, and other information.
Finally, opting out of data brokers that collect and publish your information without your permission cuts access to the details that cybercriminals often exploit for phishing or identity theft.
You can find more tips on how to remove your information from the internet here.
FAQs
Was Bank of America hacked in 2024?
Bank of America was not hacked in 2024. Still, confidential paper documents were exposed by a third-party document destruction vendor.
How can I tell if my data was exposed in the BOA hack?
Look out for an official notification sent by your banking institution or contact their customer support service. You can also use an online breach check tool, such as haveIbeenpwned.com
What is Bank of America doing to fix the issue?
Bank of America emphasized its commitment to advancing cybersecurity, but hasn’t revealed the details of any security reforms it conducted.
Can I remove my data from broker sites if I’ve been breached?
Yes, you can manually go through data broker sites to see which ones contain your personal information and send opt-out requests to have your data taken down.




Mikalai is a Chief Technical Officer at Onerep. With a degree in Computer Science, he headed the developer team that automated the previously manual process of removing personal information from data brokers, making Onerep the industry’s first fully automated tool to bulk-remove unauthorized profiles from the internet.