LastPass breach: timeline, history, and how to safeguard your data

Imagine handing over the keys to every website and account you use—banking, email, health, online shopping and ticketing apps. That’s what’s at stake when a password manager is breached.
LastPass, a popular password manager, stores sensitive credentials for over 33M+ individual users and 100K+ businesses. When it was breached in 2022, it exposed just how high the risks are when platforms designed to safeguard our data get attacked.
Using advanced techniques, hackers infiltrated LastPass systems and operated undetected for months. They ultimately stole both encrypted vault backups and unencrypted personal data, thus revealing critical weaknesses in the most trusted security tools.
In this article, we’ll walk through the LastPass breach timeline, hacking techniques used, data types exposed, and the company’s response. You’ll also learn how to protect your information and trim down future risks.
LastPass breach timeline: how it all happened
This breach was elaborate and lengthy. In his communication with users, LastPass CEO Karim Toubba refers to it as “Incident 1” (August 8 to 12) and “Incident 2” (August 12 to October 26), with the second phase building on access gained during the first.

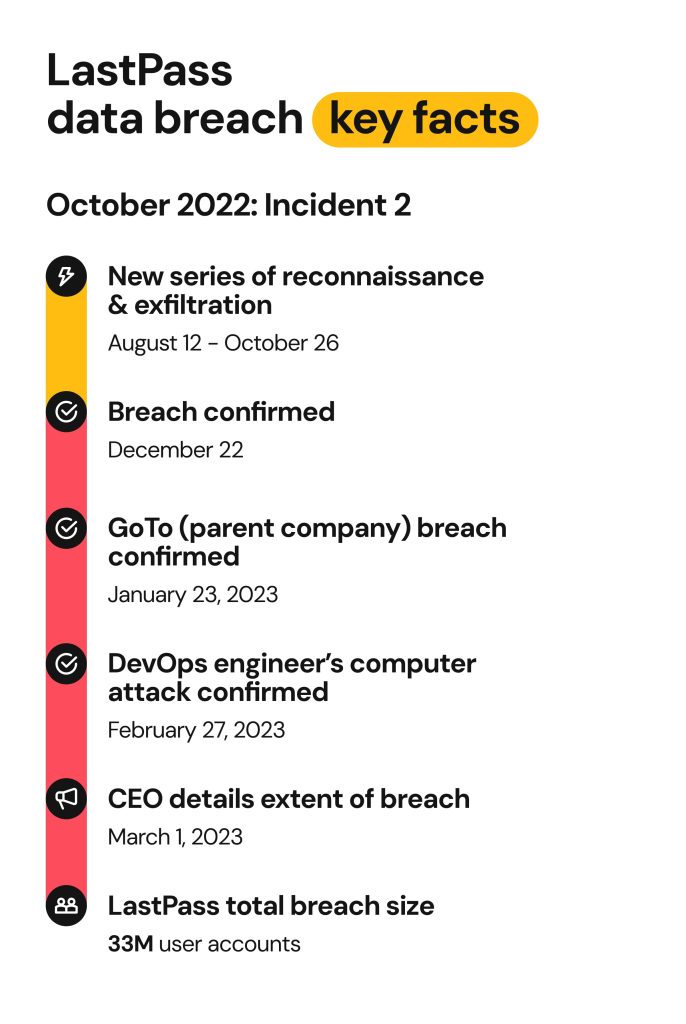
Here is the full LastPass breach timeline, start to finish:
August 2022: Initial breach
On August 8, a hacker broke into a LastPass software engineer’s work laptop. They found a vulnerability in a third-party software and used it to insert a keylogger malware. As the name suggests, this malware logs everything typed on the keyboard without the user knowing.
The software engineer was one of four who had access to LastPass cloud storage service decryption keys. When the employee entered their master password and completed multifactor authentication (MFA), the hacker captured the credentials and accessed the employee’s LastPass vault. Next, they got into the development environment, which is where LastPass creates and tests new features.
Once in this environment, bad actors could access the source code, technical documents, and system secrets. Since the development system was still tied to the production system, where user info is stored, fraudsters also stole 14 code files, also known as repositories. These files contained sensitive information such as plain text login credentials, digital certifications, and encrypted system passwords.
On August 12, LastPass noticed that something was going on.
Between August 13 and 14, hackers managed to get a copy of LastPass’s customer database. The file contained non-protected account information, associated metadata, and application configuration options such as multifactor authentication (MFA).
Around the same time, LastPass started collaborating with the incident response firm Mandiant. They kicked off an investigation and notified law enforcement.
On August 25, LastPass thought the incident was resolved. They reported no signs of ongoing malicious activity.
September 2022: Data exfiltration
Between September 8 and 22, the threat actor still had access to the LastPass database.
Within this time, they downloaded large chunks of backup data called BLOBs (binary large objects). Five files were extracted, and each backup belonged to a different day: August 20, 30, 31, and September 8 and 16.
On September 15, LastPass claimed no customer data was compromised. They also said the attack lasted only 4 days.
October–November 2022: Undetected activity resumes
After the initial data theft in September, hackers were still in the LastPass system. On October 26, they were searching and mapping out an AWS S3 bucket, which is a process known as “reconnaissance”. They looked for new files, buckets, credentials, and sensitive information they could use. It’s not clear whether they actually stole something at that point.
LastPass said they didn’t find signs of data exfiltration after September 22. They also revealed hackers weren’t present in their systems after October 26.
On November 30, the company finally admitted that customer data was exposed.
December 2022: Vault data confirmed stolen
On December 22, LastPass confirmed that full vault backups were stolen in the attack. These files contained protected and unprotected data. Almost all the customer info was compromised, except for user master passwords, which LastPass doesn’t collect.
The company warned its customers about phishing, credential stuffing, and brute force attacks.
Phishing is a form of social engineering you’re likely familiar with. Credential stuffing involves using stolen credentials on other websites, hoping they’ve been reused. Brute force involves trying random credentials (at an incredible rate), hoping to get it right.
January–March 2023: DevOps compromise and CEO apology
Since our December 22nd post, I have spoken to many of our business and consumer customers. I acknowledge our customers’ frustration with our inability to communicate more immediately, more clearly, and more comprehensively throughout this event. I accept the criticism and take full responsibility.
On January 23, 2023, GoTo, the parent company of LastPass who they share the same storage vault with, revealed that their encrypted backups and an encryption key were also compromised.
On February 27, LastPass found that Incidents 1 and 2 were connected. “While proximal in terms of timeline, it was not initially obvious that the two incidents were directly related”, LastPass said.
On March 1, CEO Karim Toubba issued a public apology and revealed more details about the LastPass data breach.
“The identity of the threat actor and their motivation remains unknown. There has been no contact or demands made, and there has been no detected credible underground activity indicating that the threat actor is actively engaged in marketing or selling any information obtained during either incident,” Toubba wrote.
What data was exposed in the LastPass breach?
The LastPass breach exposed a bunch of user information (virtually all) as well as some business information that might hurt the company in the long run.
| Data Type | Encrypted? | Exposed In | Risk Level |
|---|---|---|---|
| Vault contents (passwords, usernames, secure notes) | Yes | Sept 2022 (BLOB backups) | High |
| Website URLs stored in vaults | No | Sept 2022 (metadata) | Medium |
| Email addresses | No | Sept 2022 (metadata) | Medium |
| IP addresses | No | Sept 2022 (metadata) | Low |
| Billing information | No | Sept 2022 (metadata) | Medium |
| MFA-related entries (TOTP seeds, rOTPs, K2 keys) | Partially | Possibly Oct 2022 (S3) | High |
| Developer credentials (API keys, certificates) | Mixed | Aug & Oct 2022 (Dev systems) | High |
| Internal technical documentation | No | Aug & Oct 2022 | Low |
LastPass’s response and security upgrades
LastPass did what all companies do when faced with a data breach: launched an investigation, notified law enforcement, and tried to contain the incident. But things didn’t go so smoothly.
Let’s take a look back at LastPass’s breach history.
- The attack started on August 8, 2022, and lasted until October 26, 2022.
- The company noticed malicious activity on August 12.
- On August 25, LastPass stated there was no ongoing malicious activity.
- On September 15, LastPass claimed no customer data was affected, and the attack lasted for just 4 days.
- On November 30, LastPass admitted that customer data was affected in the incident.
- On March 1, the LastPass CEO issued a public statement.
Much of a delay? The CEO blamed it on the ongoing investigation, but users felt transparency wasn’t a priority.
“I left after the news in February (?) about how the hack happened. For me it was a combination of lost trust, the stunningly lax security practices revealed, the lack of any substantive support, the lack of any meaningful apology, and the lack of any verifiable promises to clean up their act. In the months since, it sounds like their stability and customer service have really declined,” an ex-LastPass user wrote on Reddit.
How did LastPass upgrade its security?
Here is how the company plans to prevent similar attacks from happening in the future.
- Rebuilt environments. Now, the development and production environments are separate. This means that no user information can be stolen from the development part of the system. The restructuring also helped make sure the systems were protected and free from bad actors.
- Identity Access Management (IAM). The company implemented stricter policies about who can access what.
- Rotation of credentials. Needless to say, all login credentials were changed, and they continue to change on a regular basis.
- New EDR, SASE, and CSPM tools. LastPass invested in some new cybersecurity tools. These monitor and protect their cloud environment and user devices, and secure remote connections.
Why the breach matters: risks to users and systems
The incident was an unusual one. It lasted for approximately 3 months, which shows poor cybersecurity on LastPass’s end. It also means that cybercriminals had plenty of time to roam around LastPass systems and exfiltrate a massive amount of user data.
Another aspect of this incident was specific: LastPass used MFA, but it failed. If you’ve read any of our previous data breach articles, you know MFA is one of the best personal cybersecurity measures. How was LastPass hacked, then? The truth is, endpoint security is just as important as strong login protections. Each device (endpoint) should be updated regularly and protected with a trusted antivirus software, in combination with other measures.
The LastPass breach had some real-life repercussions. In addition to a surge in phishing campaigns that are quite common after a large-scale breach, users faced an increased risk of identity theft and fraud. Personal information like billing details and email addresses can be exploited to impersonate victims or open fraudulent accounts. Just as concerning , some users reported that their cryptowallets were drained.
What should LastPass users do to protect their data?

If you’ve been affected by the LastPass breach, here is how you can protect yourself.
Secure your master password
The more complex your master password is, the stronger the encryption used to protect it.
Go for at least 12, and preferably 16 to 20 characters, using upper case, lower case, numeric, symbols, and special characters. You can generate a random one using the LastPass Password Generator. Of course, don’t use this password anywhere else.
Speaking of password encryption, here is how it works. LastPass uses Password Based Key Derivation Function (PBKDF2). So, each time you enter your master password, it gets hashed a certain number of times, creating a complex encryption key.
The number of hashes is determined by your iteration count. The recommended number is 600,000, which you can set up in your LastPass settings. This entire process makes it harder to expose your password in a brute force attack or take advantage of it if compromised.
Review your overall password strength
LastPass users can check their overall security score in their security dashboard, which is part of the LastPass vault. The password manager calculates this score based on the quality of passwords stored in your account. You should change the passwords marked as weak or reused.
Enable dark web monitoring
LastPass offers this feature to customers, so why not use it? The dark web monitoring tool scans the dark web for email addresses saved in your vault and notifies you if a match is detected.
Use MFA for LastPass
The LastPass breach may be an example of an incident where MFA failed, but remember that MFA has likely protected millions of personal accounts from takeover.
If you are already using MFA for LastPass, the password manager advises you to regenerate your shared secrets in the settings. This secret is what your app uses to create the login codes. As it is stored in LastPass, it might have been stolen in the breach.
You can find additional security recommendations in the LastPass security guide.
How Onerep helps protect your personal information
Onerep reduces your “attack surface” by scrubbing your personal data from data brokers and the public web. After a data breach, cybercriminals may visit these sites to learn more about you. The personal details data brokers expose help them craft convincing phishing emails and other social engineering scams.
To cut down attackers’ access to your data, Onerep scans over 210 data broker sites to find where your information is exposed, sends automated opt-out requests to those websites, and doesn’t stop until your data is taken down.
Once removed, Onerep keeps monitoring 200+ data broker websites to make sure your information doesn’t resurface.
Is LastPass still safe to use?
Factors to consider
LastPass gave its cybersecurity a boost after the incident. It propelled encryption strength through higher PBKDF2 iteration count, rotating credentials, and rebuilding its systems. At present, the way LastPass works is aligned with industry standards.
Still, a breach of this magnitude (and the way it was publicly handled) has understandably made some users question whether LastPass remains their best option.
- If you’ve taken the steps to secure your account and haven’t run into any issues, you might be good to stay.
- However, if your vault was affected and you’ve experienced problems as a result, it’s completely fair to feel uncertain. There’s nothing wrong with exploring other password managers if that feels like a better fit for you.
- If your vault was exposed and you’ve faced trouble because of it, it’s completely fair to feel uncertain, and there is nothing wrong with exploring other options.
But what are the other options out there? In fact, there are plenty, and we’ll briefly highlight just a few.
- Bitwarden. If LastPass’s style of communication rubbed you the wrong way, you’ll be pleased to learn that Bitwarden is known for transparency. Its open-source code is publicly available, and the company prioritizes strong security features.
- 1Password. Intuitive and user-friendly. Many security experts and businesses use it.
- KeePass. Open-source and offline, but geared toward more advanced users.
FAQs
Was LastPass hacked?
Yes, LastPass was hacked in 2022. The hackers exploited a third-party software vulnerability to insert keylogger malware into a software engineer’s corporate device. The attack lasted for about 3 months. Large amounts of LastPass customer data were stolen.
What data was leaked in the LastPass breach?
Bad actors exposed encrypted vault data (passwords, notes) and unencrypted info like URLs, emails, and billing details. They also accessed MFA seeds and internal cloud secrets, which might be encrypted but accessible with stolen decryption keys.
Is LastPass safe to use now?
The company updated its cybersecurity after the incident. The damage that came out of this breach was grave, but many other large companies suffered from cybercrime. No organization is completely sheltered, and LastPass today is no less safe than other password managers.
What should I do if I used LastPass during the breach?
First and foremost, read the LastPass security bulletin. To sum up, you’ll need to make sure your master password is strong and unique, as well as the other passwords stored in your vault. Enable dark web monitoring in-app and use MFA to log in.




Mikalai is a Chief Technical Officer at Onerep. With a degree in Computer Science, he headed the developer team that automated the previously manual process of removing personal information from data brokers, making Onerep the industry’s first fully automated tool to bulk-remove unauthorized profiles from the internet.