Temu data breach: what really happened and how to protect yourself

E-commerce platforms attract cybercriminals of all sorts by storing vast troves of user data. From account takeovers to large-scale data theft, even well-protected online retailers like Ticketmaster or Amazon have faced attacks and third-party data breaches.
Temu, a fast-growing Chinese-owned online marketplace, is one such magnet. Considering the app’s aggressive data collection and intrusive access into users’ devices, the volume of information it may hold is staggering.
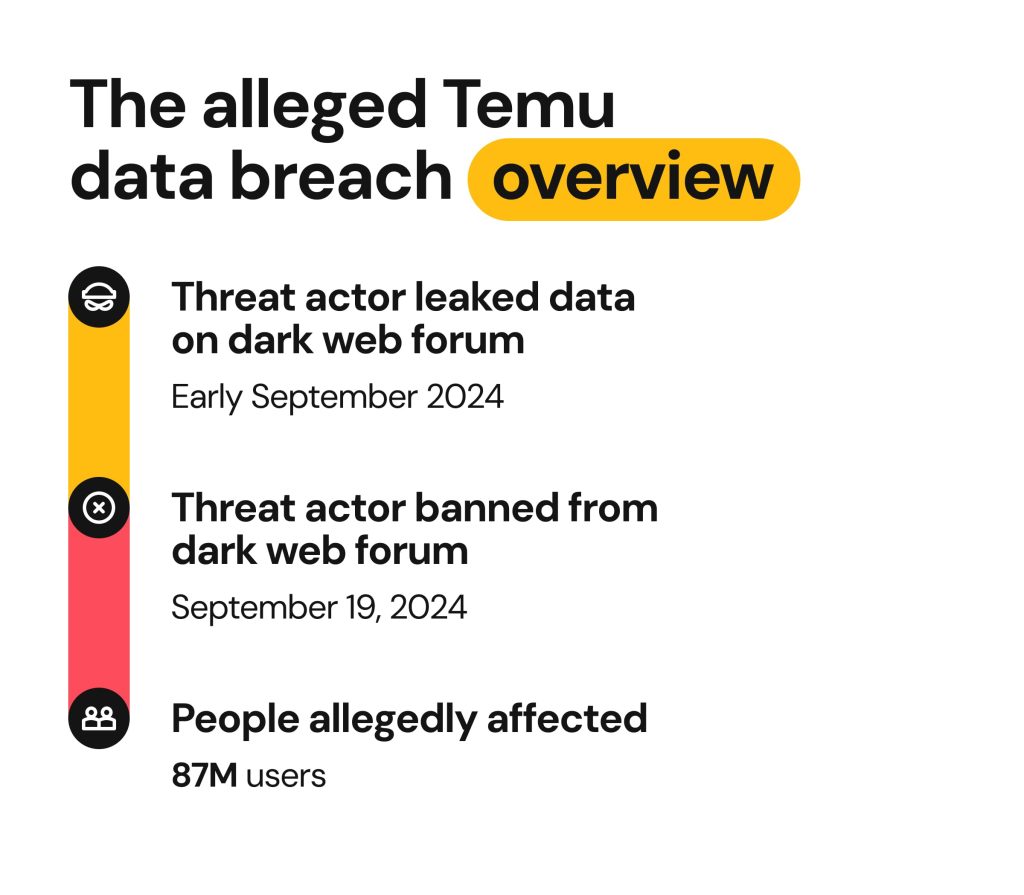
So it was only a matter of time before news broke in 2024 about a potential Temu data breach. The hacker claimed that they breached the app and stole 87 million user records, sparking immediate concern and widespread speculation. But was the breach real?
This article examines what really happened, what cybersecurity experts uncovered and whether Temu users should be concerned. It also outlines how to protect your data on Temu or any similar platform.
What is Temu, and why is it under scrutiny?
If you’ve lived in the U.S. in the past couple of years, you’ve probably heard of Temu. It’s a widely used e-commerce platform set up in 2022. The secret to success? Not-so-subtle marketing (to the level of Super Bowl advertising) and very, very low prices.
Temu’s parent company, PDD Holdings, is Chinese. That is where things start to get sticky: the app is accused of collecting way too much user data and having ties with the Chinese Communist Party (CCP).
The alleged Temu security breach: fact vs fiction
Hacker’s claim on BreachForums
On September 16, 2024, a hacker named “smokinthashit” claimed to have hacked Temu and compromised 87 million Temu user records. As proof, they published a sample of the breached data.
The sample contained personal details such as full names, gender, DOBs, phone numbers, shipping addresses, IP addresses, usernames, and hashed passwords, which, if turned out real, could be used to conduct phishing attacks, hack into customer accounts, or steal the users’ identities.
Temu’s response
Temu carried out an investigation and stated there was no data leak. They compared the sample data with internal user records, but didn’t find a match. The officials emphasized how strong their cybersecurity is.
We take any attempt to tarnish our reputation or harm our users extremely seriously and reserve the right to pursue legal action against those responsible for spreading false information and attempting to profit from such malicious activities.
What cybersecurity measures does Temu employ?
They protect user accounts with 2-factor authentication (2FA), have a MASA certification from DEKRA, and adhere to the industry standard for processing credit card details, PCI DSS.
Temu is also participating in the HackerOne Bug Bounty Program. This initiative invites the “good” hackers to discover systemic weaknesses and report them before they get exploited by bad actors. Of course, a prize is involved.
The breach source debunked
Cybersecurity experts confirmed the sample data didn’t come from a Temu data leak. According to BleepingComputer, CheckPoint Research traced some of this data to a 2021 Foreup.com security incident.
This is not a rare case as bad actors often exaggerate the value of the data they possess and may even repack the data stolen in an older data breach in an attempt to sell it. Finally, the hacker “smokinthashit” was banned from the dark web forum for misrepresenting publicly available information as new.
Why concerns about Temu still persist
Despite the fact that no breach was confirmed, cybersecurity experts, privacy advocates, and regulators continue to question Temu’s motives and overall safety. Much of this attention stems from allegations that the platform collects more data than necessary, thus putting users at risk.
Privacy and spyware allegations
To illustrate the scope, here are just a few of the recent privacy scandals involving the platform. In 2023, Grizzly Research, a short seller known for its aggressive investigations and controversial reports, called Temu “the most dangerous app in wide circulation” and “cleverly hidden spyware”. The report alleged that Temu was designed to bypass the device’s privacy settings and could access various data on the user’s mobile device without asking for permission.
In 2024, the Center for Strategic and International Studies (CSIS) raised additional red flags about the app’s invasiveness. The report warned that the platform may share the data with its parent company, PDD Holdings, and that under Chinese law, PDD could be compelled to share its database with government agencies in China.
Legal challenges and public outcry
In addition to mounting privacy concerns, Temu is facing legal scrutiny in the U.S.
In 2023, a class action was filed in Illinois. The plaintiffs accused the company of violating customer privacy rights by collecting user data without proper consent. This lawsuit was amended in 2024 to accuse Temu of sharing user data with its parent company.
In 2024, the Arkansas Attorney General, Tim Griffin, filed a new state lawsuit against PDD Holdings Inc. and WhaleCo Inc. The lawsuit alleged that the companies violated the Arkansas Deceptive Trade Practices Act and the Personal Information Protection Act.
Temu has publicly denied any wrongdoing in response to both lawsuits, maintaining that its privacy practices comply with industry standards.
Is it safe to keep using Temu?
The argument for caution
Temu hasn’t suffered a data breach, but you may want to consider other Temu allegations (see above) and privacy concerns (read the full breakdown here) before you keep using the app:
- Access issues. Temu might peek into way more than what e-commerce apps usually do. Researchers warn about the app having inherent access to your contacts, camera, mic, location, and possibly other app activity.
- Hidden data collection. Researchers suggest that the Temu app code might bypass your phone’s privacy settings and exfiltrate more data than you might be aware of.
- Sharing information with third parties. Analysts have questioned the viability of Temu’s business model and raised concerns about the app selling user info to third-party companies, including PDD Holdings. As a Chinese company, PDD might have to share its database with the Chinese government as per Chinese laws.
Best practices for safer usage
If the controversies don’t scare you off and you still prefer to use the platform, here are a few important safeguards to keep in mind. These tips don’t just apply to Temu but are useful for protecting your data on any online shopping app.
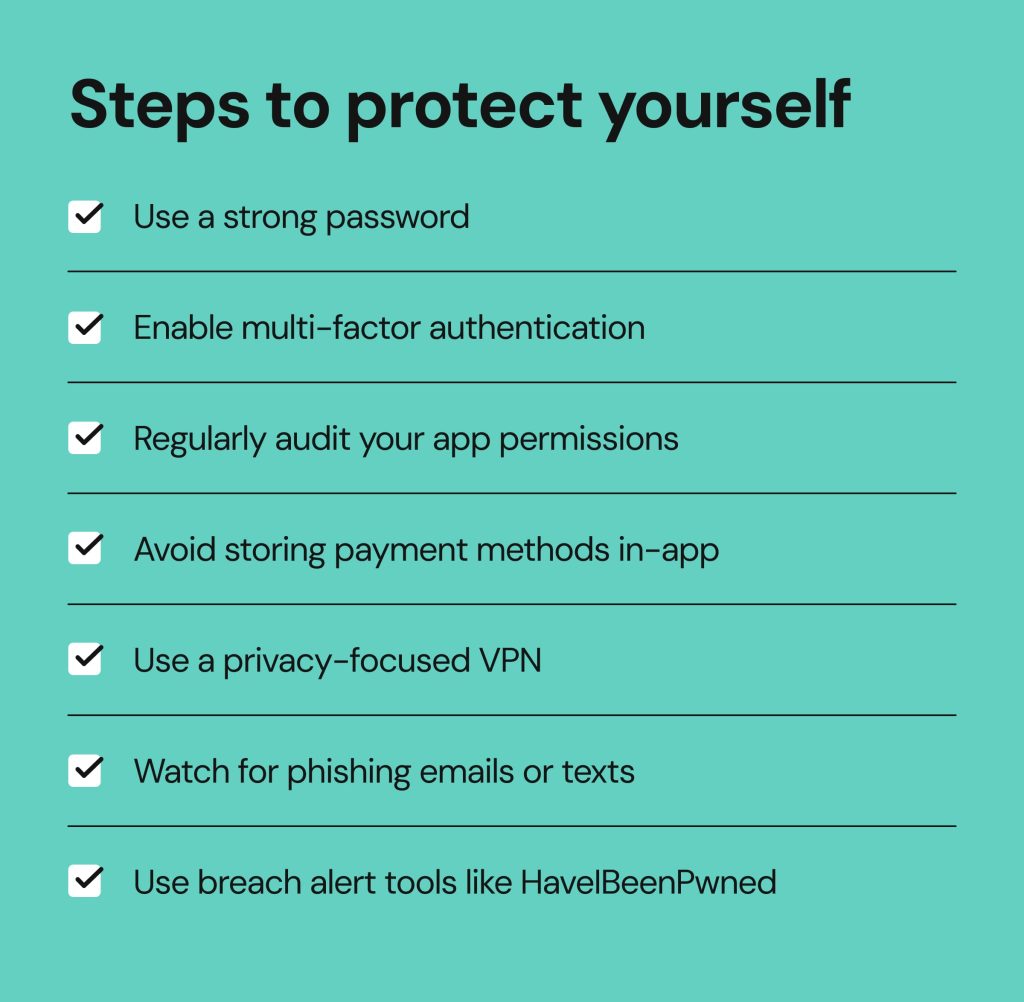
Use a strong password
Breach or no breach, a strong password is your first line of defense against threat actors. A complex password is composed of 12-16 characters, including uppercase and lowercase letters, numbers, and special characters. Don’t use common phrases and qwerty patterns. Even better, get a password manager to create strong passwords and store them for you. And, follow a simple rule of thumb: one password, one website.
Enable multi-factor authentication
If threat actors get ahold of your login credentials, multifactor authentication can still prevent them from breaching your account. The site will require a login code sent to you as a text or email. Some platforms support authentication apps such as Microsoft or Google Authenticator. That way, even if hackers breach your email or phone number through SIM hijacking, they still won’t get the code.
Regularly audit your app permissions
Do you know what your apps track? Make sure to check your privacy settings for each app and disable any that are not necessary for the app to work. Nowadays, you can even set up partial access (for example, an app will see the gallery photos you allow it to access).
Avoid storing payment methods in-app
As convenient as it may be, it’s best not to store your card details in-app. If a platform gets breached or your account gets compromised, your payment details will also be exposed. Make sure to always manually add your card number and CVC for each payment.
Use a privacy-focused VPN
A VPN hides your IP address and makes it hard to track you on the internet. This can help with apps like Temu, which collect your online activity and location.
The best VPNs are paid, but there are a couple of solid free options. Make sure to look for a VPN with strict privacy protocols.
Watch for phishing emails or texts
No matter whether you know that your data has been exposed or not, be wary of phishing scams. Fraudsters used to send generic phishing messages to everyone, but nowadays, these scams are harder to spot.
Fake emails or texts are often personalized and seem legit. Still, double-check the source before clicking on any links and downloading files. Most importantly, never reveal your personal information to anyone.
Use breach alert tools
With data breaches happening more frequently than ever, it’s a good idea to routinely check if your information has been exposed.
- Use HaveIBeenPwned to see if your email address has been compromised in a data breach.
- Google also offers dark web reports, which will let you know if your personal information is detected on the dark web.
How Onerep helps protect your privacy
As you may know, data broker websites collect, list and sell all your publicly available information for a small fee. They are an invaluable resource for fraudsters, who use this information to craft compelling phishing scams or commit identity theft.
Bad actors can combine data broker details with information exposed in data breaches, or even use information from brokers alone to carry out social engineering attacks, impersonate you, or attempt financial fraud. Onerep helps you limit this risk by cutting off threat actor access to your personal information exposed on data brokers. Think of this as a proactive step, even if you’ve never been part of a known breach.
We restore your privacy by finding and removing your details from more than 210 data broker sites. The process is automated and ongoing: Onerep scans for your exposed information, sends removal requests, verifies that your data has been deleted, and continues monitoring to ensure it doesn’t resurface.
FAQs
Is Temu hacked?
A hacker claimed to have hacked Temu. But, the company denied the breach. Independent research revealed that the alleged sample data belonged to a separate data breach that didn’t involve a Temu information leak.
How do I protect my data on Temu?
You can protect your data on Temu by using a strong password, enabling MFA, checking app permissions, not storing your payment information in-app, using a VPN, and staying wary of phishing scams. High-risk users should consider setting up a credit alert or credit freeze.
Can hackers steal my information from shopping apps?
Unfortunately, they can. No platform is immune to data breaches.





Mikalai is a Chief Technical Officer at Onerep. With a degree in Computer Science, he headed the developer team that automated the previously manual process of removing personal information from data brokers, making Onerep the industry’s first fully automated tool to bulk-remove unauthorized profiles from the internet.