Zeeroq.com data breach: what happened and how to protect yourself

Imagine waking up to a notification that says your credentials have been found on the dark web. You click for details, expecting to see a familiar platform, but the breach report mentions a website you’ve never heard of before: zeeroq.com.
You’d think this was a scam, but it wasn’t. That was the exact experience many users had when they received breach alerts in early 2024 tied to this mysterious platform.
In this article, we’ll analyze what’s known about the zeeroq.com data breach, explore its possible connection to to a larger security incident called “The Mother of All Breaches” (MOAB), and share actionable tips to protect your personal information.
What is Zeeroq.com?
Now defunct, Zeeroq.com was the website of a cloud services provider that, in January 2024, experienced a data breach connected to the massive Mother of All Breaches (MOAB) exposing 26 billion records from multiple organizations.
The event caused significant confusion among the public. It all began with a Reddit user receiving a notification from Credit Karma (a credit and financial management platform) that their email address and password had been exposed in a Zeeroq breach and asking others if anyone had heard of this website before.
Other Reddit users confirmed receiving similar alerts, but no one seemed to have any recollection of ever using the zeeroq.com website. Some turned to web archive snapshots in an effort to piece together its purpose, sparking a range of speculations and theories. Those included zeeroq.com being a placeholder domain, a design agency, a shady redirect, or even a host for leaked credentials. Still, verifiable information about the site remains scarce.
What we know about the Zeeroq.com data breach
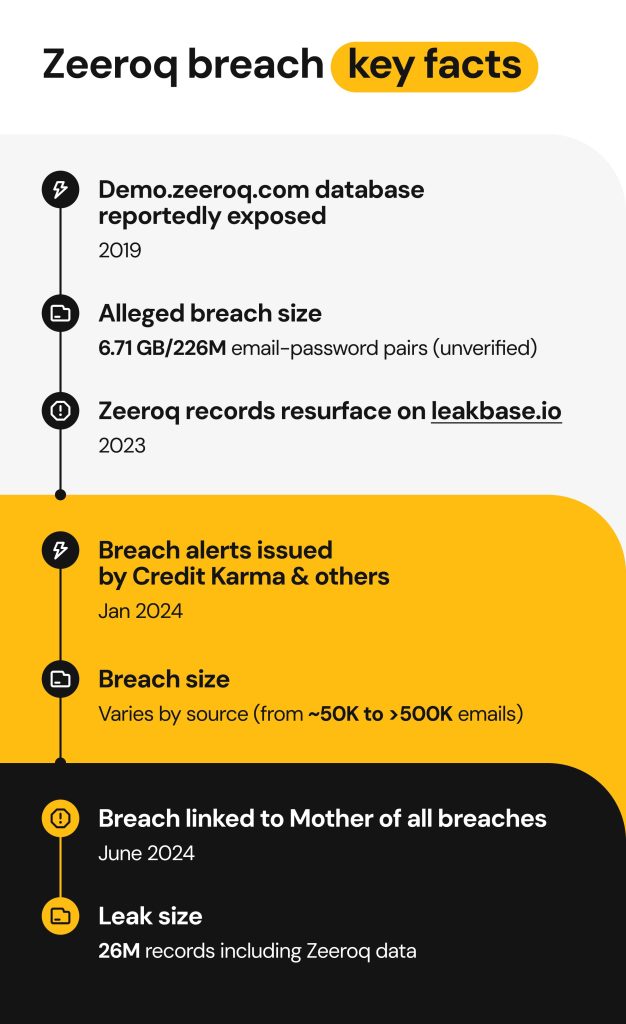
Timeline of the Zeeroq.com breach
2019: The website’s subdomain, demo.zeeroq.com, exposed combo lists — collections of stolen emails and passwords compiled from various breaches. These credentials were published without any protection, making the domain a public repository of breach data. It was unclear if the data was stolen from Zeeroq itself.
2023: The dark web monitoring service InsecureWeb reported that Zeeroq data appeared on leakbase.io (a forum that focuses on database leaks). Researchers didn’t treat this as a unique breach but rather a dump containing credentials from previous breaches.
January 2024 onward: Users started receiving alerts from Credit Karma, VPN services and dark web monitors that their credentials were found on zeeroq.com. HaveIBeenPwned integrated the breach into its database.
June 2024: The Zeeroq.com data breach gained widespread public attention and was linked to the MOAB.
The Zeeroq breach and the Mother of All Breaches
There are data leaks, and then there’s this.
The Mother of All Breaches, also known as MOAB, is a massive leak containing 12 terabytes of data from multiple previous breaches and exposing 26 billion records from 3,800 folders. It contains scraped or hacked LinkedIn data, compromised Venmo records, and user data from countless other platforms, including Zeeroq.
Potentially one of the largest leaked datasets ever discovered, the database was allegedly held by Leak-Lookup, a data breach search engine that suffered a firewall misconfiguration. The leak was uncovered by cybersecurity researcher Bob Dyachenko and the Cybernews team, who believe the dataset includes not only previously breached records but also new, unpublished data.
According to the researchers, the MOAB owner could be a data broker or a malicious actor that can leverage this enormous dataset for a wide range of cyberattacks.
So, essentially, Zeeroq was one of the many data sources included in the MOAB.
What data is exposed?
There’s no consensus among security experts and credible resources about the types of data leaked in the Zeeroq.com data breach. Allegedly, the incident exposed the following information:
- Email addresses
- Passwords
- Names
- Dates of birth
- Phone numbers
- Payment details
Zeeroq.com breach: how to check if your data was exposed
Take the following steps, if you suspect your personal info was compromised during the Zeeroq breach:
- Use data breach monitoring tools like HaveIBeenPwned.com or Cybernews Personal Data Leak Checker: run these checkers using your email addresses or phone numbers to see if any mentions of zeeroq.com, demo.zeeroq.com, or MOAB appear.
- Look for leaked emails (personal or professional), passwords associated with those emails, and any other exposed information, such as phone numbers or payment details.
What to do if your data appeared in the Zeeroq breach

Change passwords immediately (especially reused ones)
If you believe someone has gained unauthorized access to one of your accounts, change your password to a new, stronger one, which you don’t use for any other platform or app. While doing so, combine unrelated words, numbers, special symbols, as well as uppercase and lowercase letters — or use a password manager. Be sure to change your password as soon as possible.
Enable 2FA on key accounts
Fraudsters might want to use leaked passwords to access your private information across multiple accounts. Add an extra layer of security by turning on 2FA (two-factor authentication). This way, criminals will hit a wall, having to pass an additional identification step, such as an authenticator app, SMS code, email code or push notification.
Freeze credit if sensitive data (like SSN) is exposed
Place a free credit freeze with Equifax, Experian and TransUnion — online, by phone or by email — so no one can open new credit lines in your name. If your credit is frozen and someone is applying for credit on your behalf, the potential creditor won’t see the data required to approve the application. A credit freeze stays in place until you lift it.
Contact the three national credit reporting agencies separately to place a freeze on your credit file.
Monitor email, bank, and credit reports
Obtain a free copy of your credit report from annualcreditreport.com or by calling toll free at 877-322-8228. When reviewing your credit report, look for information such as your home address, SSN, accounts and loans that are not accurate or incomplete. If you see anything you don’t recognize, call the business that opened the account or the credit reporting agency that issued the report. Check the Consumer Financial Protection Bureau’s website for more information on how to review your credit report.
You can also place free credit alerts with the three reporting agencies, contact your bank representatives to activate online monitoring and place alerts on your accounts, and regularly review your reports for unfamiliar transactions yourself. Turn on notifications and SMS alerts in your banking app. Place suspicious-login and security alerts in your email settings, too.
Be alert for phishing attempts using familiar details
Scammers will likely attempt to use stolen credentials to reach out to you with messages that look realistic and familiar, claiming to be from your bank or a platform you use and asking you to reset your password. Treat these with caution; don’t click links and don’t open attachments. Instead, check with the company directly to see if there’s a real issue.
How to protect your data from future breaches

Stop reusing passwords
If some of your passwords are used to access multiple platforms or services and they have been exposed, cyber criminals may gain access to all of those accounts at once. To prevent this from happening, use reliable password managers to generate strong, unique passwords for each account individually.
Stay informed
Add reputable cybersecurity specialists and watchdogs, such as Catalin Cimpanu and Lorenzo Franceschi-Bicchierai, to your reading list. They often report on breaches faster than PR teams issue official statements. Set up Google alerts on “Zeeroq data breach” and adjacent terms.
Scour subreddits like r/cybersecurity, r/netsec and r/scams as well as tech security forums like Bleeping Computer. Don’t forget to use breach trackers from HaveIBeenPwned or Cybernews for live updates on leaked data.
Review and reduce your digital footprint
Audit information on you that’s already out there. Google your full name, usernames and email addresses. Click through your social media accounts to see how much of your personal data is on public display. Revisit privacy settings to limit what others can see. Be especially cautious about sensitive details like your birthdate, children’s names, etc. to prevent password guessing and social engineering. Delete or deactivate old accounts you no longer use.
Use tools like Onerep to automatically remove your private information from over 230 data brokers and people-search websites—as well as Google. When your personal data is readily available online, it increases your risk of phishing, identity theft, financial fraud, and other cyberattacks. By removing your exposed information, you reduce your visibility to cybercriminals and minimize risks to your privacy.
Start your free 5-day trial with Onerep
FAQs about the Zeeroq breach
What is zeeroq.com?
It’s a domain that was registered in 2008 and has changed hands multiple times since then. It came into the spotlight in January 2024, when users started receiving notifications that their credentials had been exposed as part of a 26-billion-record breach called MOAB (“The Mother of All Breaches”). The website is now defunct, and according to breach discussions on Reddit, no users recall ever visiting it.
Was Zeeroq hacked?
There’s no evidence that Zeeroq was storing user data that could potentially be exposed. This website is more of a dump storing data leaked in multiple previous hacks, rather than the source of the stolen data.
How do I know if my data was exposed?
Check the email addresses you use against reputable breach databases, such as HaveIBeenPwned, Google’s Dark Web Report or the Cybernews Personal Data Leak Checker.
Is Zeeroq legit or safe to use?
Reputation scanners such as ScamAdviser give zeeroq.com a low trust score and mention recent phishing reports. Avoid visiting it, if possible.





Mikalai is a Chief Technical Officer at Onerep. With a degree in Computer Science, he headed the developer team that automated the previously manual process of removing personal information from data brokers, making Onerep the industry’s first fully automated tool to bulk-remove unauthorized profiles from the internet.