How to completely disappear from the internet 2025: steps to protect your identity and data

Follow these steps to safeguard your online identity and data from surveillance.
| Your personal information | Websites/Apps found on |
|---|---|
| Full Name | Social Networks, Forums, etc. |
| Email Address | Mailing Lists, Online Accounts |
| Phone Number | Public Records, Employer Websites |
| Address | Background Check Websites, etc. |
Remove social media accounts
I know – social media is probably the cornerstone of your online life. Social networks are how we keep up with friends and family and even receive the latest news about the world. But you need to disappear from the social world if you want to keep prying eyes out of your private life.
Be sure to download any photos or videos you want to keep before they’re permanently deleted from the Internet. If possible, first delete your posts and comments, then follow these steps to delete your social network accounts.
There are different methods to permanently delete your account. Start by clicking on your profile picture and selecting “Settings & Privacy,” then “Settings.” Look for “Accounts Center” – if it’s at the top left, use Accounts Center; if it’s at the bottom, use Settings.
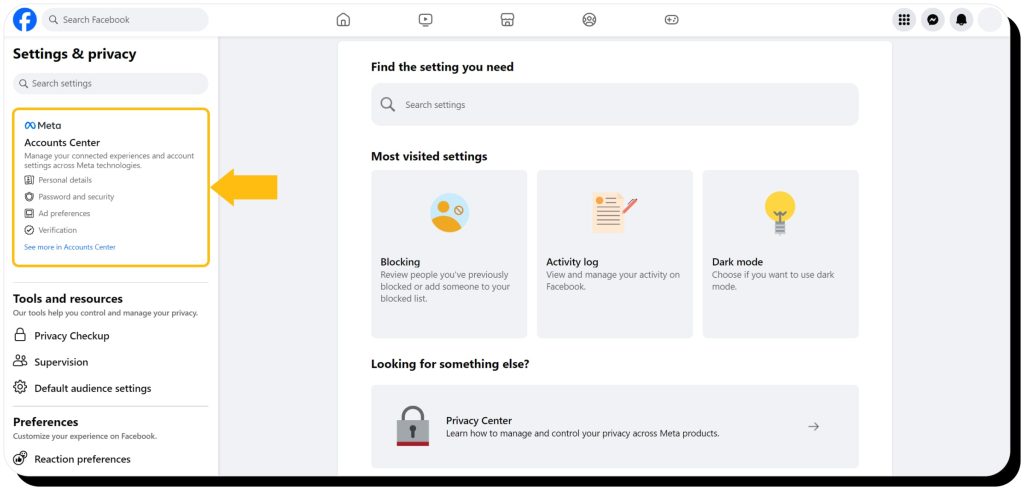
Accounts Center
- Browse to Accounts Center > Account Settings > Personal details
- Select Account ownership and control
- Select Deactivation or deletion
- Select your profile
- Select Delete account and click/tap Continue
Settings
- Browse to Settings & Privacy > Settings
- Select Your Facebook Information (or Profile Access & Control)
- Select Deactivation and Deletion
- Select Delete Account, then click/tap Continue to account deletion
X (Twitter)
- Click More in the X menu (desktop) or tap your profile picture (mobile)
- Select Settings and Support > Settings and privacy
- Select Your account > Deactivate your account
- Select Deactivate
Computer
- Browse to Instagram’s Delete Your Account page
- Choose why you’re deleting your account in the dropdown menu and enter your password
- Click Delete [username]
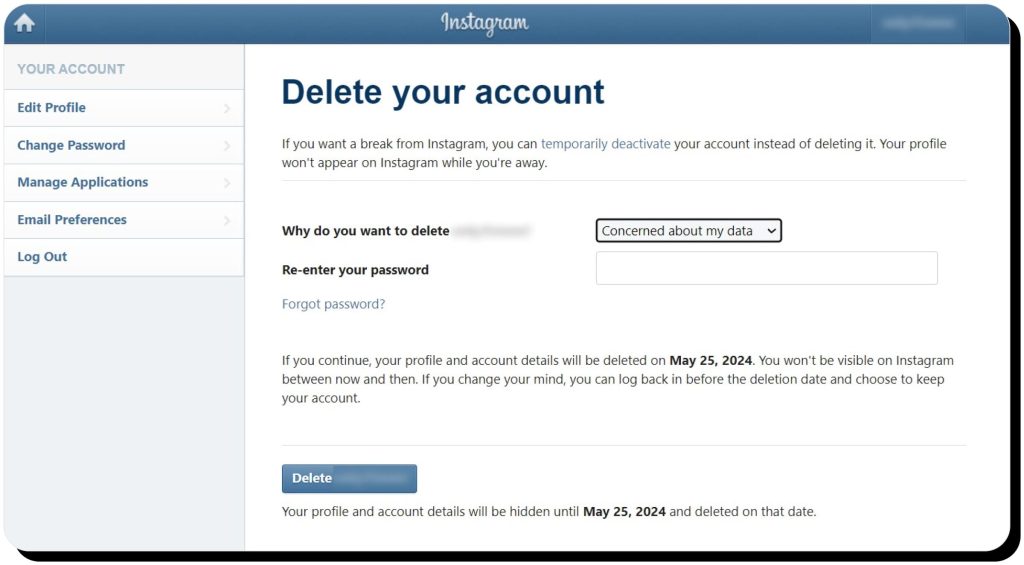
iPhone app
- Browse to your profile and open the menu
- Tap Account > Delete account
- Tap Delete account > Continue deleting account
- Choose why you’re deleting your account in the dropdown menu and enter your password
- Tap Delete [username]
Android app
- Browse to your profile and open the menu
- Tap Accounts Center > Personal details
- Tap Account ownership and control > Deactivation or deletion
- Select your account and tap Delete account
TikTok
- Open the app, tap Profile, and open the menu
- Tap Settings and privacy > Account
- Tap Deactivate or delete account
Remove old email accounts
Next, I recommend removing all the old email accounts you no longer use. Long-forgotten email addresses could be gateways for hackers to gain access to your personal details and even your financial information.
Start by identifying your old personal and business profiles. If you use Gmail, try Google’s Find your email tool, which will locate any Gmail addresses associated with your phone number, recovery email, and name.
Once you’ve identified your old emails, you can delete them one by one. Here are instructions for the most popular email services:
Once you’ve removed old email accounts, I recommend taking the following steps to secure your primary email address:
- Use strong, unique passwords. Free sites such as Strong Password Generator will help you create complex passwords in case you run out of ideas
- Enable two-factor authentication. Preferably, use an authenticator app such as Google Authenticator, Authy, or Duo
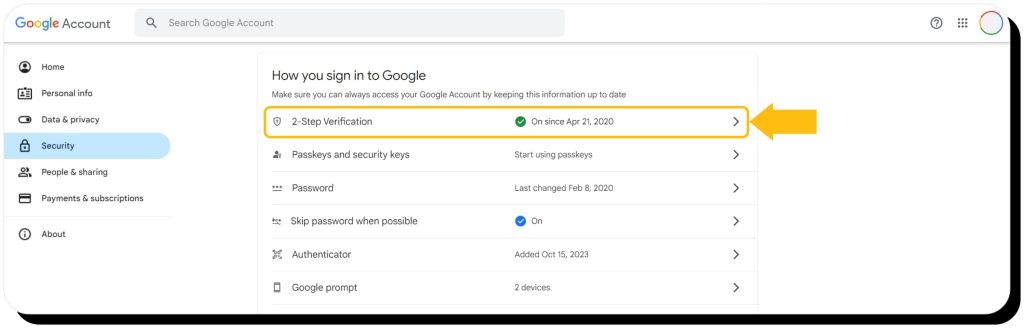
- Create a non-identifying email address. Don’t use your real name, birth year, or any other personal details in your email
- Revoke third-party access. Disable and delete any browser extensions that have access to your email and remove single sign-on (SSO) access
- If you use Gmail, you can browse to your account security settings and select “See all connections” under “Your connections to third-party apps & services,” then delete each connection
- Disable autoloading images. Hidden email images, or pixels, are used to track your activity. Disable them to prevent tracking
- Use encrypted email. Privacy-first email service providers won’t track your activity. Proton Mail is a popular option
Remove or disable outdated accounts
If you’re like most people, you have dozens of old, forgotten Internet accounts – for example, online shops, streaming services, employer websites, cloud storage services, and forum accounts. It makes sense to remove yourself from these sites to prevent unauthorized access to your data and protect yourself from potential data breaches on platforms you no longer use.
Find old accounts
- Search for your name, email, and username on multiple search engines (Google, Bing, etc.)
- Search your email inbox and archives. Try your username and common phrases used in welcome emails and shopping transactions (e.g. “welcome,” “thank you,” “your order,” “account,” and “confirm your email”)
- Check password managers, especially if you allow your browser to store login credentials
- Chrome: Settings > Autofill and passwords > Google Password Manager
- Firefox: Settings > General > Passwords
- Edge: Settings > Profiles > Passwords
- Safari: Preferences > Passwords
- Check SSO services, including Google, Facebook, Apple, Instagram, and Twitter
- Google: myaccount.google.com > Security > Sell all connections > Your connections to third-party apps & services
- Facebook: Settings > Apps and Websites
- Apple: Settings > Password & Security > Apps Using Your Apple ID
- Instagram: Settings > Security > Apps & Websites
- Twitter: Settings and privacy > Account > Apps and Sessions > Connected Apps
- Check HaveIBeenPwned, which searches for your information in known data breaches
Remove your data
Once you’ve made a list of all the old Internet accounts you can find, the next step is to remove them. Some services also offer deactivation. Note that deactivating an account typically means temporarily hiding your profile until you reactivate it while deleting permanently removes it – it can’t be reactivated or restored, so it’s the only way to truly disappear. I recommend deletion since data breaches can still expose information on deactivated online accounts.
The process typically involves:
- Logging in and checking account settings for a “delete” option
- If you don’t remember your password, you can reset it from the login page
- If you no longer have access to the email account you used, you’ll need to contact the site’s customer support
- If you can’t find the “delete” option, check the site’s knowledge base or contact their support
- Alternatively, you can search Google for [SITE] + DELETE ACCOUNT or try JustDelete.me, a directory of deletion links for many sites
If you can’t delete
- Remove sensitive information – payment info, personal data, images, everything you can
- Anonymize your data – change your name, email (create a fake email address), and any other information so that if the site is hacked, scammers will only get access to a worthless fake identity
Opt out of data broker websites
These companies – which sometimes refer to themselves as background check websites – collect and sell personal information about you. Major data brokers like Experian, Acxiom, and Epsilon mainly license data to other businesses for marketing and risk mitigation. But smaller brokers known as people-search engines sell your information to anyone willing to pay (here’s more information about the largest data brokers).
These sites use public records and various online sources to compile a huge list of information about you, including:
- Contact details (phone, email, and physical address)
- Financial and credit background
- Family members and friends
- Criminal and court records
- Location history
- Age
- Social media profiles
- Past relationships
That means anyone can use data brokers to get detailed personal information about you, from old classmates to criminals who want to steal your identity (and money) to ill-wishers seeking to stalk and harass you.
The law gives you the right to remove yourself from data brokers, which reduces your digital footprint, helps keep your information off the dark web, and protects your privacy. However, it takes a lot of time and effort to remove yourself from the hundreds of data brokers out there. The process is challenging, but not impossible – especially if you use a data removal service.
Onerep scans 230 data brokers to find your information, then sends opt-out requests on your behalf until your profiles are removed. We continually monitor each site and automatically restart the removal if they republish your information in the future.
Request for Google to remove content
Google is often the first place people rely on to find personal data about you. A quick Internet search for your NAME + CITY + STATE will likely reveal lots of information about your life.
However, Google will remove pages from its results if they contain personally identifiable information such as:
- Contact info (phone number, email, and physical address)
- Login credentials
- Government ID numbers
- Bank and credit card numbers
- Personal, restricted records (medical records)
While you can conduct online searches to find yourself and request removal, I’d say the easiest way to identify personal information on Google is to use the Results About You tool.
- Visit the Results About You page (you’ll need to sign in with a Google account)
- Follow the prompts to enter your personal details and choose how you’d like to be notified
- After a few hours, Google will start sending you notifications about what it found
- Return to the Results About You dashboard to review the results and request Google to remove any that are eligible under its Personal Content and Product Policies
- Google will then consider your request and notify you once it’s approved or denied. If approved, the offending page will disappear from the results
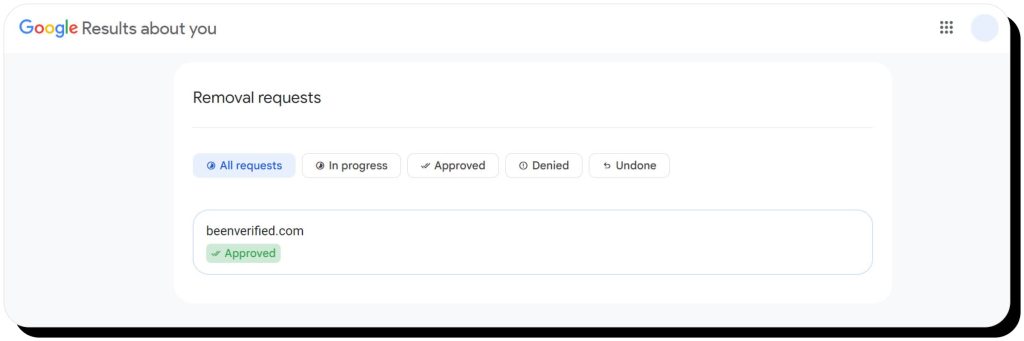
Note that it’s an ongoing process, so Google will routinely send new notifications when it finds sites and pages that publish your personal information.
Opt out of newsletters and sales alerts
If you’re like me, you’re often tempted to sign up for newsletters – and if you’ve done any Internet shopping, you’re undoubtedly on mailing lists and probably receive marketing emails in your inbox every day.
However, these newsletters and sales alerts can be used to collect and share data about you, so you should unsubscribe from any you don’t absolutely need.
There are many tools and services that make it easy to declutter your inbox and unsubscribe from newsletters. Some will allow you to opt out of emails that don’t have an unsubscribe link and even auto-block senders that do not respect your unsubscribe request.
Popular options include:
Use privacy-focused search engines
Major search engines like Google, Bing, and Yahoo track your Internet activity. For example, they track your location history, shopping behavior, search history, and other data and build comprehensive profiles to serve targeted ads and search results.
Privacy-focused search engines do not track your online behavior, allowing you to search the Internet anonymously and making it easier to disappear.
Popular examples include:
Making the switch is as simple as browsing to one of those sites instead of your normal search engine (though some, like Startpage, offer Chrome extensions).
Of course, you can take it a step further by using a privacy-first browser that protects you across the entire Internet. These browsers block tracking cookies and ads, and some even feature built-in VPNs to help you explore the Internet anonymously.
Switching is easy, as most private browsers allow you to import bookmarks, saved passwords, and extensions during installation. Examples include Brave, Duck Duck Go, and Opera.
Utilize a virtual private network (VPN)
Virtual private networks (VPNs) mask your IP address by routing your traffic through their servers, making it difficult to track your online presence and build profiles on you. They also encrypt your Internet connection to stop would-be hackers from gaining access to your private data.
Consider these tips for selecting and using a virtual private network:
- Free VPN providers might sell your data to third parties, so consider a paid VPN that’s dedicated to keeping your information private
- Choose a VPN with strong encryption, such as 256-bit AES
- VPNs can slow your Internet experience as they route your traffic through other servers, so look for a VPN that promises high-speed
- Understand what type of data your VPN logs. Some VPNs do not log any activity, some only record that you’re connected, while others log your whole Internet activity – such should be avoided
- A kill switch instantly cuts the Internet if your VPN connection unexpectedly drops. It’s a “safety valve” to ensure your information isn’t exposed, so look for a VPN with such a feature
Keep your secrets safe with encrypted messaging apps
Encryption converts your messages into code before transmission. The recipient must have the right decryption key to decipher your message back to human language. This way, only the sender and receiver can see the message – if it’s intercepted by a third party, all they’ll see is a jumbled block of code.
Encrypted messaging apps provide secure communication, making it virtually impossible for anyone on the Internet to intercept and read your personal messages.
Whether you need to protect trade secrets for your business or just want to keep your personal messages away from prying eyes, I recommend using one of these encrypted messaging apps:
Avoid downloading and using apps
We all like to download apps on our phones, but many apps put your privacy at risk because they record your personal data, track your behavior, and even share your information with third-party companies. You need to be careful about which apps you download and:
- Delete any unnecessary apps (and close related accounts)
- Review permissions settings for the apps you keep. Revoke access to your data, camera, contacts, and microphone, and disable any kind of tracking or sharing
- Keep apps updated to prevent malware attacks
- Use web-based versions instead of installed apps where possible
Adjust your device’s location settings
Device location sharing allows others to track you where you go. That includes:
- Advertisers who use your location to serve targeted ads
- Law enforcement agencies that use your location to identify your proximity to a crime
- Ex-partners and criminals who could use your location to find, stalk, blackmail, or harass you
In fact, the FTC recently prohibited one data broker from sharing sensitive location data (such as visits to domestic abuse shelters, medical facilities, and places of worship) after the company sold that data without informed consumer consent.
To stop apps, data brokers, and other third parties from accessing your location information, I strongly recommend turning off location services. Here’s how to do it:
Remove and decline cookies
Websites use cookies to identify you. They work by placing small files in your browser and on your computer when you visit a website. When you return later, the website recognizes you.
Cookies are useful for things like remembering your shopping cart and auto-filling your login credentials – but they can also be used to track your online behavior and serve targeted ads. They can contain lots of personally identifiable information such as your name, address, phone number, and email in addition to your browsing history.
Here’s how to delete, decline, and block cookies to avoid being tracked on the Internet:
- Decline all cookies if prompted when you browse the Internet
- Delete and block cookies in your browser
- Chrome
- Edge (Clear cookies and block cookies)
- Firefox (Clear cookies and block cookies)
- Safari
- Install an ad blocker that also blocks trackers. Options include AdBlock Plus, uBlock Origin, and Ghostery, which has a “never consent to cookies” feature
Don’t forget to run antivirus scans often
Viruses can infiltrate your devices, apps, and software, then access your documents and photos, log your keystrokes, and track your Internet behavior. Be sure to install a good antivirus and frequently run scans.
Most antivirus software allows you to run automatic scans daily, which I recommend. These scans typically run in the background when your devices are idle, and they’ll notify you if they identify a threat. No news is good news, but it’s still a good idea to check results every week to ensure your antivirus is scanning on schedule.
Use different passwords for each online account
I’m as tempted to use the same passwords across numerous platforms as anyone, but it’s truly critical to use different passwords for each online account. If you use the same password for multiple services, a single hack or data breach could grant criminals access to all of them. Your passwords should be strong and diverse to prevent anyone from guessing them. Use a password manager such as Dashlane or Proton Pass to generate and store secure passwords, and be sure to enable multi-factor authentication to add another layer of security to each account.
FAQ
Can police monitor your Internet activity?
Police can monitor anything you do publicly, such as activity on your social media accounts, but they generally need a warrant to track your IP address, location history, and other data points. However, some law enforcement agencies purchase information from data brokers instead of getting a warrant.
Who is tracking my Internet activity?
Your Internet Service Provider (ISP), data brokers, advertisers, browsers, apps, search engines, and law enforcement agencies can all track your online activity.
Is deleting search history a crime?
In general, deleting search history is not a crime. However, in rare circumstances it could be considered obstruction of justice; for instance, if search history is erased in an attempt to hide or destroy evidence of a crime.
Can someone find the deleted search history?
It is possible to recover deleted search history even if it no longer displays in your browser. Methods include data recovery tools that can access hidden logs stored on your computer, a system recovery that restores your device to an earlier state that still has saved searches, and account activity data stored by your search engine or ISP.




Dimitri is a tech entrepreneur and founder of Onerep, the first fully automated data removal service. Top cybersecurity CEO of 2021 by The Software Report.