Life360 data breach: what happened and what you should do next

Life360, a family safety app that offers real-time location tracking, crash detection, and emergency roadside assistance services to over 66 million users around the world, experienced two security incidents in 2024.
The first incident involved the manipulation of an unsecured Android API to compromise the personal data of more than 440,000 customers. The second incident occurred within Tile, a tracking device company owned by Life360, when a bad actor used a former employee’s login credentials to access sensitive user data.
Both incidents raised concerns about flaws in API security and access management, including weak login protections without multi-factor authentication (MFA) and the dangers of keeping unused credentials active.
This article will break down what happened in the Life360 data breach, what kind of information was compromised, how Life360 responded, and what you can do to protect your personal data moving forward.
What happened in the Life360 data breach?
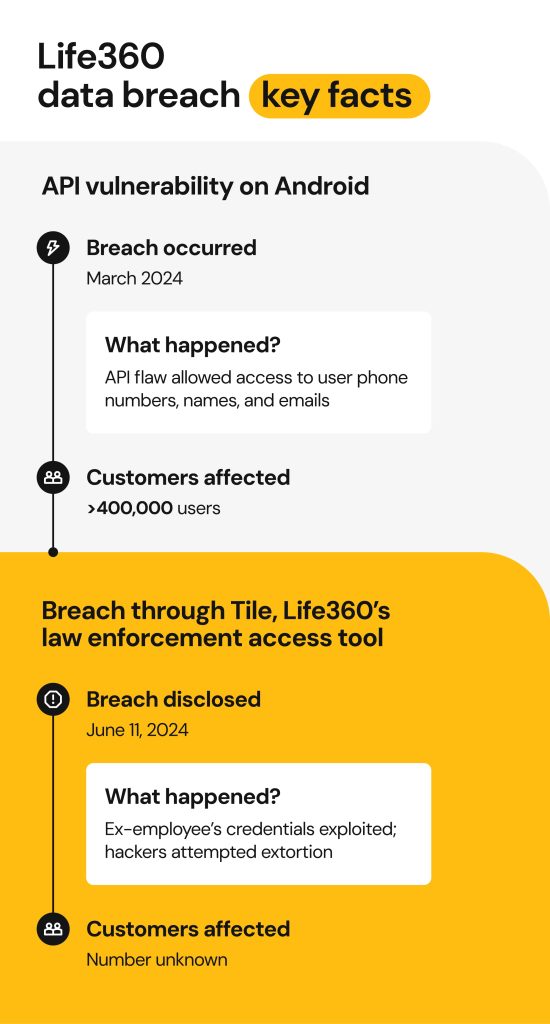
Part 1: API vulnerability on Android
The first data breach occurred due to a systemic flaw within the company’s Android Application Programming Interface (API), allowing a bad actor to obtain personal information of approximately 442,519 users.
An API is a tool that enables different software systems to communicate, in this case, the Life 360 Android app login page and the server. Once you enter your login credentials, the API takes that information to the server and, if the credentials are correct, returns a confirmation notice that allows you to log in.
Let’s translate this digital process to a physical space: imagine entering a secure office building where you work. You walk up to the reception desk and show the receptionist (API) your ID badge. The receptionist should take your badge, verify that it is within the building’s internal system (server), and allow you to pass. Now, imagine that they also call out your name, phone number, and email before letting you enter.
This is exactly what the Life360 API system did, although the users weren’t aware because the data wasn’t displayed on the login page.
How was the flaw discovered?
The data obtained through the Life360 data breach was leaked on the dark web by someone who used the alias “Emo”. This individual stated that it wasn’t them who originally breached Life360, but they used reverse engineering to expose the flaw.
Emo used an Android emulator, which is computer software that mimics an Android phone, to install the Life360 app. They also set up a proxy, a tool that intercepted traffic between the app and the server, to see what data was sent and returned by the faulty API.
Once the issue was evident, Emo wrote a script to send repeated login requests and collect the returned personal data of hundreds of thousands of users. Next, they went on a dark web forum to explain the technical process and leak the compromised data.
Part 2: Unauthorized access to a Tile customer support platform
Life360 also suffered a cybersecurity incident related to Tile, a company most well-known for making Bluetooth tracking devices similar to Apple’s AirTags, which it acquired in 2021. Tile had a restricted portal for law enforcement requests about the location of its trackers, which was meant to be accessed only by the police and authorized personnel.
However, cybercriminals obtained the login credentials of a former Tile employee and used them to access the portal. Once they came into possession of the customer’s personal information, bad actors demanded ransom from Life360.
This incident pinpoints serious internal access control failures, including not revoking the former employee’s access after they departed the company and not implementing multifactor authentication (MFA) as an additional layer of cybersecurity.
What data was potentially exposed in the Life360 breach and why does it matter?
API incident data
The API incident may have compromised the following user data:
- First and last names
- Email addresses
- Phone numbers
Unverified phone numbers were fully exposed, while the API returned the verified ones as partially masked (+1******4830).
Tile platform incident data
The breach into the Tile platform may have exposed the following user data:
- First and last names
- Email addresses
- Phone numbers
- Tile device ID numbers
Life360 stressed that the exact location data, passwords, payment information, or Social Security numbers (SSNs) were not compromised.
How the Life360 data breach could put you at risk
Although government-identifiable or financial information wasn’t compromised, the breach could pose significant risks:
- Phishing attacks: Personal info can be used to create compelling phishing emails.
- Smishing attacks: Cybercriminals could send you fake text messages, seemingly from Life360 or another trusted source.
- MFA fatigue attacks: Bad actors may try to log into your account repeatedly and trigger numerous MFA pop-ups, hoping that you would approve one out of confusion.
- Secondary ID theft: Attackers might combine your leaked personal info with data found on public data broker websites to impersonate you more convincingly and commit fraud.
Is the Life360 data breach legit?
Breach confirmation timeline
The incident related to API vulnerability occurred in March 2024, and the compromised data resurfaced on the dark web in July 2024. Life360 promptly notified its users upon discovering the incident. BleepingComputer verified that the leaked information belongs to actual Life360 customers.
While it’s not clear when the Tile-related data breach occurred, it was publicly disclosed on the Life360 website on June 11, 2024.
Life360’s reaction to the Tile breach
We have taken and will continue to take steps designed to further protect our systems from bad actors, and we have reported this event and the extortion attempt to law enforcement. We remain committed to keeping families safe online and in the real world.
According to the Life360 website statement, the Tile incident was a ransomware attack, and it was reported to the authorities. The exact number of affected customers was not specified, but the compromised data types were listed.
The company emphasized the separation between the Tile support platform and its core services. “We promptly initiated an investigation into the potential incident and detected unauthorized access to a Tile customer support platform (but not our Tile service platform)…We believe this incident was limited to the specific Tile customer support data and is not more widespread”, Life360’s CEO stated.
What should users do now?
If you are a Life360 user, there are steps you can take to protect yourself after the breach.

Check dark web exposure
You can try a few helpful tools to see if your personal info was exposed. HaveIBeenPwned lets you check if your email address or phone number have been exposed in known data breaches. Also, you can set up a dark web monitoring profile with Google that will check for data on the dark web that might be associated with your email address or other info you add to your monitoring profile. It can alert you if your name, address, email, phone number, username, or password appears in leaked databases. Using either or both of these tools is a good way to stay on top of any potential issues.
Utilize Life360’s built-in breach monitoring
Life360 has a Data Breach Alerts feature built into the app. If you’re subscribed, make sure to enable it in the account settings to be notified if your data appears in a breach.
Update the Life360 app and review permissions
Life360 patched the API vulnerability in July 2024, so make sure that you are using the updated app version. Also, don’t forget to review the app’s location and visibility settings and minimize access.
Secure all associated accounts
Reusing passwords across different accounts puts you at risk of having your accounts hacked. Remember to update your password for the Life360 account and all connected accounts after the breach. Create strong, unique passwords and enable MFA whenever possible.
Monitor for suspicious activity
In the weeks and months following a data breach, affected users are often targeted by bad actors. Keep an eye out for:
- Phishing emails or smishing texts: it’s important to be extra vigilant and not fall for emails and SMS requesting urgent action, inviting you to click on suspicious links, or disclose your personal information.
- Odd account activity and unknown login attempts: don’t forget to enable account notifications and check login history, if available.
Protect minors’ data and identity
If you’ve used Life360 to monitor your children’s locations, take proactive steps to protect them:
- Consider freezing children’s credit profiles.
- Make use of parental control tools to limit their digital exposure and monitor risky behaviors.
Use Onerep to limit your public web data exposure
Onerep specializes in minimizing the exposure of your personal data on data broker websites. The tool has automated the process of detecting your personal information across 200 public data broker sites and sending opt-out requests on your behalf. Even after your data has been removed, we keep monitoring these sites to make sure your information is not reposted. Keeping your data off the public web helps you stay protected from various online threats, including scams, phishing attacks, and identity theft.
FAQs
Was Life360 hacked in 2024?
Yes, Life360 had its API system vulnerability exploited by hackers in 2024. Bad actors also breached the restricted platform of a tracking device company owned by Life360, Tile.
What kind of data did the Life360 breach expose?
The Life360 breach exposed the customer names, email addresses, phone numbers, and Tile tracking devices’ ID numbers.
Is it safe to continue using Life360 after the breach?
Yes, Life360 assured its customers that its API system and Tile platform have been secured after the breach.
Was the Tile app also affected by the breach?
Yes, the Tile customer support platform was breached by bad actors in possession of login credentials of a former Tile employee.
Can I remove my information from data broker sites?
Yes, you can remove your personal information from data broker sites by searching for your information and sending the opt-out requests. This can be done manually or automatically with the help of Onerep and similar tools.





Mikalai is a Chief Technical Officer at Onerep. With a degree in Computer Science, he headed the developer team that automated the previously manual process of removing personal information from data brokers, making Onerep the industry’s first fully automated tool to bulk-remove unauthorized profiles from the internet.