Ascension data breach explained: what you should know about the Ascension cyberattack and multiple data breaches of 2024-2025

Healthcare organizations are always at risk because of the massive amounts of personal, financial and medical data they’re storing. This data is incredibly valuable for cybercriminals, which makes the healthcare sector a common victim of ransomware attacks and data breaches.
In recent years, several high-profile data breach incidents shook the industry. Change Healthcare, Kaiser Permanente, and Delta Dental have suffered data breaches that impacted millions of people.
Among these, the Ascension data breach stands out as one of the biggest. In 2024, Ascension had a ransomware attack that exposed the data of over 5.6 million patients, followed by multiple non-related third-party data breaches that involved hundreds of thousands more.
This article breaks down what happened, who’s affected, and, most importantly, what patients should do to protect themselves.
What is the Ascension data breach: understanding the incidents

Ascension cyberattack: what actually happened
Ascension, one of the largest private nonprofit healthcare systems in the U.S., suffered a large-scale ransomware cyberattack in 2024. The incident endangered the privacy of over 5.6 million Ascension patients and disrupted clinical operations at all hospitals.
Timeline of the attack
- February 29th, 2024: According to Maine’s state attorney general, the initial breach occurred when an employee unknowingly downloaded a malicious file, which gave hackers a way into Ascension’s network. From there, they launched a ransomware attack and deployed malware to encrypt files. The employee made an honest mistake and wasn’t part of the attack, the healthcare organization reported.
- May 8th, 2024: Ascension detected the breach when its medical providers lost access to patient medical records as well as the network systems needed to do their jobs.
- May 9th, 2024: Ascension’s IT team detected abnormal activity on its network and immediately took critical electronic systems offline to contain the event. They confirmed it was a ransomware attack but didn’t share any specifics at the time.
- June 2024: The healthcare organization revealed that the attack likely breached the patients’ personal information.
- May-December 2024: The healthcare organization worked with Mandiant to investigate and remediate the attack. By mid-June, the electronic platforms were up and running again.
- December 2024: After completing the investigation, Ascension revealed that approximately 5.6 million patients were impacted in the attack. It began notifying the victims and offered two years of free credit monitoring and identity (ID) theft protection services.
Although Ascension never disclosed who the attacker was, a few sources suspected the Black Basta ransomware group.
Systems impacted, including Epic EHR
Cybercriminals invaded only 7 out of 25,000 Ascension servers, but clinical operations in all 140 Ascension hospitals were disrupted. It turns out the breached servers were being used for daily and routine tasks, which led to some of the most important systems being taken down:
- Electronic health records (EHRs): Ascension’s primary EHR platform, Epic, went offline. In some regions, EHR systems, such as Cerner and Meditech were also affected.
- Patient portals: The incident also disrupted the patient-facing Epic MyChart platform.
- Communication systems: Some phone systems were disrupted, making it difficult for staff to communicate internally and with patients.
How the Ascension cyberattack disrupted patient care
Having no access to electronic systems across Ascension hospitals caused a stir for both patients and providers.
What was it like for patients?
- No way to book new appointments, view test results, or order prescription refills online
- Couldn’t get in touch with the providers via phone
- Asked to recall diagnoses, test results, and medications during appointments.
- Advised to bring appointment notes, prescription reports, and medication bottles.
- Had to wait longer than usual for lab work, procedures, and surgeries.
Healthcare providers also struggled to deliver adequate care:
- Difficulty making evidence-based medical decisions: providers had to rely on patients to recall the medications they were using, risking treatment errors if the patient failed to disclose some medications.
- Back to manual systems: writing down patient records and medications using pen and paper. The time-consuming patient charting and limited staff had nurses picking up extra patients, which raised safety concerns.
- Some elective appointments, tests, and procedures had to be postponed.
- Urgent cases had to be diverted to nearby non-Ascension hospitals where they could be triaged properly and provided timely medical care.
Was patient data exposed?
According to Ascension, cybercriminals didn’t gain access to full medical histories, but bits of information were exposed. There was no way of concluding what data type was exposed for each patient, so it’s best to assume that both personally identifiable information (PII) and protected health information (PHI) could have been compromised.
The breached data included:
- Personal information, including full names, street addresses, and DOBs
- Government-identifiable information, including SSNs, passport, driver’s license, and tax identification numbers
- Medical information, including medical record numbers, procedure codes, and types of lab tests
- Health insurance information, including Medicaid/Medicare IDs, policy numbers, and insurance claims
- Financial information, including credit card and bank account numbers
Ascension response: investigation, restoring systems, and breach notifications
The healthcare organization worked with Mandiant, a Google-owned cybersecurity firm, to get to the bottom of the incident, contain the breach, and restore its systems, as well as remain compliant with the regulatory guidelines regarding cybersecurity incidents.
While the investigation was still ongoing, the healthcare organization offered 12 months of free credit monitoring and identity (ID) theft protection services to all patients and associates.
After approximately six weeks of patient care disruption across most hospitals, Ascension announced its electronic systems were safely restored. EHR access was first reestablished in Alabama, Austin, Florida, Tennessee, and Maryland hospitals; other regions waited until mid-June to regain full functionality.
The investigation lasted for approximately seven months and revealed the true scale of the breach. On December 19, 2024, Ascension began sending out breach notification letters and offered affected patients a free 2-year credit monitoring package through IDX.
Reactions to the Ascension data breach: union petitions and public fallout
In the weeks following the attack, Ascension healthcare professionals reported feeling overwhelmed by the increased workload and raised serious concerns about patient safety. Unions responded by launching petitions to improve working conditions.
In light of these circumstances, we demand that immediate safety precautions be implemented to ensure the well-being of both our members and the patients under our care,”
Patients whose data had been compromised also voiced their frustrations via online forums and social networks. Some were upset by the attack starting as an “honest mistake”, accusing Ascension of not providing its staff sufficient cybersecurity training.
The healthcare organization also faced criticism for outsourcing key IT operations and relying on third-party vendors. Many wondered whether cutting corners contributed to vulnerabilities that enabled the ransomware attack to happen.
Critics also pointed out that breach notifications were delayed significantly. A Reddit user wrote: “They need to get sued. They should’ve openly informed the public at least in June or July.” Many people called for accountability and demanded more transparency around what went wrong and how similar incidents could be prevented in the future.
Third-party vulnerability: multiple unrelated Ascension data breach incidents after the major attack
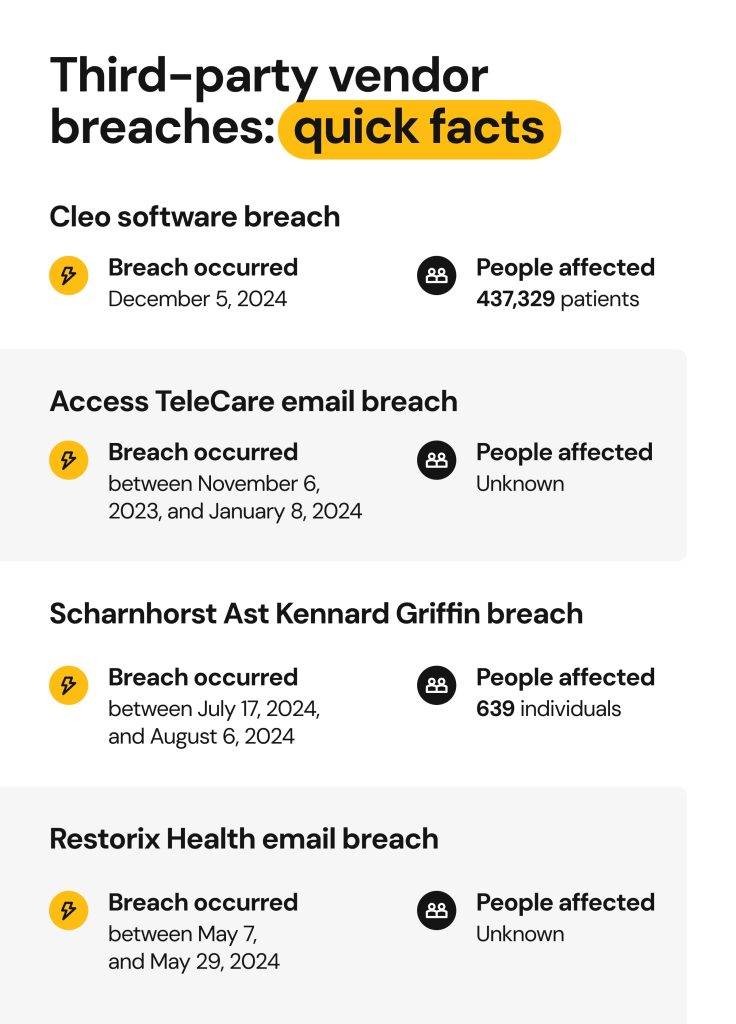
Cleo software breach
In December 2024, Ascension’s former business partner suffered a data breach that compromised the sensitive data of 437,329 patients. The data was exposed through a vulnerability in the third-party software the business partner was using.
Based on the timing and description of the event, it is likely related to the Clop ransomware gang cyberattack on the Cleo file transfer platform.
The compromised data included PII and PHI, such as:
- Full names, race, gender, DOBs, street addresses, phone numbers, email addresses, and SSNs.
- The physician’s name, medical record numbers, diagnosis and billing codes, dates of hospital admission and discharge, and insurance company names.
It seems that the sensitive patient data had accidentally been disclosed to the former business partner. The healthcare organization sent out data breach notifications in April 2025 and offered patients two years of free credit monitoring and ID theft services through Kroll.
Access TeleCare breach
In March 2025, Ascension disclosed a third-party data breach stemming from Access TeleCare. The incident happened between November 6, 2023, and January 8, 2024, when cybercriminals infiltrated the email environment of the telehealth services company associated with Ascension Seton in Texas.
The incident might have compromised the patients’ PII, PHI, and financial data: full names, DOBs, SSNs, passport numbers, medical treatment information, and bank account details. The exact number of affected patients has not been revealed.
Scharnhorst Ast Kennard Griffin law firm breach
In April 2025, Ascension revealed a third-party data breach that occurred at Scharnhorst Ast Kennard Griffin (SAKG), a Missouri-based law firm, and affected 639 patients.
The cyberattack took place between July 17, 2024, and August 6, 2024. Cybercriminals gained access to legal documents and patient data, including demographic information, SSNs, details about the medical treatments, medical records, and patient account numbers.
Restorix Health email breach
In February 2025, Ascension disclosed a third-party data breach that originated at Restorix Health, a business partner that provides wound care management services to Ascension Michigan, Ascension St. Vincent’s Riverside, and Ascension St. Agnes.
The incident happened between May 7 and 29, 2024, when cybercriminals gained access to a Restorix Health employee’s email account. The compromised data may have included PII and PHI, such as full names, DOBs, SSNs, driver’s license, passport, and government-issued ID numbers, medical and insurance information.
Why the Ascension data breach incidents matter
The Ascension data breach serves as an exemplary case study on the importance of cybersecurity in healthcare. When electronic systems are down, the level of patient care suffers. According to a study conducted at Vanderbilt University, hospital cyberattacks may correlate with worse health outcomes and higher mortality rates.
It’s essential for a healthcare organization to take robust cybersecurity measures to maintain its digital infrastructure. Furthermore, third-party service providers may pose a great potential hazard for any organization. Even with robust internal cybersecurity measures, sensitive patient data remains at risk when using vendors with flawed or outdated systems.
The sheer scale of healthcare data breaches underlines the significance of these events. Although Ascension restored its systems and recovered from the attack, millions of patients are still facing long-term risks of having their PII and PHI exposed, including ID theft, fraud, and reduced quality of care.
What should patients do after the Ascension data breach incidents

Check communications from Ascension
If your data has been compromised in an Ascension cyberattack, you should have received a data breach notification letter. Check Ascension’s official channels of communication, or call the customer support center.
Monitor medical records, insurance activity and financial statements
After a healthcare data breach, it’s important to keep an eye out for suspicious activity in your bank statements, insurance reports, and medical records. Bad actors may use your PII and PHI to commit medical ID theft: get treatment, refill prescriptions, or file false insurance claims.
Look for incorrect information in your medical records, such as medical history or blood type, medical bills for services you didn’t receive, or insurance claims for unfamiliar treatments or providers.
Secure online accounts
Remember to secure your online accounts by updating passwords and enabling multi-factor authentication (MFA). You’ll want to create strong, unique passwords for each online account, especially the healthcare or insurance portals.
Register for identity monitoring services
If you received a data breach notification from Ascension, be sure to take advantage of the free credit monitoring and ID theft protection services offered free of charge. Follow the steps outlined in the letter to enroll for IDX or Kroll, depending on what breach affected your data.
Remember that you have to register again for the 24-month IDX credit monitoring and ID theft protection, even if you already applied for the initial service.
Order and review your credit report
You are entitled to one free credit report per year from each of the three major credit bureaus (Equifax, Experian, and TransUnion).
You can get your report:
- online (at annualcreditreport.com),
- via phone call, dial 1-877-322-8228 and follow the automated instructions
- via mail, download a form from https://www.consumer.ftc.gov/articles/pdf-0093-annual-report-request-form.pdf, fill it out, and mail it to: Annual Credit Report Request Service, P.O. Box 105281, Atlanta, GA 30348-5281
Place a security freeze or fraud alert on your credit file
A fraud alert urges creditors to take extra precautionary measures before approving your credit, while a security freeze keeps your credit report hidden from everyone. A fraud alert is a great precautionary measure if you suspect your sensitive info has been compromised, but a freeze offers a higher level of protection for those who don’t need to apply for new credit.
The steps for placing a fraud alert or security freeze are similar:
- Contact the major credit bureaus: Equifax, Experian, and TransUnion (You’ll need to contact each one to freeze your credit).
- Provide proof of identity.
- Request a renewable one-year fraud alert or set up an indefinite freeze that will last until you lift it.
Is there a lawsuit or class action stemming from Ascension data breach incidents?
Overview of legal fallout
A data breach of this magnitude was set to cause a significant legal fallout.
- On May 12 and 13, 2024, two class action lawsuits were filed by Katherine Negron in the U.S. District Court for the Northern District of Illinois and Ana Marie Turner in the Western District of Texas. Both accuse Ascension of failing to implement appropriate cybersecurity measures to protect sensitive patient data.
- On May 24, 2024, a separate class action lawsuit was filed by Yvonne Pratt, a patient at Ascension Saint Thomas Hospital in Nashville, Tennessee. It notes Ascension’s negligence in protecting sensitive patient data to be the main cause of the breach.
- In June 2024, eight plaintiffs from various states filed a multi-state class action lawsuit in the U.S. District Court for the Eastern District of Missouri. The lawsuit accuses Ascension of negligence, violating consumer protection laws, and breach of contract.
How to track or join potential Ascension lawsuits
If you received an official breach notification letter from Ascension, you might be able to take part in ongoing legal actions. The best way to join a lawsuit is to reach out to law firms involved in those legal actions.
Multiple law firms have investigated the May 2024 data breach (and the third-party ones that followed) and filed lawsuits:
- Cotchett, Pitre & McCarthy (CPM)
- Levi & Korsinsky
- Lynch Carpenter LLP
- Markovits, Stock & DeMarco, LLC
To stay updated on the Ascension lawsuit progress and settlement opportunities, follow official channels such as ClassAction.org and ClassActionU.
How to protect your data in a post-breach world
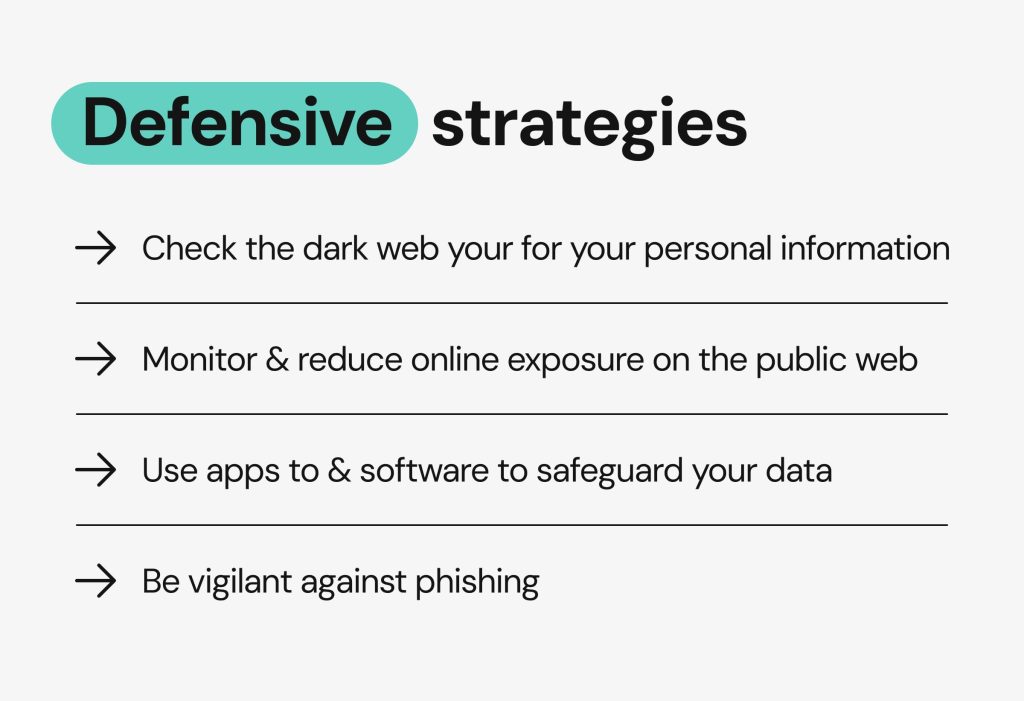
Check the dark web for your personal information
If your data has been compromised, it’s likely to wind up on the dark web. You can check if your email address has been exposed on the public web through haveibeenpwned.com, test out other dark web monitoring tools, or set up a Google dark web monitoring profile. This way, Google will notify you if it detects your personal information (such as your name, address, phone number, email, username, and passwords) on the dark web.
Monitor and reduce your online exposure on the public web
Have you ever Googled yourself? You might want to, just to see what information is out there.
It’s a good practice to regularly review your presence on social networks and check if your personal info can be found on data brokers’ websites. Don’t forget to opt out of these sites to have your data removed.
Given the number of people-search websites, the process of opting out can take a lot of time. Onerep is here to help – we scan 200+ data broker sites on your behalf, automatically identify where your personal information is exposed, remove it, and continuously monitor the web to ensure it doesn’t resurface.
Use apps and software to safeguard your data
If you’ve been entangled in a cybersecurity incident, remember to take advantage of tools that secure your data:
- Throwaway email addresses for online signups will allow you to protect your real email address in case of a breach (and keep the spam away).
- Masked/virtual phone numbers (provided by Google or apps like Burner) can be used to avoid spam and scams.
- VPNs will hide your IP address and make it harder to track your online activity, especially when using a public network.
- Anti-virus software can protect you against phishing and malware.
- Safe browsers, like DuckDuckGo or Firefox, protect your privacy online by blocking trackers and ads.
Be vigilant against phishing
A phishing attempt is what compromised the sensitive data of over 6 million Ascension patients. Obvious scams can become more sophisticated once bad attackers obtain your PII and PHI.
Watch out for:
- Emails or texts claiming to be from your hospital, insurance provider, or breach response manager (like IDX or Kroll), using urgent language and asking you to download files, click a link, or verify your confidential information.
- Phone calls offering help with the breach and asking for more personal information.
If unsure, always contact the organization directly using a verified channel of communication.
FAQs
What caused the Ascension cyberattack in 2024?
In February 2024, an Ascension employee fell victim to a phishing attack and downloaded malware-containing files. Some sources suggest the Russian ransomware gang Black Basta was behind the attack.
Did the attack affect patient records or medical care?
Yes, Ascension’s electronic systems (including EPIC EHR containing patient records) were taken down to contain the cyber attack. In turn, the quality of medical care suffered.
Was Epic involved in the Ascension breach?
As the core Epic database was not compromised, this wasn’t an Epic cyber attack. Still, Epic EHR and patient portals had to be taken down for damage control.
What is Ascension doing to recover from the cyberattack?
Ascension has conducted a thorough investigation of the event and taken steps to advance its cybersecurity.
Can I sue Ascension over the breach?
If you received an official data breach notification from Ascension, you could join one of the ongoing class actions.





Mikalai is a Chief Technical Officer at Onerep. With a degree in Computer Science, he headed the developer team that automated the previously manual process of removing personal information from data brokers, making Onerep the industry’s first fully automated tool to bulk-remove unauthorized profiles from the internet.