Target data breach: what really happened and how it impacts cybersecurity today

The Target data breach happened over a decade ago, but it remains one of the most significant cybersecurity case studies to date. It was the first major retail hack to expose how dangerous weak third-party access and poor internal defenses can be.
In 2013, hackers gained entry to Target’s network through a vendor. Sounds familiar? Similar third-party vulnerabilities have caused recent breaches at Bank of America, Prudential Investments, T-Mobile, Comcast, Ascension Health, Amazon and others.
The Target cyber attack affected approximately 110 million people. Some had their payment card data stolen, others lost personal information like names and email addresses, while many lost both.
This article revisits the Target hack to explain how it happened, why it is still relevant in 2025, and what it teaches us about modern digital threats. Most importantly, you’ll learn how to protect your personal information when even big companies fail to keep it safe.
What was the Target data breach and why does it still matter?
The incident left millions of consumers exposed to financial fraud and ID theft and cost Target millions of dollars in out-of-pocket expenses and lawsuit settlements. This was a wake-up call for everyone involved. Target had to make substantial cybersecurity upgrades, and the industry followed.
Does your credit card have a chip? If so, it’s likely because of the Target data breach. Let’s dive in.
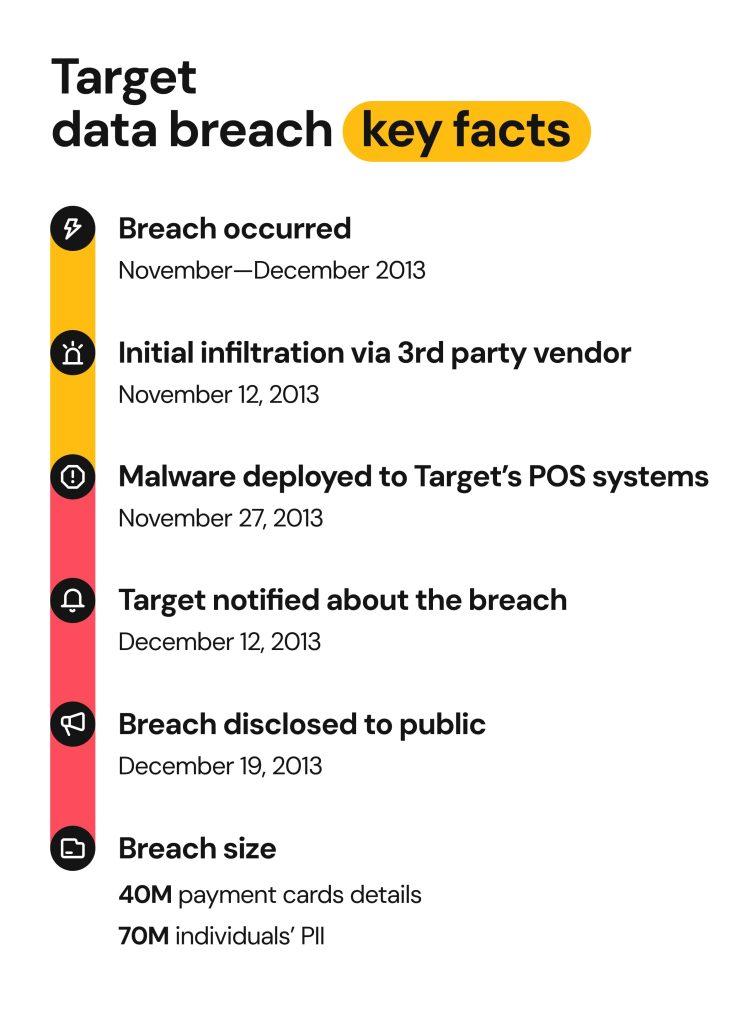
When did the Target hack happen?
Fraudsters chose the 2013 holiday season to breach Target. Here is the exact timeline of events:
- Cybercriminals accessed the Target network on November 12, 2013.
- Scammers deployed their Point-of-sale(POS) malware on November 27, 2013. This is when the attack officially began.
- Target became aware of the breach on December 12, 2013. The attack was quickly contained.
- The retailer notified its customers that their credit card details may have been stolen on December 19, 2013.
- The company added that personal information had also been compromised on January 10, 2014.
How did the Target cyberattack happen?
The Target data breach was a well-planned cyber attack that developed over a few weeks. The hackers did proper research on the retailer’s systems and found a weak link to target.
It all started from a 3-rd party vendor, Fazio Mechanical, which provided refrigerating services to the retailer. The HVAC vendor fell for a phishing attack that contained malware.
This was the Citadel malware, which logs keyboard strokes and takes screenshots, perfect for stealing login credentials. This gave fraudsters access to the Target network. They moved freely across the systems, looked for a vulnerability, and finally found it. The weak spot was used to insert another malware, the BlackPOS, into POS devices in Target stores.
Whenever a customer used their card to buy products in a Target store, their financial information was stored in a POS memory. Fraudsters scraped that unencrypted information, as well as over 11 GB of personal user information from Target servers, and sold it on the dark web.
It took some time for Target’s security team to notice any suspicious activity. What’s more, the staff knew about the POS system vulnerability before it was exploited, but their concerns were dismissed.
What data was compromised and how many customers were affected?
The Target hack isn’t only one of the first cybersecurity incidents to affect the unprepared customers, but also a massive one. Millions of people got entangled just by shopping.
- The hackers stole 40 million payment card details, including credit card numbers, expiration dates, names, PINs, and CVVs.
- Another 70 million customers had their personal information exposed. This included full names, phone numbers, and email addresses.
- Of course, there was an overlap between the two. Some estimates show that in total, 110 million people were affected.
Target’s response: what they did and what they missed
Target notified the public four days after discovering the breach. They opened a dedicated customer support line and offered all US customers free credit monitoring and ID theft protection services for one year.
The retailer’s security team removed the malware and secured the environment. They didn’t stop there and took actions to further strengthen security:
- Vendor access got restricted. After the breach was confirmed, third parties were obliged to use multi-factor authentication (MFA) to access only parts of the system relevant to their role.
- The environment was segregated. Access management was enabled, and sections were split up, especially the payment system, to prevent hackers from moving laterally through the network.
- Chip and PIN cards. After the breach, Target issued new REDcards (credit and debit cards used only at Target that give you extra discounts) and got new POS terminals. These cards contain a chip that generates a new code with every use and requests to insert a 4-digit PIN with every transaction. It may seem tedious, but it is far more secure than standard magnetic stripe cards.
- A new CISO. Target hired a Chief Information Security Officer to improve its cybersecurity.
- A centralized Cyber Fusion Center. Security teams could now collaborate more efficiently in this joint space.
It seems that, given the historic nature of the breach, Target handled the situation well. But, they still received criticism.
People were (rightfully so) upset about the actual duration of the attack. The hackers had infiltrated Target’s network for weeks before the company noticed. This was a major oversight by the security team.
You might be surprised to hear that Target had solid security tools in place. The suspicious activity was detected by the software. Somehow, the security team didn’t think much of these alerts or failed to escalate the situation.
Also, scammers moved freely through the network because it wasn’t segregated. Once they were in, there was no restriction to limit their activity. How were they able to access Target systems in the first place? Customers felt like the third-party vendors should not have open access to the whole of the Target network.
Impact of the Target data breach
Financial consequences for Target
The infamous Target cybersecurity breach cost about $200 million, excluding the legal costs. The insurance covered about $90 million, but the retail giant still spent approximately $110 million dealing with the incident.
According to their 2013 Q4 financial report, Target’s net profit dropped by 46%. Their stock value also declined 0.6 percent to $55.13 in afternoon trade, and foot traffic was reduced.
Somebody had to take the blame for what happened, and it was the CEO Gregg Steinhafel and CIO Beth Jacob. This makes the Target breach one of the first cybersecurity incidents that triggered executive resignations.
Reputational damage and loss of customer trust
Many people didn’t feel comfortable shopping at Target after 2013, at least not right away. The holiday shopping craze was abruptly interrupted, and there was nothing much to do.
According to a public perception survey, the Gen X shoppers (those born between 1965 and 1980), were particularly wary of Target after the breach. They are also Target’s core customer group before the incident.
Luckily, a survey also points out that retailers are the most likely to win back customers after a breach, compared to other businesses. And in the following months, Target made a comeback.
The long-term brand recovery plan was rooted in a few principles:
- Transparency. Target was open about what happened and what they were doing to fix it.
- Loyalty programs. Swapping the Target REDcards and new discount initiatives lured some customers back in.
- Visible cybersecurity improvements. Perhaps the most important aspect, Target was very vocal about making security improvements. They introduced new safety protocols and hired a Chief Information Security Officer to improve their cybersecurity.
Legal settlements and regulatory action
In addition to the money spent dealing with the breach, Target paid another $134 million to resolve the legal headaches. Here is how it went down:
- Attorneys general from multiple states started looking into the incident. Target paid $18.5 million to settle the investigation. The case involved 47 US states and the District of Columbia.
- Consumers filed a class action lawsuit against Target. The retailer settled for $10 million.
- Financial institutions that had to issue new cards after the breach also sued Target. The company first agreed to pay $67 million to settle with Visa. The initial settlement offer with MasterCard fell through, but a new settlement of about $39 million was reached. Of that amount, MasterCard card issuing banks received $19 million in compensation. Other card issuers, like American Express and Discover, were covered by the rest of the settlement.
Why the Target breach still matters: how to protect yourself today
Retail breaches reveal deep risks for consumers
As we’ve seen with HauteLook, Luxottica, and Neiman Marcus, data breaches in the retail industry carry long-term repercussions. This is because the stolen data types typically include both financial and personal information.
This mix of data has high value on the black market. It can circulate for years, be sold over and over, and reused by cybercriminals for different scams. The main concern for customers here is time. Once your sensitive data has been compromised, you remain a potential target for years to come.
The most common scam is phishing, which almost always increases in frequency after a data breach. But fraudsters may also steal your identity and meddle with your finances. For example, they may use your personal information to log in to your banking platforms, transfer money, apply for loans, or file fake tax returns.
How to protect your personal information after a data breach
Data breaches may carry risks, but you can also take steps to protect yourself. Here is how:
- Check your credit reports and bank statements regularly. This is the time to review all your transactions and question the unfamiliar ones. Fraudsters sometimes take small amounts as a test before attempting to steal larger sums.
- Set up fraud alerts or credit freezes. A fraud alert will prompt creditors to take extra care when verifying your identity. A credit freeze will quite literally prevent anyone from opening new credit in your name. An alert is a good precautionary measure, while the freeze makes more sense in high-risk situations.
- Watch out for phishing and scams. As we mentioned before, you are likely to be targeted in the months following a breach. A faux email from your bank, a call from a fake Target customer support agent, or an SMS asking to confirm your purchase. Pause and think before clicking on any links or downloading any files. And absolutely never disclose your sensitive information to anyone via phone call or email.
- Scan the dark web for data leaks. The quickest way to see if your email was leaked in a data breach is to look it up on HaveIBeenPwned.com. You can also set up dark web alerts with Google.
- Monitor and manage your digital footprint. Cleaning up your digital footprint can make you less of a target. Try not to post anything personal on your social networks.

How Onerep helps you control your information
Cybercriminals often rely on publicly available details to appear believable, like your address, relatives or even your birthday. Unfortunately, this kind of personal information is easily found on data broker websites, which serve as a one-stop shop for scammers.
That’s where Onerep comes in. We help you take back control of your digital footprint by removing your information from over 200 data broker sites. Our system continuously monitors these sites to ensure your data stays removed even if it gets reposted.
FAQs about the Target data breach
H3: How do I know if my data was involved?
Have you shopped at Target stores between November 27 and December 15, 2013? Did you get a breach notification from Target? If so, check breach notification tools like HaveIBeenPwned.com.
Is Target safe to shop at now?
More than 10 years later, Target hasn’t had a new data breach. You could say that it is a safe place to shop, but remember that no company is immune to breaches.
Can I still claim compensation?
No, it is too late to claim your compensation now. All the affected customers were compensated.





Mikalai is a Chief Technical Officer at Onerep. With a degree in Computer Science, he headed the developer team that automated the previously manual process of removing personal information from data brokers, making Onerep the industry’s first fully automated tool to bulk-remove unauthorized profiles from the internet.