Dark web vs. deep web: key differences explained
What’s the difference between the deep web and the dark web? While the deep web is a collection of all web resources not indexed by search engines, the dark web takes this inaccessibility further, allowing only anonymized access to its content. Technically, the dark web is part of the deep web, but the two should be differentiated as the dark web has the illegal element to it.
While the broader deep web contains legitimate content such as banking accounts, emails, and corporate cloud-stored files, the dark web is a mix of both “good” and “bad” content and activities, making you think twice before accessing it.
The confusion between the deep web and dark web terms is common. Even a 2013 Time Magazine article used the term “deep web” to define what clearly was the dark web in the context of the Silk Road market shutdown.
Let’s see how the deep web is different from the dark web, and why it’s important to understand the nuances for a better and safer online browsing experience.
What is the deep web?
The term “deep web” was first used by computer scientist Michael K. Bergman in 2001, who defined it as all online content that’s not indexed by traditional search engines but hides enormous amounts of valuable information.
However, the roots of the deep web can be traced way back to the mid-1990s. As the internet evolved beyond static pages, search engines and web crawlers couldn’t access dynamically generated or database-powered content, making a large portion of the internet virtually invisible.
The deep web: definition and scope
Simply put, the deep web is everything connected to the World Wide Web but not found on Google or similar search engines. Although indexing and web crawling technologies are now more advanced, not all content can be accessed by them due to technical barriers, data privacy, and intentional restrictions.
The deep web has been evolving along with the internet itself. Historically, its development has been driven by technological innovations, trends in software engineering, and data privacy requirements:
- Authentication systems (session tokens, cookies, access controls) created websites with restricted access.
- Dynamic content and databases serve data based on user input and generate output in real time, making it impossible to index.
- Advances in programming languages made it possible to render content without refreshing or creating new pages, as well as interact with databases to serve content dynamically.
- Robots.txt can be used by web developers to intentionally block certain content from indexing.
- Encryption, firewalls, and network access controls allow content to remain hidden and blocked as needed.
It’s said that the deep web occupies more than 90% of the entire internet. Its scope is vast and spans hundreds of web resources hidden from search to protect sensitive information.
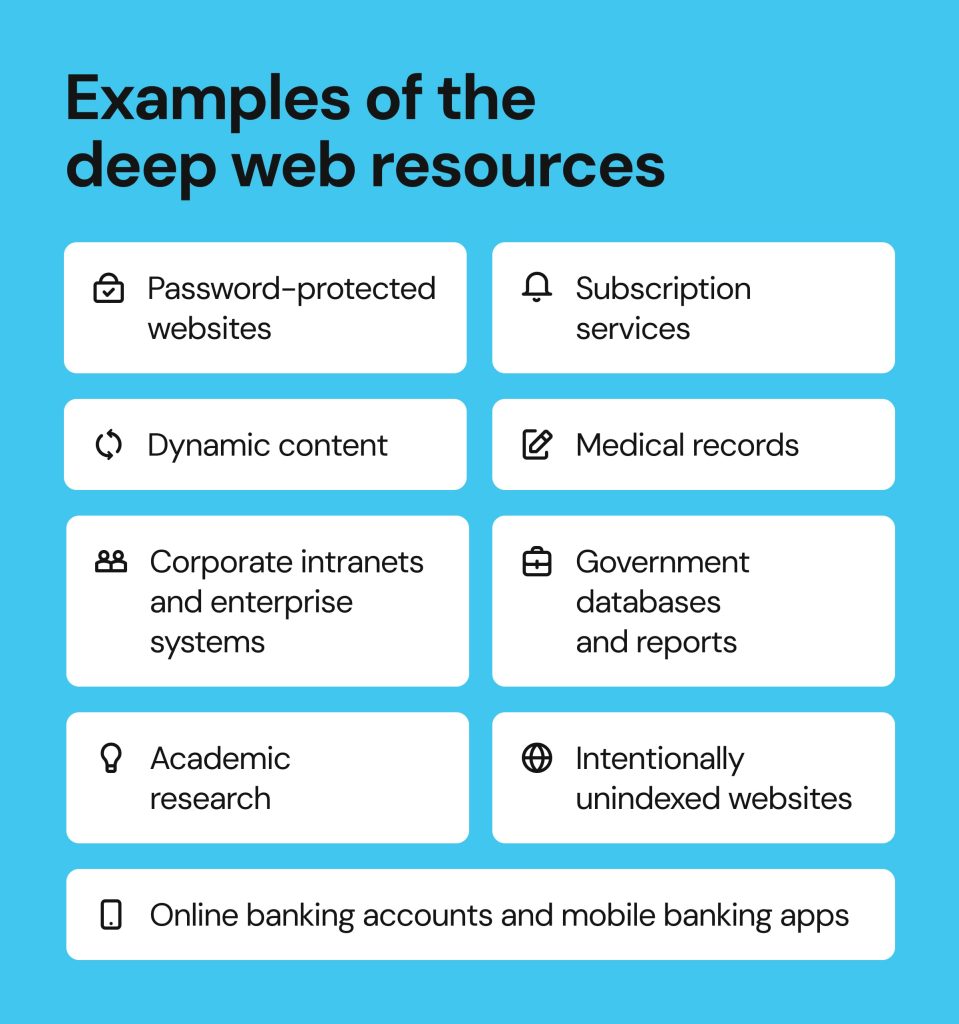
Examples of the deep web resources
You’d be surprised to know that the average internet user interacts with the deep web all the time. Examples of the deep web are everywhere you look and include:
- Password-protected websites (Gmail, Facebook, LinkedIn)
- Dynamic content (filtering and search results on sites like Indeed, Amazon, Expedia)
- Corporate intranets and enterprise systems (hosted by platforms like Salesforce, Microsoft 365, etc.)
- Academic research (scholarly papers and databases like ScienceDirect)
- Medical records (patient portals, personal health records on platforms like MyChart)
- Online banking accounts and mobile banking apps (Chase, HSBC, Revolut)
- Subscription services (Netflix, The Economist, Spotify)
- Government databases and reports (e-services like IRS, PACER)
- Intentionally unindexed websites (websites under construction, development instances on staging domains, Notion pages, private Google Docs and GitHub projects)
As you can see, these deep web examples are harmless but still need to be protected from unauthorized access. Strict security controls are almost always in place to shield deep web information from exposure.
Why the deep web is not dangerous
The deep web is safe to access as its content is legitimate and appropriate in almost all cases. It’s hidden because of regulatory and digital privacy requirements, technical restrictions, and content monetization mechanisms, not because its users want to conduct illicit activities.
What is the dark web?
The deep web’s notorious counterpart is the dark web—a cover-up for those who want to stay anonymous, for good or bad. The dark web is not only hidden from indexing but is made private on purpose—to anonymize users, encrypt traffic and decentralize data governance. This part of the web is not regulated but is monitored by law enforcement agencies for traces of illegal activities.
The dark web went mainstream after the innovation—the Tor (The Onion Router) network—became available in the early 2000s. The technology was developed back in the mid-1990s in the U.S. Naval Research Laboratory but the first working version wasn’t released until 2002. Since then, the dark web has grown to attract an average of about two million daily users (though April 2025 saw a spike to more than six million daily users). Tor is still partly funded by the U.S. government.
The dark web’s primary purpose has always been to support privacy and freedom of expression, but it has also created a welcoming environment for illicit trade and cybercrime. Even now, the dark web remains one of the world’s biggest legal and ethical challenges.
Accessing the dark web via Tor or I2P
The dark web refers to the section of the internet that can’t be accessed via common browsers like Google Chrome or Safari. Because of its encryption, anonymization, and peculiar traffic routing, you’d need specialized software, such as the Tor browser or the I2P router software.
Tor and I2P (Invisible Internet Project) are two different types of anonymous, decentralized, peer-to-peer networks. While both enable private and censorship-free communication, I2P is designed to access sites found exclusively within the I2P network. This network hosts its own messaging and file-sharing system, enabling multiple layers of end-to-end encryption for optimized internal communication. Unlike I2P, you can use Tor to visit the regular internet too—it just adds a layer of privacy to your online sessions.
Why people go on the dark web: common use cases
With its multi-million daily user base, the dark web attracts people from all walks of life—and for all sorts of purposes.
Some of the more innocent use cases include avoiding internet surveillance and personal data collection, seeking freedom of speech under oppressive regimes, avoiding censorship, communicating securely and accessing prohibited digital resources and literature. These opportunities draw journalists, researchers, whistleblowers and activists to the dark web.
The dark web draws criminals, too. That’s why it has become synonymous with cybercrime, the buying and selling of drugs, weapons, stolen data, malware, and counterfeit goods, to name just a few illegal areas. For example, dark web monitoring reveals millions of stolen personal data records traded on the dark web, making it a lucrative business for cybercriminals.

Why exploring the dark web is risky
You can’t casually stumble into a dark web site; you can only access it deliberately. When you do, keep in mind that whatever your good intention, you may still run into illicit content, scams, and illegal trade.
Remember that the dark web is a dangerous place. It’s fine to explore it out of curiosity, as long as visiting the dark web is legal in your location (in some, it’s not). But browsing the dark web can still expose you to malicious websites and the content you didn’t intend to see. Read our guide to dark web websites for tips on how to browse the dark web safely and legally.
Surface web vs. deep web vs. dark web
Now, the only piece missing in the deep vs. dark web comparison is the surface web. Often called the open web, this part of the internet is openly available, indexed by search engines, and accessible via conventional web browsers. It’s the easiest to visit as it requires no credentials, special software, or tech skills—and is just a few clicks away.
Using the traditional deep web iceberg metaphor, the surface web is found, well, on the surface. It’s the tip of the iceberg, with websites like Google, The Guardian, Wikipedia, and Reddit sitting there. Going down, we have 90% of the iceberg submerged beneath water—that is the deep web. At the deepest end of it, there’s a tiny portion (about 4-6% according to various sources) where the dark web is located.
Key differences between the deep web and dark web
The dark web takes the deep web’s information privacy to the next level. Let’s explore how the two terms compare and where they really differ.
Accessibility
Both the deep web and the dark web restrict access to information, but it’s easier to visit the deep web, especially for not so skilled internet users.
The deep web allows only authorized access, so you need the right set of credentials to visit it. At the same time, you can still use your common web browser with no extra software required. For example, you can access your online banking account on mobile using biometric authentication.
In comparison, to access the dark web, you need an impressive toolkit, including a compatible browser like Tor, a well-functioning antivirus system, and some optional add-ons like a portable operating system (for example, TailsOS) and a VPN.
Content
The main difference between the deep web and the dark web lies in the content found there. Information on the deep web is private and often sensitive (such as internal corporate communications, banking details, court and medical records), while content found on the dark web is private and often illicit (related to cybercrime, violence, and the selling and buying of drugs and stolen data, etc.)
While there are legitimate sites on both the deep web and the dark web, it’s the illicit activity often found on the dark web that attracts the most media attention. As a result, the dark web is frequently associated with online crime and underground networks.
Security and privacy
The deep web is not only regulated by national internet policies but is often governed by law as the information there concerns the social, medical, and financial aspects of both individuals and organizations. It can be hacked like any other digital system, but there are security controls in place to prevent it. Deep web users are also unlikely to run into a scam unless, for example, they click on a phishing link in their corporate email inbox.
The dark web is the digital Wild West, where no one is protected from risks as there’s no government regulation and no in-built security measures. It does provide a haven for uncensored communication while anonymizing its users’ identities. Yet, this also makes it easier for cybercriminals to manipulate those same users into giving away their personal information and money through scams, social engineering, malware and fraud.
Legal vs illegal usage
The deep web is almost entirely legal and safe to use—except for the portion occupied by the dark web. Deep web resources are used daily by regular users, companies and even governments, helping them keep sensitive and confidential information hidden.
In comparison, the dark web is a mix of both legal and illegal activities. Users may go there to read uncensored news, find like-minded internet privacy enthusiasts, exchange ideas and do academic research. Or, they can use it as a hideout for illicit trade, cybercrime, drug trafficking and many other activities that are both dangerous and illegal.
Dark web vs deep web: summary of key differences
The table below provides a concise summary of the main points discussed above, outlining how the deep web and dark web differ from each other.
| Feature | Deep web | Dark web |
|---|---|---|
| Technical requirements | Standard web browser and OS | Special software (Tor, I2P) TailsOS (optional) VPN (optional) |
| Accessibility | Requires authorization in most cases | Requires specialized software and credentials (in some cases) |
| Search indexing | Not indexed | Not indexed |
| Purpose | Private information protection | Anonymous communication, privacy protection |
| Types of content | Emails, social media accounts, banking accounts, academic papers, corporate intranets, medical records | Darknet markets, forums, whistleblower sites, hacking tools |
| Legality | Largely legal | Both legal and illegal uses |
| Security | Data protection, access controls, network security controls | User anonymization, data privacy, encryption, random traffic routing |
| Examples | Gmail, JSTOR, Spotify, MyChart | SecureDrop, Hidden Wiki, ProPublica |
Why the deep vs. dark web distinction matters
Even though the dark web and deep web are really close in meaning, these terms are not synonymous. They are still used interchangeably, often to sensational effect, which leads to even greater confusion and anxiety among the public. That’s why it’s important to draw the line between the two to prevent misidentifying the larger deep web as dangerous.
Misconceptions in media and pop culture
The deep web is often portrayed as the hidden internet that’s entirely illegal, which is not true. News reports, media publications, documentaries and Quora answers may refer to the deep web as a whole without distinguishing its dark web subset when discussing lawlessness and rampant cybercrime. In reality, illicit websites take up only a small portion of the deep web, found in its dark web corner. However, the harm these websites can cause is unprecedented, so you still shouldn’t brush it off.
Impact on online privacy perception
Mixing up the dark web and the deep web often leads to a negative perception of online privacy in general. However, when used for good, the concept is highly useful and brings multiple benefits, from protecting legitimate confidential information to supporting the right to online anonymity.
The dark web, too, can be used for benign purposes and plays an important role in protecting civil liberties, including freedom of expression. Much like any other technology, the dark web is a tool, and it’s how you use it that matters.
Staying safe on all layers of the web
Any part of the internet, even the surface web, makes users vulnerable to countless cyber risks—data breaches, malware, phishing attacks, Wi-Fi eavesdropping, fake websites, account hijacking, you name it. Oftentimes, our carelessness and lack of security awareness make it easier for cybercriminals to exploit our data. In some cases, they don’t even need to hack anything as we willingly give away our personal information ourselves.
Make privacy-first browsing a habit
The first step to protecting your personal information and identity online is to adopt privacy-first browsing. This includes the following best practices:
- Use only strong, unique passwords along with multi-factor authentication
- Use privacy-respecting browsers like Mozilla Firefox and Tor that block trackers
- Disable third-party cookies
- Use a VPN to prevent ISP tracking and mask your IP address
- Use search engines like DuckDuckGo that don’t track your online behavior or build advertising profiles
- Always use trusted antivirus software
- Update your devices and software regularly for the latest security patches
- Sign up for dark web alerts to get notified if your personal data is found on the dark web
How Onerep helps you minimize online exposure
The less data circulates about you on the web, the harder it is for cybercriminals to exploit it. One simple step to reduce your digital footprint is to remove your data from people-search websites and data brokers. These resources gather publicly available information about you and either feature it openly or sell it to third parties. This information is often enough to piece together your profile and steal your identity for fraudulent purposes.
Onerep removes your personal data from 210+ websites, automating opt-out requests and monitoring where your data appears and reappears online. This helps reduce the risks of identity theft, doxxing and targeted scams.
Explore Onerep to see how we can help protect your privacy online and beyond.
FAQs
Is the deep web illegal?
No, the deep web is not illegal in general. It simply hosts content not indexed by search engines and often requires credentials to access. In comparison, the dark web—also technically located in the deep web—contains both legal and illegal content. It’s the latter that makes it a place to avoid.
Can you access the dark web without Tor?
Accessing the dark web requires specific tools designed to preserve anonymity, such as the Tor browser or networks like I2P. Standard web browsers like Chrome or Firefox cannot reach dark web content, as it’s intentionally hidden from the surface web and not indexed by traditional search engines.
What’s on the deep web vs. dark web?
You can find everything not indexed by Google or other search engines on the deep web. These resources include legitimate information like banking and medical records, internal corporate portals, business systems, staging domains, accounts that require authorization and so on. The dark web allows everything, from legitimate news portals to black markets, disturbing and illegal content, stolen data dumps and much more.
Is my data on the dark web part of the deep web?
Not necessarily, but it’s advised to check for it. There are many data leak monitoring tools, both free and paid, that can scan the dark web for traces of your personal data exposed in a data breach and notify you if found. Once you know of your data exposure, you can take informed security actions to minimize the risk of identity theft and compromised privacy.





Dimitri is a tech entrepreneur and founder of Onerep, the first fully automated data removal service. Top cybersecurity CEO of 2021 by The Software Report.