Account takeover fraud: all you need to know about prevention, detection, and recovering after an attack

Nobody wants to be the victim of an account takeover. But you may be making this fraud easier for criminals through some of your seemingly harmless habits. In this guide, we’ll explore this common crime and its variations, and explain how it happens. We will also share the warning signs that indicate an account may be compromised, and what you can do to prevent it and mitigate the damage.
Account takeover fraud is a form of identity theft where criminals gain unauthorized access to victim’s online accounts. Fraudsters employ various techniques to steal user credentials, including phishing, data breaches, credential stuffing, social engineering, malicious software, and spyware.
You can significantly reduce the risk of becoming a victim by creating complex passwords that differ among your accounts, using two-factor verification, bolstering security settings, reviewing your accounts for unusual activity and unauthorized charges, installing reliable anti-malware software on your devices, removing your contact details and other sensitive data from the Internet, and closing unused accounts.
What is account takeover fraud?
Identity fraud, also known as identity theft, is an ever-increasing problem that caused $16.9 billion in losses in 2019. This crime affects individuals like you, organizations such as churches or schools, and businesses too.
Account takeover (ATO) is a type of identity theft that occurs when criminals use information about an individual victim, organization, or business to hijack one or more of their accounts. Account takeovers have gone up 79% this year.
ATO is particularly damaging to consumers, not only because of the amount of financial losses and time it takes to deal with the initial fraud, but also because it may take months or years to repair the damage altogether. Fraudsters may extract customer data from an account to sell, which leads to more breaches. Recovering identities and fixing credit reports can be a very long process.
To raise awareness of the problem and arm our readers with the knowledge on how to cope with ATO, we’ll focus on account takeover fraud against people.
What type of data is used for an account takeover?
The personal details criminals use to take over an account depend on what they need. For instance, a poorly protected account might only require a username and password to access it. Other accounts may have more sophisticated protection and might require a one-time password, which would then mean a hacker would also have to gain access to your email account or cell phone.
As we mentioned before, account takeover is a subset of identity fraud. However, it is one of the flavors of identity theft that uses the least amount of data to accomplish. A new account might require multiple pieces of sensitive information, including some harder-to-get data like your social security number and a valid credit card. But account takeover is sometimes accomplished with just a couple of pieces of data.
Am I at risk?
Unfortunately, everyone is at risk. There are some common mistakes that hackers count on, which increase your vulnerability and heighten the threat of account takeover.
These risky behaviors revolve around weak or repetitive passwords, lowering security settings, and having too much of your private information available on the internet. We will cover how to fix these in detail in the How do I Avoid Account Takeover Fraud section below.
The following factors influence your ATO risk:
#1 Passwords
Risk:
A lot of mistakes that we make with passwords increase our exposure. We have many passwords today and also want to get into our accounts quickly. But using a simple or the same password on multiple accounts makes them easy to crack.
Solution:
Choose complex passwords to ensure password security. It is critical that you do not use the same passwords on multiple accounts. If a hacker gains access to one account password, they will often try to get into your other accounts.
#2 Lack of security
Risk:
People also turn off the two-factor authentication (also known as multi-factor, two-step verification, and two-step authentication), making it easier for them to get into their accounts, but consequently easier for the criminals. Another similar mistake is leaving your cell phone and computer without password protection.
Solution:
Take advantage of the security protections offered to you, including using two-factor authentication. Set passwords, face recognition, or fingerprint verification on your devices.
#3 Too much personal info on the web
Risk:
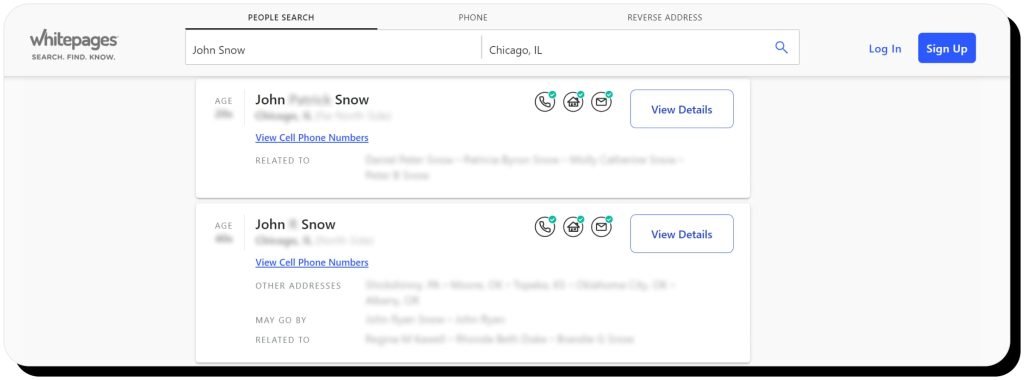
Having too much information out on the internet puts people in danger. Data that shows up on a people-search site like your name, email address, and other contact details can be leveraged to get into your accounts or used as a springboard to find more information about you.
Solution:
Opt out of people-search engines. The law requires them to remove your personal information upon request. You can send your removal requests manually using our detailed removal instructions.
Onerep also offers an automated tool that does it for you, so your information is deleted from the internet and stays gone permanently.
How does account takeover fraud happen?
Criminals find many different creative ways to take over your accounts. They often involve:
- Data breaches in which cyber criminals target a company or institution and secure databases of user accounts. They use this information to access people’s accounts at the breached company and may also have enough information to try to hijack victims’ other, unassociated accounts.
- Phishing scams where victims respond to an email that they think is from a company or institution. These will have a false message saying there is a problem with the account or some other ruse to get the victim to click on a link that takes them to a fake website and then steals their login credentials.
- Remote access scams that result in cybercriminals getting access to victims’ computers under the guise of helping them. They use this access to steal information or install malware to hijack accounts.
- Deceptive scam calls and other social engineering techniques (also known as vishing) are used to access accounts. Scammers may call and say they are from a familiar institution or company and need to verify information. But this is a ruse to get the victim to tell them sensitive data they will then use to breach an account. Bad actors also use email, texts, or social media with the same intentions. Sophisticated scammers may exploit the data they acquired on the internet to trick your friends and relatives into giving them more information about you. They may use what they already know about you to trick customer service representatives into inadvertently helping them compromise your accounts.
- Apps installed on your phone may contain malware that collects data and sends it to scammers, who then compromise accounts.
- Someone in the neighborhood hacking your unsecured WiFi network. In all fairness, an unprotected computer may be compromised remotely by anyone in the world! You are also vulnerable when you are on public unsecured WiFi, like at a coffee shop.
- ATM or point-of-sale skimmer secretly installed over authentic devices. These devices capture account information and send it to the criminals. Skimming usually results in fraudulent charges. However, in some cases, a criminal may leverage information scanned from a card to access and hijack someone’s account.
- Malicious programs that may be inadvertently loaded by a user when installing other software. A computer might also be unknowingly infected when someone is browsing the internet. Spyware may capture personal information, including passwords, then send it to criminals who will use it to compromise your accounts.
- Stealing your mail or your wallet or even going through your trash might seem old-fashioned, but sometimes the information contained in any of these places is all an offender needs to access your accounts.
Common types of account takeover fraud
Loyalty fraud
Loyalty fraud is a growing problem, with losses from loyalty and reward program points estimated at $1 billion per year. There are a few ways loyalty fraud can occur that directly impacts businesses, such as when scammers steal rewards. Ultimately, consumers pay for this type of loyalty fraud in the higher price of goods.
The most common way loyalty fraud affects individuals like you is through account takeover fraud. A scammer acquires control of the account through one of the methods we have discussed and uses your points immediately or transfers them to another account under their control.
Medical account fraud
Because of the increased use of telemedicine due to COVID-19, medical account takeover fraud is skyrocketing. Medical records can fetch $1,000 each, which is ten times more than the average credit card data will bring on the black market. Once a cybercriminal has taken over your account, they can harvest all of the information to sell it on the dark web.
Cybercriminals may also take over your account to get pills prescribed that they can then resell. And like any other account takeover fraud, criminals can also use your medical account information to commit other fraud.
Bank account fraud
There are several different types of bank scam operations that criminals may use, but account takeover fraud is at the top of the list as it’s one of the quickest routes to financial gain.
A typical example of an account takeover occurs when you find yourself unable to log into your financial accounts because your passwords have been changed. After speaking with the bank and accessing your account, you may find that there are fraudulent transactions to dispute.
Social media account takeover
Social media account takeover occurs when a cybercriminal hijacks an account like Twitter, Facebook, or Instagram. They can then use the accounts to try and scam other people.
Three people recently engaged in a widely publicized Twitter hack that compromised the accounts of Joe Biden, Barack Obama, Elon Musk, and other famous people. Once they had completed the social media account takeover, they posted messages stating they would send double bitcoin to those that sent it to them. But the plan was just to collect the bitcoin and never send any money back.
You may become aware of this fraud when you cannot access your social media account or get messages from your contacts telling you there are suspicious posts.
Phone takeover fraud (SIM swap scam)
Phone takeover fraud occurs when scammers activate a new phone using your phone number. Your phone still turns on, but you find that you are not getting emails or text messages and can not get on the internet.
Cybercriminals accomplish this by calling your cell phone provider and tricking them into thinking your phone was damaged or lost and that you now have a new phone. Or they may fool a different carrier into believing you want to transfer your number to them.
Once scammers have access to your phone number, they can take over other accounts linked to your phone number and access your other data.
Credit card account fraud
Credit card account takeovers are becoming more frequent. Much of the past fraud has been when somebody stole card numbers and made fraudulent charges.
Account takeover fraud may involve hijacking your account entirely and changing the contact information. Then you would be unaware of any fraudulent charges because you would not get emails, texts, and statements. They may also add unauthorized users to your account.
Because your contact information has been removed from your account, you may not discover this type of fraud until you check your account yourself. If this is the case, you will have to deal with disputing the charges and repairing your identity and credit damage.
Email account takeover
Email account takeover can be extremely damaging. It may be used as a tool to access other accounts, harvest information about you, and perpetrate fraud on others.
Cybercriminals often target your email first in takeover attempts to then target other accounts using your hijacked email account! This type of account takeover occurs when a criminal gets access to your email due to a data breach, common password, phishing, or another scheme. They may eavesdrop on your emails to see what data they can accumulate about you, or completely take over your account so that you become unaware of verification and notification emails that would warn you of unauthorized activity.
Your first sign of email account takeover may be that your email password no longer works.
E-Commerce fraud (account takeover)
E-commerce ATO attacks happen when a cybercriminal hijacks your shopping account and then uses it for fraud. The scammers may order merchandise and also harvest more information about you, such as stored credit cards or other financial information that you use for payments.
Like other account takeover fraud, the criminal may change your contact information so you might not receive a notification when the scam is happening. You could try to log into your Amazon or eBay account and find that your password does not work. You might also see unauthorized charges appearing on linked payment types, such as your credit card.
IRS fraud
The IRS has warned that account takeover is on the rise. This may involve fraudulent tax filings where the cybercriminal gets refunds intended for you. These criminals will often use social media to gather information about the victim and call or email to get more sensitive data. The IRS generally makes the first contact with you via USPS mail, not by calling or emailing you.
Find out more at the IRS taxpayer guide to identity theft page.
PayPal account takeover
PayPal account takeover is among many vulnerabilities linked to the PayPal payment system. This occurs when a cybercriminal gains control over your PayPal account to make unauthorized purchases, drain your account, scam other people and harvest your linked payment information.
Because PayPal is so popular, it is a prime target for fraudsters. One of the most frequent ways that PayPal account takeover occurs is through phishing emails where the criminal sends what appears to be a PayPal email to the victim, which tricks them into entering their login information.
Similar to other account takeovers, the scammer may change your information. Your first awareness of the issue may be when you see unauthorized charges to a linked payment method.
New account takeover
New account takeover occurs when a criminal adds a new user to your existing account or opens an entirely new account without your permission. You may become aware of this via an email stating you have a new account or authorized user added to your account.
How do I know I’m a victim?
These are some red flags that may indicate account takeover fraud:
- You realize that you have not received any recent emails from a company.
- Your password no longer works.
- A customer representative tells you your verification information is incorrect.
- You have not gotten a bill in a while.
You may be required to prove to an institution that you are their actual customer before they assist you with your account. This process could include sending copies of documents like your identification or a utility bill. While this might be frustrating, it is sometimes a necessary step while reestablishing access to your account.
Once you have access to your account, several things might confirm account takeover theft, including:
- changes to your email address, phone numbers, and street address
- unauthorized charges
- added users
- changed username or password
How do I avoid account takeover fraud?
There is no way to shield yourself from account takeover fraud completely. However, the following checklist of items gives you an action plan that can significantly reduce your risk:
- Don’t reuse passwords across accounts and set up multi-factor authentication. The latter will also help you detect an attack in real-time as someone is trying to get into your account requiring a verification code.
- Review your accounts regularly for any unusual activity. This includes transactions you don’t recognize. Carefully look at all of your contact information, including address, telephone numbers, and emails.
- Keep your computer and cell phone operating systems up to date and be sure you have good anti-malware installed.
- Check your social media accounts and remove any private information that is too public to share. Always be cautious about what you post publicly. You might choose to make a subgroup of more intimate friends to share non-public information.
- Regularly change your passwords, PINs, and security questions. Turn off password hints if allowed, and choose unique security questions for each account. The days of using your mother’s maiden name for every account are long gone.
- Be aware of your billing cycles, so you notice if a bill does not arrive (because a hacker has redirected it). Most financial institutions will allow you to choose your statement closing date, and it might be helpful to synchronize them.
- Close any unused accounts. Bank fraud may occur on infrequently used accounts and escape notice.
- Turn on password protection for your phone and computer.
- Do not carry your social security card in your wallet.
- Keep your cell phone locked and use the other security features available to you. Do not use public, unsecured Wi-Fi networks as hackers can steal your passwords and data.
- Shred any paper documents before you throw them away.
- Keep your phone and computer updated with the latest operating systems and virus protection.
- Review your credit reports. There are free services that keep track of your credit, and Annualcreditreport.com is run by the three major credit bureaus to let you request a report from each once a year. Instead of getting all the reports simultaneously, you might choose to check one every four months.
- Delete your data from information brokers. These websites are a prime place for hackers to harvest your information for account takeover scams. Start with Onerep’s free 5-day trial to remove your unauthorized profiles automatically from 230 people-search engines that expose your information.
- Freeze your credit reports. It’s free and easy. This does not prevent a hacker from taking over an existing account. However, it removes some of their incentives because they will not be able to use any of the information they gain from the hijacked account to open a new account.
- Be careful about sharing your data. A form or website may ask for your social security number or birthdate, but you do not always have to provide it.
- Secure your incoming mailbox and make plans for neighbors to get mail for you or ask the post office to hold your mail if you are away.
What can I do after account takeover?
Once you know you are the victim of account takeover fraud:
- Immediately change passwords for compromised accounts and any other accounts where you used similar credentials.
- Contact the company or institution via the phone number you get directly from their website or previous statements.
- Check your computer and cellphone to be sure they are updated and also check to delete any malware.
- Review your social media accounts and look for any changes that might indicate they have been compromised.
- Change your PINs, passwords, and security questions on all of your accounts and review account activity for suspicious behavior. Be sure to set good passwords that avoid common mistakes.
- Tell people you know about what happened and advise them to be aware they may have been compromised through an email sent from your system during the time the hacker had control of your account.
- Enable all the heightened security on your account, including multi-factor authentication.
- Make reports to the relevant agencies. See the How Do I Report section below.
- Review the How do I avoid account takeover fraud checklist above, and be sure you have completed all of those steps.
How do I report account fraud?
You first want to report account fraud to the company where it occurred. It may be necessary to call them if your online access has been compromised. Be sure to locate the correct contact number directly on the company’s website or from your bill.
Federal Bureau of Investigation
https://www.ic3.gov/
Federal Trade Commission
877-438-4338
https://identitytheft.gov/
U.S Department of Health and Human Services Inspector General (for Medicare account takeover fraud)
800-447-8477
State Consumer Protection Offices
https://www.usa.gov/state-consumer
Internal Revenue Service
https://www.irs.gov/identity-theft-central
800-829-1040
Let’s wrap it up…
Account takeover fraud is disruptive and costly. Being a victim of this crime can feel like a nightmare. And it can take a very long time to recover from the damage. However, armed with the information we have given you here, you know how to reduce your risk and deal with it should it happen.
We recommend that you bookmark this page for your future needs and share it with your friends and family so they know what to do too. Remember to proactively complete the action plan above, including visiting Onerep to remove your personal data from the web to reduce your likelihood of being targeted.
FAQ
Is an account takeover the same thing as identity theft?
Account takeover is a type of identity theft where the criminal impersonates the victim to take over an account. In more complex identity theft scenarios, a criminal may have enough information to make new accounts and do more damage beyond just one account.
What is account takeover protection?
This often refers to companies that will help you recover your identity if there is fraud. However, setting things like two-factor authentication, complex passwords, varied security questions, removing your online data, and other proactive steps are also a method of account takeover protection.
What is password (credential) staffing?
This is also known as credential stuffing. It is a cyber-attack method where criminals use stolen databases of user data to breach systems using bots to try multiple attacks. You can protect yourself against this by using different and complex passwords on every account.
What is credential cracking?
This is an automated brute-force attack on the target service. Unlike credential staffing or stuffing, this technique does not rely on a stolen database. It merely tries a massive number of username and password combinations to get into a company or organization. This type of attack is focused more on getting into a specific company than specific customer accounts.
What is the bank mobile scam?
Some banks partner with learning institutions to disburse financial aid funds and refunds. A student’s school initiates these payments. However, it may seem like bank account fraud because the student was not aware of the partnership. If you receive communications from Bank Mobile, you should check with your financial aid office to determine if it is legitimate or a bank scam.
What is corporate account takeover?
This occurs when criminals gain control over a business’ account and take control of it.
What does social engineering mean?
Cybercriminals use deception to trick victims into giving them sensitive information or performing actions that lead to compromise. They may try to get a victim to provide them with their passwords, credit cards, or social security numbers by pretending to be calling from their bank or other familiar institutions. Sometimes they get victims to perform actions like installing malware or giving them access to their computers.
What are the red flags of account takeover?
The red flags indicating you may be a victim of account takeover include not being able to log into your accounts, unexpected login alerts, unauthorized transactions and other fraudulent activities, changes to user information, unknown devices linked to your account, disabled security features, and missing notifications or emails.
How common is account takeover fraud?
Account takeover fraud has become increasingly common in recent years. According to Sift, account takeover attacks jumped 169% year-over-year in 2022. Another report by Javelin revealed that ATO resulted in nearly $13 billion in losses in 2023 (up from $11 billion in 2022).





Mark comes from a strong background in the identity theft protection and consumer credit world, having spent 4 years at Experian, including working on FreeCreditReport and ProtectMyID. He is frequently featured on various media outlets, including MarketWatch, Yahoo News, WTVC, CBS News, and others.