T-Mobile breach: what you need to know to stay protected

T-Mobile, the second-largest wireless carrier in the U.S., suffered multiple data breaches in the past decade, exposing the personal information of tens of millions of people. These incidents highlighted deep-rooted weaknesses in the company’s cybersecurity practices. Among them, the 2021 T-Mobile breach was the most severe, affecting over 76.6 million individuals and triggering class action lawsuits, regulatory investigations, and major enforcement actions.
This article will break down the timeline of events, exposed data types, and the legal and financial fallout for T-Mobile, including lawsuits, government penalties, and required reforms. We’ll also walk you through practical steps to protect yourself if you were affected.
Overview of the past T-Mobile breach incidents (2015–2020)
Did T-Mobile have a data breach? Not again! Unfortunately, the company has built a solid reputation for data breaches.
Here is a quick overview:
- October 2015: Bad actors breached Experian systems and compromised the sensitive data of approximately 15 million T-Mobile customers. Experian notified the affected customers and offered free credit monitoring services.
- August 2018: Cybercriminals exploited an API (allows two software systems to exchange information) vulnerability. The incident compromised sensitive information of about 3 million T-Mobile users. T-Mobile notified customers without delay and recommended regular password changes.
- November 2019: Fraudsters gained access to sensitive information of over 1 million prepaid T-Mobile customers. The details about the cyberattack were never disclosed. T-Mobile took swift action to remedy its systems and notified the affected users.
- March 2020: Bad actors hacked a T-Mobile employee’s email account, exposing the sensitive information of an undisclosed number of customers.
- December 2020: Cybercriminals accessed the sensitive information of approximately 200,000 T-Mobile customers. The details of the breach weren’t disclosed.
Although these earlier breaches impacted a considerable number of T-Mobile users, they were less severe in scale compared to the 2021 incident and a subsequent major breach in 2023.
August 2021 breach: the largest incident

In the summer of 2021, a bad actor used brute force on an unprotected General Packet Radio Service (GPRS) gateway to access T-Mobile’s internal systems and compromise the sensitive information of approximately 76.6 million people.
According to T-Mobile, cybercriminals have likely had prior knowledge of T-Mobile’s network structure. They accessed the company’s testing environment, which is a practice version of T-Mobile’s systems, that might have been less protected than the real one.
After locating an unprotected GPRS gateway, which is a mobile data technology used to connect mobile networks to the internet, bad actors tried numerous passwords or credentials until something worked. This hacking technique is also known as brute force, and it was used to get into the T-Mobile systems, where sensitive customer data was stored.
Hackers kept exfiltrating confidential information between March and August 2021, until an outsider informed T-Mobile about their customers’ data being sold on the dark web. A cybercriminal, John Erin Binns, came forward to take credit for the breach.
Exposed data and affected groups
The T-Mobile data breach 2021 exposed a wide range of sensitive customer information.
- Personally identifiable information (PII) such as names, home addresses, and dates of birth
- Government identifiable information: Social Security numbers (SSNs), driver’s license or ID numbers
- Technical information: T-Mobile account PINs, IMEI, and IMSI numbers, linked to individual mobile devices and SIM cards.
The breach affected the current T-Mobile customers, as well as former and prospective customers, including people who had applied for credit with the company but never became active users. A smaller number of business accounts were also compromised.
T-Mobile’s response
Attacks like this are on the rise and bad actors work day-in and day-out to find new avenues to attack our systems and exploit them. We spend lots of time and effort to try to stay a step ahead of them, but we didn’t live up to the expectations we have for ourselves to protect our customers. Knowing that we failed to prevent this exposure is one of the hardest parts of this event. On behalf of everyone at Team Magenta, I want to say we are truly sorry.
After learning about the breach, T-Mobile launched an internal investigation to identify the specific vulnerabilities. They also brought in external cybersecurity experts, including Mandiant and KPMG LLP, to help assess the damage and improve its security systems.
Mandiant focused on tracking the attackers and analyzing how they gained access, while KPMG was tasked with reviewing and strengthening T-Mobile’s overall cybersecurity practices.
Although the company stated that it couldn’t share too much information due to security concerns, they revealed that the entry and exit points used by the hackers had been closed.
2021: another breach
A few months after the massive 2021 incident, T-Mobile suffered a minor data breach that involved SIM swapping, a scam in which cybercriminals hijack your SIM by tricking mobile providers into reassigning your phone number to a card they control, in order to receive your texts, two-factor authentication (2FA) codes, and phone calls.
The company promptly informed a small number of customers and claimed to have resolved the issue.
T-Mobile breach incidents in 2023
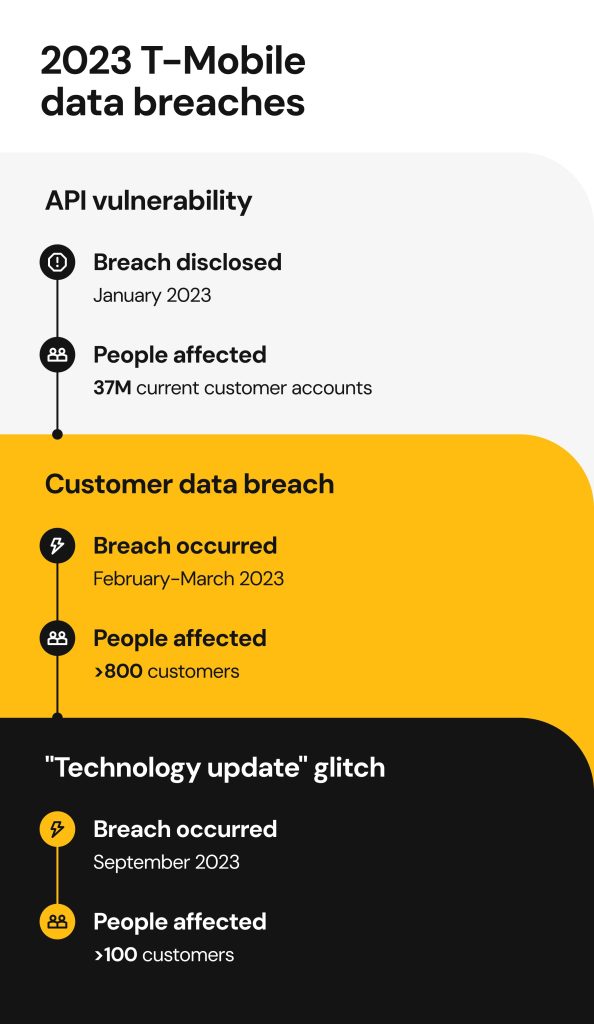
January 2023 breach
A bad actor exploited an API vulnerability to access the sensitive information of about 37 million prepaid and postpaid users, T-Mobile revealed in an 8K filing with the U.S. Securities and Exchange Commission.
The incident took place in November 2022, but the mobile carrier discovered the malicious activity on January 5, 2023. It was contained within 24 hours, and the affected users were promptly notified.
Compromised information included names, billing addresses, phone numbers, and emails. T-Mobile stated that the customers’ passwords/PINS, financial data, and government-identifiable information were not part of the breach.
February-March 2023 breach
Starting late February 2023, bad actors obtained access to the T-Mobile systems, which led to the sensitive information exposure of approximately 836 individuals. Although the incident affected a smaller number of people, it compromised highly sensitive user data, including SSNs, government-issued ID numbers, and T-Mobile account PINs. All the affected customers were promptly notified.
September 2023:
In September 2023, T-Mobile got caught up in two security incidents. Firstly, a glitch in the T-Mobile app led to confidential information of some T-Mobile customers being displayed to other app users.
The issue exposed the personal and financial data of fewer than 100 people, including phone numbers and billing addresses. The company revealed that the glitch was connected to an overnight technology update and was quickly resolved.
Not long after, sensitive information of T-Mobile employees and a small number of users was allegedly compromised in a third-party breach. The incident was likely related to an April data breach of a T-Mobile retailer, Connectivity Source. On September 21, 89 GB of data was posted on a dark web forum. The file contained personal and financial information, such as email addresses and partial SSNs.
Legal consequences and settlements after the T-Mobile breach incidents
$350 million class action lawsuit and settlement
A class action lawsuit against T-Mobile was filed in the U.S. District Court for the Western District of Missouri following the 2021 data breach. The lawsuit claimed that T-Mobile failed to properly protect customers’ data, didn’t have adequate security measures, and acted negligently, putting people at risk of identity theft and financial loss.
T-Mobile denied any wrongdoing but chose to settle the lawsuit. The company agreed to a $500 million settlement: $350 million directed to 76.6 million eligible Americans, and $150 million used to upgrade its cybersecurity systems.
Here is a timeline of the settlement case:
| Milestone | Date |
|---|---|
| Preliminary settlement approval | July 26, 2022 |
| Final deadline to submit a claim | January 23, 2023 |
| Final approval of the settlement | June 29, 2023 |
| Settlement distribution onset | May 30, 2025 |
Please note that all claims under this settlement should have been filed by/on January 23, 2023. No new claims are accepted after the deadline.
Eligible class action members were entitled to the following benefits:
- Reimbursement for documented out-of-pocket expenses and lost time: up to $25,000, including $25 per lost hour, for up to 15 hours.
- Alternative cash payment as an alternative to reimbursement for out-of-pocket expenses and lost time: $25 or $100 if you resided in California on August 1, 2021.
- Two years of identity defense services free of charge.
- Fraud resolution for all settlement class members.
FCC enforcement and $31.5 million settlement
The massive data breaches that happened within several years, as well as plenty of affected individuals and poor cybersecurity practices, led to another legal action against the telecom company, this time initiated by the Federal Communications Commission (FCC). In September 2024, T-Mobile reached a settlement to resolve the FCC’s probe into the T-Mobile data breaches of 2021 – 2023.
As a result, T-Mobile agreed to pay a $15.75 million civil fine to the U.S. Treasury and make a $15.75 million cybersecurity investment in its systems. The mobile carrier also had to adopt zero-trust architecture and make overall improvements to its cybersecurity program.
This settlement is part of a broader push by the FCC to reform privacy and protection of personal data in the telecommunications industry, signaling stricter accountability and higher standards for telecom providers moving forward.
Washington State Attorney General lawsuit
In January 2025, Washington State Attorney General Bob Ferguson filed a lawsuit against T-Mobile under the Washington Consumer Protection Act.
The lawsuit claimed that T-Mobile failed to improve the cybersecurity weaknesses it was aware of, which led to the 2021 breach, and alleged that the company’s breach notifications were misleading. Over 2 million Washington residents were affected by the T-Mobile breach, and for 183,000 of them, Social Security numbers were exposed.
The lawsuit, still active, aims to hold T-Mobile accountable by seeking civil penalties, financial restitution for affected Washingtonians, and court-ordered reforms. These reforms would include improving the company’s cybersecurity policies, enhancing customer communications in case of future breach incidents, and ensuring more transparent and effective protection under state consumer laws.
Is your data at risk after the T-Mobile breach?
Find out if you were affected
You can use HaveIBeenPwned.com, a free tool that shows whether your email or phone number appeared in data breaches, to check whether you’ve been affected by any of the T-Mobile security incidents.
If you were a T-Mobile customer during the time of the breach, you can visit T-MobileSettlement.com to check if you’re eligible for compensation or free identity theft protection service.
What to do if you were impacted in the T-Mobile or similar telecom breaches

- Freeze your credit at the three credit reporting agencies and the National Consumer Telecom and Utilities Exchange (NCTUE). A credit freeze protects you from someone using your identity to obtain loans or make large purchases. It’s free, doesn’t affect your credit score, and you can unfreeze it anytime. To place a security freeze, follow the instructions on Equifax, TransUnion, and Experian. Freezing your credit with NCTUE can be done online or by calling them at 866-349-5355. If you do so, scammers won’t be able to open a new cell phone account using your name.
- Change your mobile account PINs: Update your T-Mobile (or other carrier) account PINs immediately to prevent SIM swap attacks. Make your new PINs strong and unique, and don’t use easily guessed numbers such as your birthday or other simple patterns.
- Run a full credit check: Use AnnualCreditReport.com to get a free credit report from the three credit reporting agencies. Review each report carefully for accurate personal details and confirm that all listed accounts are legitimate and authorized.
- Review your financial statements: Go through your recent bank and credit card activity line by line. Look for any unauthorized charges, new accounts, or purchases you don’t recognize.
- Consider credit monitoring services: If your SSN or financial data were exposed, credit monitoring can promptly inform you of possible identity theft, such as opening accounts in your name or accessing financial services.
- Monitor for scams and identity fraud: Stay alert for phishing emails, strange phone calls, or unexpected bills. Identity thieves may try to use your data weeks or months after a breach.
- Dispute fraudulent activity: If you find any inconsistencies and signs of fraud, send written dispute letters to each credit bureau.
- Report id theft and fraud: File a police report, as well as report the theft to the FTC at identitytheft.gov and to your state’s Attorney General.
- Close affected accounts: Contact your banks, credit card providers, or lenders right away. If an account was opened or changed without your permission, request to close or secure it immediately.
- Document everything: Keep detailed records of every step you take. Save all original documents like police reports and dispute letters.
How to protect your personal data going forward

- Set strong, unique PINs for your mobile accounts: Your mobile account PIN is often the first line of defense against SIM swapping and unauthorized access. Choose a PIN that is hard to guess and not reused across other accounts. Consider changing it regularly and storing it securely using a password manager.
- Use authenticator apps instead of SMS for 2FA: SMS-based 2FA can be intercepted if your number is stolen or ported via a SIM swap. Instead, use an authenticator app like Google Authenticator or Authy. These apps generate secure, time-based codes that are tied to your physical device.
- Regularly review account activity and enable fraud alerts: Make it a habit to check your bank, credit card, and mobile account activity for unusual transactions or login attempts.
- Minimize your digital footprint: The less personal information you share online, the harder it is for hackers to exploit you. Limit what you post publicly, delete old or unused online accounts, and avoid oversharing details like your address, phone number, or full birthdate. Consider using aliases or separate email addresses for different types of accounts to add another layer of privacy.
FAQs
Did T-Mobile really get hacked in 2021?
Yes, the company was hacked in August 2021 by a hacker named John Erin Binns, who used brute force to breach an unprotected GPRS gateway.
Is it safe to stay with T-Mobile?
T-Mobile took steps to enhance its cybersecurity measures. As part of a 2021 data breach settlement, the company invested an additional $150 million in improving its data security infrastructure. It was also ordered to take additional cybersecurity measures as part of the FCC enforcement. Still, T-Mobile has a long history of data breaches that might make some customers uncomfortable staying with them.
What compensation was offered to affected users?
T-Mobile agreed to a $350 million settlement to compensate customers affected by the 2021 data breach. Eligible individuals could receive $25,000 for documented out-of-pocket losses and lost time, or $25 to $100 as a flat payment, depending on state residency for those without documented losses.





Mikalai is a Chief Technical Officer at Onerep. With a degree in Computer Science, he headed the developer team that automated the previously manual process of removing personal information from data brokers, making Onerep the industry’s first fully automated tool to bulk-remove unauthorized profiles from the internet.