X (Twitter) data breach: what happened and what you should know to protect your information

News about a Twitter data breach or a Twitter data leak has made headlines for the past few years. The reports left many people confused: were they true breaches, massive scrapes, or recycled databases?
Twitter (now X) has faced multiple security incidents between 2021 and 2025. The initial, and perhaps most impactful, was the API flaw exploitation, followed by source code exposure, insider leaks, and massive data compilations.
This article will break down the timeline of events, what was actually leaked, the risks to users, and how to check if your account is among the leaked Twitter accounts. We will also discuss how to protect yourself after an X breach.
Twitter is now called X: understanding the context
As we analyze Twitter/X security incidents, let’s start by understanding the platform’s identity. Twitter, started in 2006, quickly became the go-to social network for discussions, social and political movements, and quick news sharing.
Elon Musk purchased the platform in October 2022. Less than a year later, Twitter underwent a complete rebrand. The name, blue color, and familiar bird logo were gone, and Twitter officially became X. Also, Musk cut down the workforce by about 80%.
Reporters and forums use “Twitter,” “X,” and “Twitter leak/X breach” interchangeably for the same historical incidents, regardless of whether they happened before or after the rebrand. In this article, we’ll use “Twitter/X” to reflect continuity across years and systems.
A brief history of X (Twitter) data breach incidents: 2021-2025 in focus
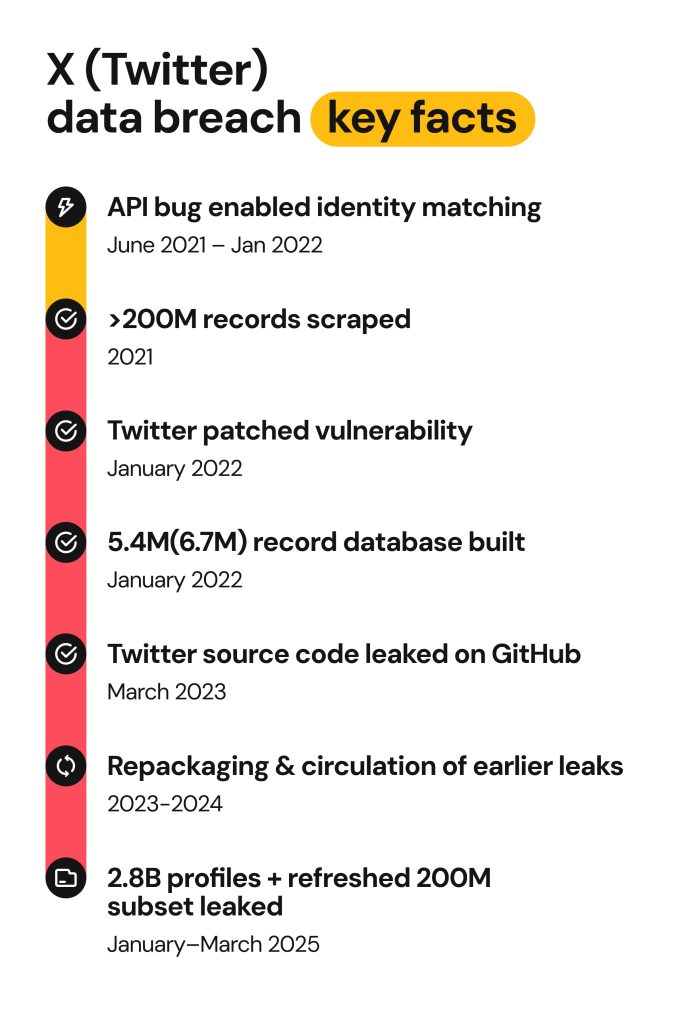
2021–2022: API bug enables identity matching
Back in June 2021, Twitter/X made changes to its source code. The modification caused an API error that allowed anyone to look up Twitter/X accounts using an email or phone number.
How was that possible? An API (short for Application Programming Interface) allows software to communicate with each other, and look up users or tweets in bulk, for instance. The catch is that the retrieved information, normally, is publicly available.
Twitter/X wasn’t aware of the issue until a researcher reported it as part of a Bug Bounty Program in January 2022.
Twitter/X quickly patched the API vulnerability. At that time, it wasn’t clear whether someone had already taken advantage of the bug. Then, in July 2022, a news report revealed 5.4M to 6.7M records linking emails/phones to Twitter/X accounts. The company issued a public statement about the incident in August 2022.
Late 2022–Jan 2023: 400M claims, 200M verified dataset
In late 2022, an alleged dataset of approximately 400 million Twitter/X accounts emerged for sale on the dark web. Expert analysts found it to contain a lot of duplicates. Still, about 200 million records were verified as real.
The dataset contained email addresses linked to Twitter/X accounts and public profile information, such as usernames, bios, and follower counts. There were no passwords.
Based on the type of exposed info, Twitter/X maintained that this wasn’t a fresh security breach. What’s more likely is that somebody compiled the information from older data leaks and the data scraped using the API bug.
March 2023: Twitter source code leak on GitHub
In March 2023, a part of Twitter/X’s source code was posted on GitHub by a user called “FreeSpeechEnthusiast”.
According to experts, this incident was likely carried out by an insider who had access to Twitter/X’s source code, or an ex-employee who had been laid off after management changes.
Since source code falls under Twitter/X’s intellectual property, the company filed a DMCA (Digital Millennium Copyright Act) takedown notice. GitHub was legally required to take down the code, and they disabled the repository where it had been posted.
Twitter/X didn’t stop there. They issued a subpoena to GitHub, requesting information that can be used to reveal the identity of the user, including their contact information, IP addresses, and login data. GitHub was forced to comply with their requests.
2023–2024: circulation and repackaging of earlier leaks
In 2023 and 2024, bad actors kept repacking and recycling Twitter/X account information and selling it on the dark web.
On December 4, 2023, a 59 GB RAR archive containing over 200 million records emerged for sale on a hacking forum. Most of the information was traced back to the 2022 API flaw incident. The information included email addresses, phone numbers, usernames, screen names, follower counts, and other public profile data.
Jan–Mar 2025: “2.8B profiles” compilation + refreshed 200M subset
In early 2025, a user going by the handle “ThinkingOne” posted a massive 400 GB dataset on a hacking marketplace, BreachForums. The dataset contained information on approximately 2.8 billion Twitter/X user profiles.
The catch is that the number of active Twitter/X users is much smaller: just between 335 and 600 million. So, the dataset likely included old profiles and bots. Nevertheless, the records contained user IDs, screen names, account creation dates, follower counts, tweet histories, and other metadata.
Within those 2.8 billion records, researchers discovered a more significant 200 million dataset. These records linked the previously leaked emails and phone numbers with fresh, up-to-date account activity metadata from 2025.
The origin of the compilation is not clear. Some experts assume it’s yet another scraping and aggregation dataset, while others think it was an insider leak. It might also be a mix of both: old recycled data combined with a fresh leak.
What data was exposed in the 2021 – 2025 X (Twitter) data leak incidents
The root cause of Twitter data leaks was the API bug from 2021. This incident exposed internal Twitter data used to deanonymize profiles, which was later recycled and repackaged.
Exposure of the Twitter/X source code was no less of a concern. It enables cybercriminals to create custom attack vectors. Still, no user PII was exposed during this incident.
The 2.8 billion Twitter leak mainly involved profile metadata compilations, without PII. The massive number was also inflated by inactive accounts and bots. But, within the dataset was also fresh account metadata connected to the emails and phone numbers exposed in the API flaw incident.
| Security incident | Exposed data |
|---|---|
| 2021-2022: API flaw exploit | Emails, phone numbers, Twitter/X account usernames |
| 2022-2023: 200M dataset | Emails, phone numbers, Twitter/X account usernames |
| 2023: Github leak | Twitter/X source code |
| 2023-2024: recycled datasets | Emails, phone numbers, Twitter/X account usernames, locations, follower counts, tweet histories |
| 2025: 2.8B Twitter leak | Twitter/X usernames and user IDs, location data200 million detailed user profiles + user names and email addresses. |
Reactions to the Twitter data incidents
Did X do well in response?
Twitter/X handled some security incidents better than others.
- Twitter/X acknowledged the API flaw incident in August 2022, after the 200 million data set resurfaced on the dark web a month earlier. There was no way of telling who’s all been affected, so the platform issued a public statement. They ran an investigation and patched the bug immediately.
- Later on, multiple mega dumps were downplayed. Even when massive compilations appeared on hacking forums, Twitter/X maintained that they were recycled, old, and public data. Surely they wanted to calm down users and assure them of no new breaches, but the repetitive claims raised some concerns.
Experts point out that Twitter/X could have done a better job at communication. For example, when the 2.8 billion record dataset emerged, researchers debated whether it was an insider leak or an aggregation of scraped data. Twitter/X’s statements did little to resolve the uncertainty.
Public fallout: what did users say?
Wait, 2.8 billion. Does it mean the deleted accounts were never deleted?
Many users were skeptical of the 2.8B figure, wondering if historical data can ever be truly removed from Twitter/X.
Others were wondering what really happened in 2025: if a disgruntled employee stole the data before mass Musk layoffs, or if the data was scraped. Regardless of the incident background, the public is growing increasingly frustrated with Musk-era security practices and blames the layoffs for poor cybersecurity.
The leak of the structured datasets makes it easier to link Twitter/X usernames to real identities. This idea for deanonymization was especially concerning for activists, journalists, and those who use pseudonymous accounts and rely on anonymity for safety.
X data leak: what are the risks for you?
Data leaks carry inherent risks, but Twitter/X leaks come with a few specifics.
- Deanonymization. Your pseudonymous account can be traced back to you if your personal email is linked.
- Phishing & spear phishing. Knowing your email and Twitter/X account metadata allows fraudsters to orchestrate more convincing scams.
- Credential stuffing. An exposed email can be tested with old passwords on other platforms.
- Harassment & doxxing. Loss of anonymity can make you a target.
- Systemic risk from code leaks. A leaked source code can expose system vulnerabilities that enable broader attacks.

How to check if your X account was leaked
If you suspect that your X account was leaked, it’s worth investigating. Use a breach notification service, such as Have I Been Pwned, to see if your email address was leaked in a known data breach. Don’t use low-trust “breach checkers” that ask you to input personal information or your X credentials.
Next, check your recent sign-in activity on X and third-party app access. If you notice any unfamiliar devices and apps, be sure to remove them. If there are any signs of exposure, update your password too.
What to do if your Twitter data was compromised
Here are the steps to take to secure your Twitter/X account.
- Change your X password. Use a unique, long, random passphrase. You don’t have to think of it by yourself; use a password manager to generate and store it.
- Enable 2FA via authenticator or hardware key. Use an authenticator app to generate login codes, or opt for a hardware key. Don’t receive codes via SMS, since fraudsters can hijack your phone number as well.
- Revoke unrecognized app access. When did you last check your device logins? Head over to your settings and remove any devices you don’t recognize.
- Tighten privacy settings. It’s best to remove your location, have no links in your bio, and minimize your profile fields. The less personal information you share, the better.
- Stay alert for phishing emails tied to your handle. A likely aftermath of a Twitter data breach is an increase in phishing attacks. Before you click on links or download attachments, make sure to verify the sender’s domain.
- Update reused credentials across services. If you’ve used the same password for your banking app, email, or other critical accounts, change it immediately. Even better, create a new password for each account and never reuse them.
- Consider credit monitoring/fraud alerts. If you’ve had your sensitive PII (SSN, financial data) exposed in another data breach, consider placing a fraud alert or applying for credit monitoring services.
- Be careful if you operate a pseudonymous account. For safety purposes, consider removing public contact points (like websites or other links) and re-evaluate your operational security. Generate a separate email and don’t use your personal device for logging into this account.

How Onerep can help reduce your online exposure
Publicly available data on people-search and data broker sites can be exploited to enrich leaked profiles. Bad actors may already have your email address and Twitter handle, but want to know where you live and what services you subscribe to. Combining personal public data with breach records allows them to create more successful phishing and social engineering scams, impersonate you, and even commit identity theft.
Onerep locates and removes your public listings from over 200 people-search and data-broker sites. We keep monitoring these sites for new exposure. This brings down the amount of third-party information that attackers can use to profile and target you.
The real benefit of reducing your online exposure is not just enhanced safety and privacy, but having peace of mind after an X breach or any other security incident that comes up.
👉Start a free 5-day trial with Onerep
FAQ about the X (Twitter) breach
Was there a cyber attack on X?
Twitter/X’s internal systems have not been under cyberattack. In 2021, Twitter developers changed the source code and triggered an API bug. This vulnerability was exploited by bad actors, who breached Twitter’s internal systems, but there was never an actual cyberattack.
What’s the difference between a Twitter data breach and a Twitter data leak?
A data breach suggests that bad actors broke into Twitter/X’s systems by exploiting a bug or hacking internal servers. For example, in the 2021 API flaw, fraudsters took advantage of a code vulnerability to match emails and phone numbers to Twitter accounts.
A data leak happens when data is exposed without hacking into core systems. This encompasses publicly visible information that is scraped (collected at scale) or old data that is repackaged. For example, the 2025 dump of 2.8 Twitter accounts is likely just a leak of scraped public info.
Why is my Twitter getting hacked?
There could be many reasons. Perhaps your account username and handle were leaked in one of the security incidents, you tend to reuse passwords, or you revealed your credentials to a scammer in a targeted phishing attack.
What happens if my X account gets hacked?
If someone takes over your X account, you might notice various telltale signs. Fraudsters may send spam, cryptocurrency ads, or phishing links to your followers. They could impersonate you or spread misinformation. Sometimes, they will change your password and email to lock you out of your account.
Read more:
Facebook data leak: what happened and how to safeguard your information
LinkedIn breach: what we know and how to protect your account
Instagram scams in 2025: how to identify, avoid and fight back
Telegram scams: how to stay safe on the messaging app
WhatsApp scams: what you need to know





Mikalai is a Chief Technical Officer at Onerep. With a degree in Computer Science, he headed the developer team that automated the previously manual process of removing personal information from data brokers, making Onerep the industry’s first fully automated tool to bulk-remove unauthorized profiles from the internet.