Mobile Drip data breach: what you should know and do to protect your email and phone number

Spam SMS messages aren’t just an annoyance; they may be a sign that a breach has exposed your personal data. These events mirror an incident in 2019, where a researcher discovered a data breach by an unsecured MongoDB database affiliated with the Mobile Drip platform. The database was owned by ApexSMS, a company closely connected to Mobile Drip. An investigation revealed that questionable marketing tactics used to collect over 80 million customer records resulted in the Mobile Drip data breach. Further investigations suggest that ApexSMS attempted to rebrand under the name Rocket Text.
In this article, we explain how these troubling events led to a breach, what information was exposed, and why it matters. Keep reading to also learn ways you can protect yourself if your information was exposed in this breach or similar leaks.
What is mobiledrip.com?
Businesses use online platforms, like Omnisend, that combine email and SMS campaigns with automation to find what works best for their campaigns. A similar tool, Mobiledrip.com, described as a “high-volume SMS marketing” platform, was promoted as a tool for businesses to run automated drip campaigns, segment their audience, and track engagement around millions of text messages. Unlike regulated marketing services, Mobile Drip could be described as a gray market.
While gray markets may look like a legitimate marketing platform, their activities are connected to spam, scams, and misuse of personal data. As a TechCrunch report suggests, Mobile Drip’s operation harassed text recipients through massive custom message spam campaigns that would trick them into signing up for fake offers in exchange for their name, email address, and phone number.
Now, the mobiledrip.com domain is inactive and for sale on GoDaddy.com.
What is ApexSMS, and how is it connected to Mobile Drip?
If you’ve never heard of these companies, you may be asking: What is ApexSMS? If Mobile Drip was the tool used to run the SMS bombing campaign, then ApexSMS was the engine driving it. ApexSMS allegedly orchestrated the “SMS bombing” campaigns, and for a time, a Mobile Drip subdomain pointed to an ApexSMS login page.
This connection and the fact that ApexSMS was the name of the exposed database suggested a close partnership between Mobile Drip and ApexSMS. Bob Diachenko, a cybersecurity researcher and data leak expert, sent his findings to TechCrunch, tying the companies together. He also found more evidence to support the connection.
ApexSMS stored customer information and used Mobile Drip to:
- Blast bulk SMS campaigns to contact lists containing millions of recipients.
- Spam millions of individuals with convincing messages about signing up for fake services.
- Send pre-written text messages that forwarded automatic replies once triggered.
Inside the 2019 ApexSMS/Mobile Drip data leak
How the leak happened
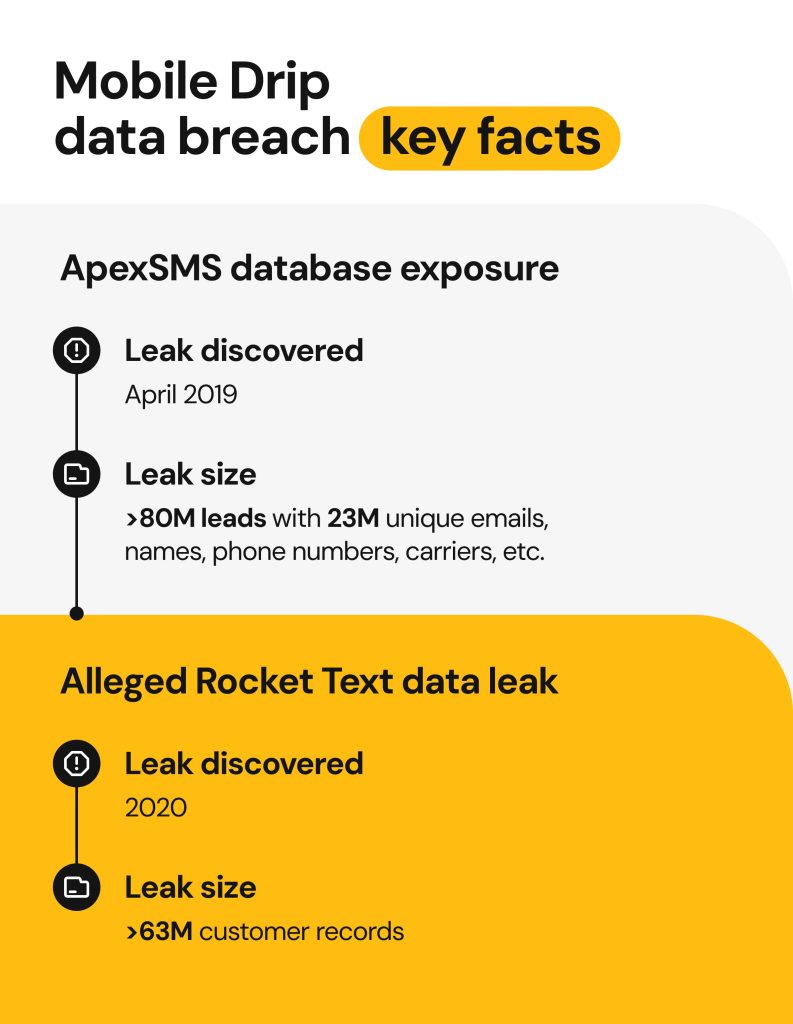
ApexSMS’s questionable activities set the stage for a leak. The Apex sms breach wasn’t the result of a hacking campaign, but an unprotected MongoDB database left exposed on the internet. During his research in April 2019, Diachenko discovered the server wasn’t password-protected after search engines indexed it.
Any bad actor could’ve accessed the data, and what’s worse, this kind of oversight is quite common. Recent studies reveal that unsecured MongoDB databases are frequently compromised, as threat actors use automated tools to find them. This Apex SMS data leak shows that attackers can exploit carelessness to collect and sell your personal data.
What information was exposed?
ApexSMS collected personal data from approximately 80,055,125 “leads.” Within the massive dataset, there were 23 million unique email addresses, names, phone numbers, and mobile carriers. According to HaveIBeenPwned, the Apex SMS data breach also exposed locations, IP addresses, and gender.
As Diachenko researched the spamming operation further, he noted how the platform tracked user activity. ApexSMS sent approximately 38 million messages using disposable toll-free numbers starting with 800, 888, or 877 and convinced roughly 2.1 million individuals to click on the scam links. ApexSMS traced and monitored:
- How many texts each toll-free number sent
- How users responded with clicks or replies
- When the system should rotate numbers to avoid spam filters
SMS bombing and shady tactics allegations
We know the Mobile drip data breach wasn’t just a static data dump, and ApexSMS’s operation contained evidence of marketing tactics commonly associated with scams. Here’s how the scam worked:
- ApexSMS used SMS bombing campaigns. Using Mobile Drip, ApexSMS repeatedly sent varying messages to confuse their targets.
- Used rotating messages and domains to throw off scrutiny. ApexSMS cycled through different message templates and website domains to avoid detection, bypass spam filters, and appear legitimate.
- Lured victims to scam websites. Most of the texts sent out by ApexSMS directed recipients to fraudulent landing pages that would harvest more data from them.
- Tracked activity with Grand Slam Marketing. The database also contained many scam websites, including Grand Slam Marketing. As a so-called “premium partner,” the website kept track of clicks and other engagement across the campaign.
- Victims had more data stolen by hidden scam sites. Copytm.com, another malicious website in the database, used hidden code to scrape sensitive data and funnel it back for future campaigns.
These tactics increase the risks of identity theft for anyone caught in the scam.
Mobile Drip response to ApexSMS breach
Our servers have always been password protected, so any information that may have been acquired was done so through illegal means with the goal of harming the reputation and financial success of the business.
Once the Mobile Drip data breach went public, the company tried to distance itself from ApexSMS. When Mobile Drip was asked for comment, the platform denied any involvement with the SMS bombing operation, citing their terms and conditions for all clients to adhere to federal telemarketing rules. The company also issued a public statement mentioning its meeting with legal counsel and commissioned a security audit to review the data leak.
Moreover, Mobile Drip ignored any claims that its infrastructure was so closely tied to ApexSMS, denied the allegations of its large-scale misuse of client data, and didn’t contact those potentially affected by the leak.
Did exposure continue under Rocket Text in 2020?
The concerns surrounding Mobile Drip didn’t end with the 2019 incident.. In 2020, Diachenko reported another data breach, this time involving a company called Rocket Text. According to his investigation on Security Discovery, Rocket Text appeared to be a rebrand of ApexSMS, operating with the same careless security practices.
The newly exposed MongoDB database revealed striking similarities to the earlier ApexSMS leak:
- It was configured in the same insecure way, left unprotected without a password.
- The Rocket Text database was managed by the same administrator as ApexSMS.
- A screenshot of the MongoDB instance showed it was still labeled “ApexSMS.”
The alleged data breach suggested that the risks of recycled data from ApexSMS were ongoing and exposed over 63 million customer records. While a distinction wasn’t made between the type of phone line, the breach compromised sensitive data, including:
- Customer names
- Email addresses
- Home addresses
- Zip codes
- Phone numbers
Why leaked emails and phone numbers are dangerous

At first glance, a leaked email address or phone number might not seem important. When combined with some personal data from other breaches or even publicly available sources like data brokers, bad actors get a powerful tool to use against you. Some of the most significant risks for victims of the Mobile Drip data breach include:
- Phishing and smishing attacks – Threat actors can use your leaked data to send targeted scam messages through text called “smishing.” Your data helps criminals craft lures to trick you, especially when buying and selling online. Similar to recent Depop scams, scammers can send text-based phishing traps to steal your credentials or credit card information.
- Account takeovers – Threat actors can use your previously exposed data for credential stuffing attacks if you’ve used the same login info for other online accounts. They will attempt to break into and drain your bank accounts or lock you out of these accounts completely.
- Social engineering hooks – Leaked contact information helps criminals sound convincing in scams. An attacker might say, “I’m calling about your Spectrum account ending in…” to gain your trust. They can pull these details from Spectrum breached records, using the data to impersonate support agents and extract more sensitive information.
- Dark web resale – Exposed data often ends up on underground forums, bundled into large datasets containing names, Social Security numbers, financial info, and login credentials. Once copied and resold across multiple markets, it’s impossible to contain and may keep resurfacing for years in new dumps or compilations like MOAB.
How to protect yourself after a data leak like Mobile Drip/ApexSMS breach

If you suspect your information was exposed in a data leak, the best response is to reduce your risk and protect your privacy moving forward. Start following these steps:
- Check if your email was compromised. Trusted breach-checking services, such as HaveIBeenPwned, can tell you if your credentials are part of a breach.
- Change your passwords and enable MFA for all accounts. Never reuse old passwords for different online profiles. You can increase your security by using unique passwords or authentication apps like Authy or Google Authenticator.
- Strengthen your SMS security. Speak to your mobile phone carrier about adding a PIN or port-out lock to protect against SIM-swapping attacks.
- Monitor your financial accounts. Set up transaction alerts with your bank and credit card providers. Consider using credit monitoring services and freezing your credit with Equifax, Experian, and TransUnion to stop bad actors from opening new accounts.
- Be mindful of smishing attempts. Be cautious of unexpected calls or texts, even if they look official. Don’t click links in unsolicited messages and forward any spam texts to 7726 to report them to your carrier.
- Regularly audit app and account permissions. Many platforms request access to your contacts, location, or SMS. Review permissions carefully and revoke unnecessary access to reduce the chance of attackers collecting more of your personal data.
- Limit what you share online. Threat actors can steal your data from old accounts and inadequate social media privacy settings. Ask how online services will store and use your data, and consider saying no when asked to share your details in exchange for offers and services. Safeguard your location, birthdate, or family connections to limit the effectiveness of phishing and impersonation attacks.
How Onerep helps you stay protected
Even if you secure your accounts, it doesn’t address the exposure risks from data brokers and people-search platforms publishing and selling your sensitive information online.
You can attempt to remove this information manually, but the process is time-consuming and repetitive since profiles usually reappear. That’s where Onerep’s approach can help. We protect your privacy with:
- Automated scans and removals – Onerep scans 230+ data broker sites to identify where your data is and begins the removal process until it’s deleted. A free Onerep scan can spot your exposed information.
- Continuous monitoring – Your data may resurface on other platforms. With monthly scans, Onerep repeats removals if a new exposure is found.
- Transparent reporting – Stay informed with visual dashboards and regular updates via your inbox that track the status of your data exposure and removal progress.
- Free trial opportunity – If you want to test the process, Onerep offers a 5-day trial with full access to the platform and its features.
FAQs
Are data leaks something to worry about?
Yes, threat actors can use your exposed data for phishing, smishing, or identity theft schemes. Leaked details are often repackaged with other breach data and sold elsewhere.
Does data leak mean hacked?
No, not always. A data leak occurs when sensitive information is left unsecured. A hack means an attacker is actively breaching systems. Both situations put personal data at risk.
Was Mobile Drip hacked?
No, the Mobile Drip data breach occurred when ApexSMS admins left their unsecured MongoDB database online without a password.
Can I get compensated for a data breach?
Compensation usually depends on class action lawsuits, like the USAA data breach settlement case. No one filed a class action lawsuit against Mobile Drip, so proactive protection steps are the best option.





Mikalai is a Chief Technical Officer at Onerep. With a degree in Computer Science, he headed the developer team that automated the previously manual process of removing personal information from data brokers, making Onerep the industry’s first fully automated tool to bulk-remove unauthorized profiles from the internet.