Smishing: definition, examples, and how to stay safe

Smishing, short for SMS phishing, is a type of social engineering scam carried out through text messages. With about 65% of the global population using SMS for messaging, it’s easy to see why scammers use this communication channel as one of the most effective for phishing attacks.
Just like in other types of scams, smishers exploit people’s trust and the urgency created by quick, official-looking phone messages. Scam texts are instantly visible, easy to interact with, and leave almost no room to verify the sender before the victim is prompted to click on the malicious link contained within. Once they do, though, their identity and financial information can be stolen and exploited by bad actors.
This article details the smishing meaning, how it’s different from other forms of phishing, the types of smishing attacks, and what you can do to protect yourself from smishing perpetrators.
Smishing meaning and definition
What is smishing? Smishing combines SMS (short message service) with phishing to describe a cyberattack delivered as a text message. Instead of phone calls (vishing) or emails (traditional phishing), smishing scams arrive as a phone text impersonating a trusted company or individual—like your bank, a delivery services provider, a government agency, or a friend—to trick you into clicking a malicious link and revealing your sensitive information.
A smishing message typically asks you to:
- Verify suspicious account activity
- Track or reschedule a “missed” delivery
- Confirm your shipping address or other personally identifiable information
- Respond with “yes” or call the sender back
- Pay unpaid taxes or bills
- Claim a refund, prize, or reward
The ultimate goal of smishing is always to make you share your personal details, such as banking logins, credit card data, Social Security number, etc. or download malware to your device.
How smishing works
Smishing scams come in different forms, but they all start with an unsolicited urgent text message that may look either personal or official depending on the purpose.
Common smishing stages include:
- Obtaining the victim’s contact details. Most of the time, these can be looked up online on public data brokers and people-search websites, but many scammers go to great lengths to buy leaked datasets on real people from dark web websites.
- Impersonating trusted institutions or people. Scammers carefully choose whom to impersonate to sound credible. These include banks, government agencies, postal services, or even your employer or business partner.
- Creating urgency. Smishing messages mimic official and urgent communication from authorized senders that can’t be easily ignored and demand prompt action, for example, “Your account will be locked unless you verify immediately.”
- Including a malicious link or phone number to call back. These are used to take the victim to spoofed websites and “call centers” that steal sensitive information, such as payment card details and digital account credentials, or to download malware to the victim’s device.
- Requesting personal information. Whether on a malicious website or on the phone with the scammer, you’ll be required to enter or share your personal information under credible excuses. Once you do this, these details will be stolen and potentially exploited for the scammer’s financial gain.
- Monetization. The ultimate stage of a smishing attack where scammers exploit your information—withdraw money from your bank account, make fraudulent purchases, commit identity theft, or sell the data to other scammers.
Smishing vs. phishing vs. vishing: what’s the difference?
Phishing is an umbrella term for all kinds of social engineering scams that trick you into giving up personal information. Most phishing attacks are email-based, so other terms came up to account for variations:
- Vishing stands for voice and phishing, meaning phishing attacks enacted through phone calls and voice mail.
- Smishing is an SMS-based variation of phishing carried out through text messages.
In practice, these phishing types can overlap. For example, you may get a Norton LifeLock scam email asking you to call back the provided phone number to cancel an unexpected charge on your account.
Smishing examples
Here are some common smishing scenarios and how they play out in real life:
Delivery scams
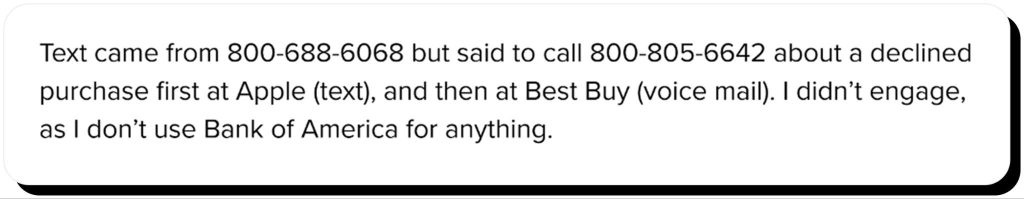
Scammers make use of the popularity of postal services and impersonate well-known delivery companies such as UPS, USPS, and FedEx. This is just one example of a USPS scam, alerting the user to a missing shipping address:
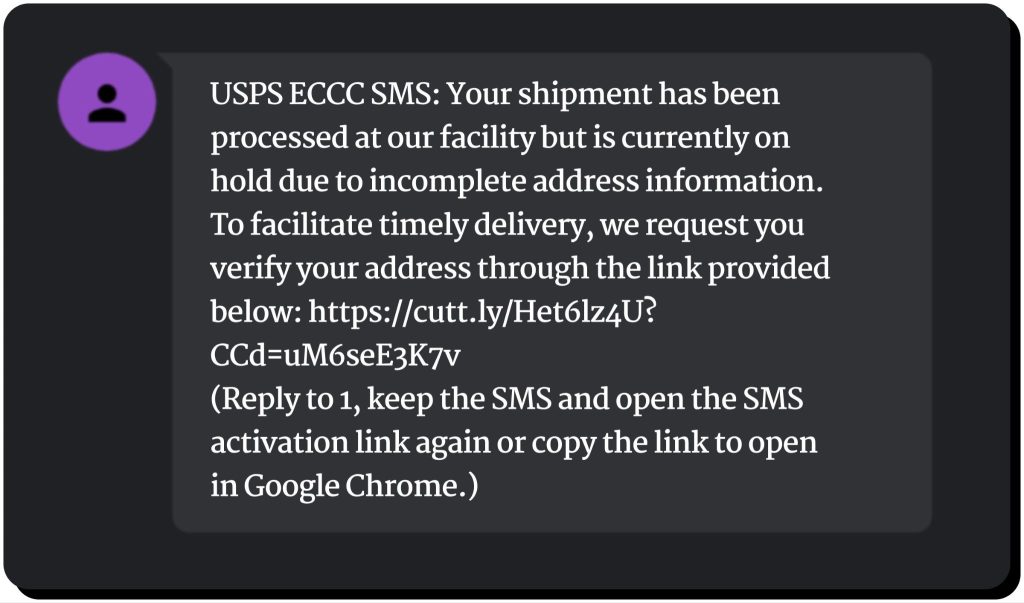
Delivery smishing texts often include a link disguised with a link shortener that takes the user to a malicious website designed to steal the information entered, such as a home address, USPS login credentials, or payment card details.
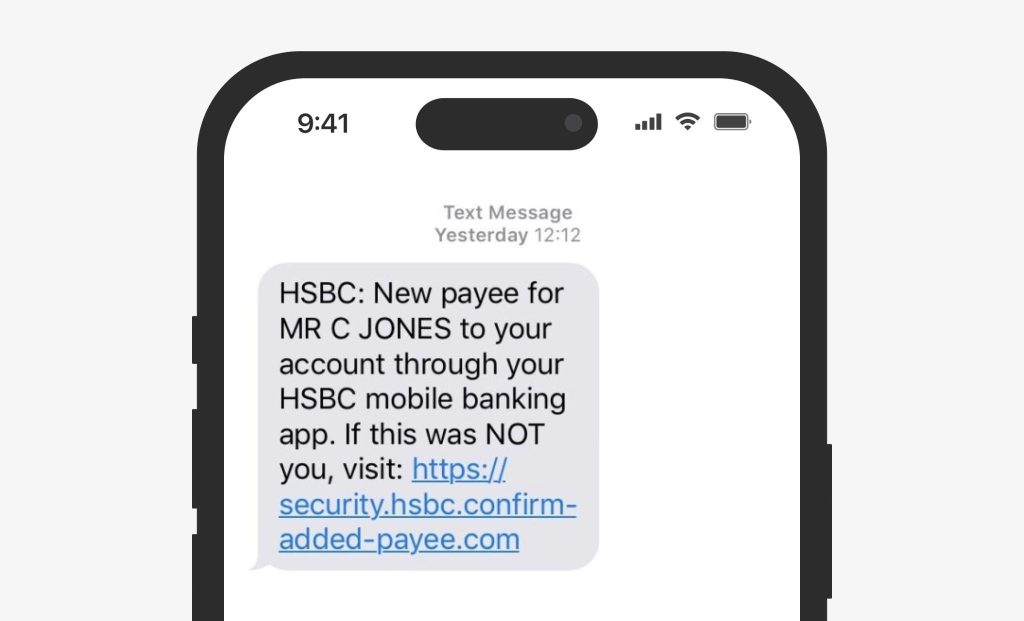
Bank alert smishing
Smishers imitate legitimate bank alerts using spoofed phone numbers and urgent language that notifies the recipient about a suspicious transaction, the need to verify their account, or to take another account-related action. The message features an URL loosely disguised as one from the bank’s official website but in fact being a malicious clone of the bank’s login page. Once you enter your bank login credentials, scammers will be able to drain your account within minutes.
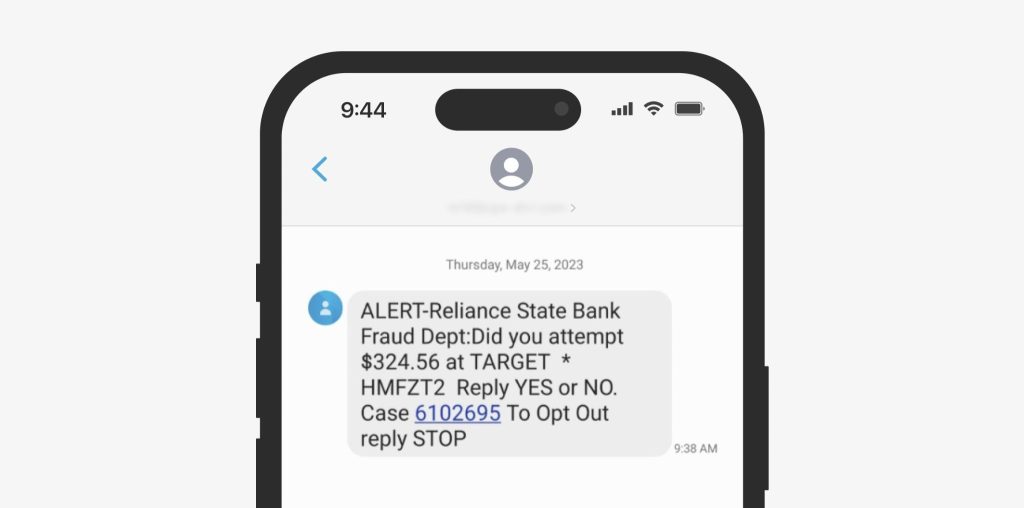
Sometimes these fake bank alerts feature a prompt to enter “yes” or “no” in response. This trick is used to filter active phone numbers and check if the target is engaged enough to continue the scam. If you reply to such a message, you’re likely to get a phone call from scammers trying to harvest your personal information.
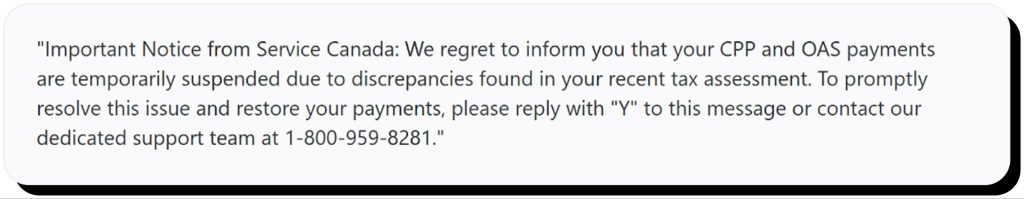
Tax or government impersonation smishing
These smishing texts allegedly come from a national tax authority, such as the IRS, or a government agency and contain an official-looking message about an issue with your taxpayer documentation or your legal status. Some messages are designed to be intimidating, citing fake case numbers and threatening a legal investigation or even arrest.
The logic follows typical smishing techniques, where the recipient is asked to click a link, respond to the message, or call back using the listed phone number. In every case, this will connect the victim to the scammers looking to defraud people of money and steal their sensitive information.
Customer support refund scams
This smishing scam often begins with a message that sounds helpful, for example, “Your refund is approved. Please confirm your details here: [phishing link].” On the surface, this may look like a generous correction, but the true purpose of this smishing message is to get you to provide your payment card details so the scammers can steal them.
One common example of customer support smishing scams is Xfinity impersonation, where users get text messages alerting them to a problem with their Xfinity account, a charge due, or a failed payment request, and requiring them to verify their identity or log in to their Xfinity account.
Some scammers take it further and install malicious software, such as keyloggers, via spoofed websites, as well as gain remote access to their victims’ devices via specialized software, like in AnyDesk scams.
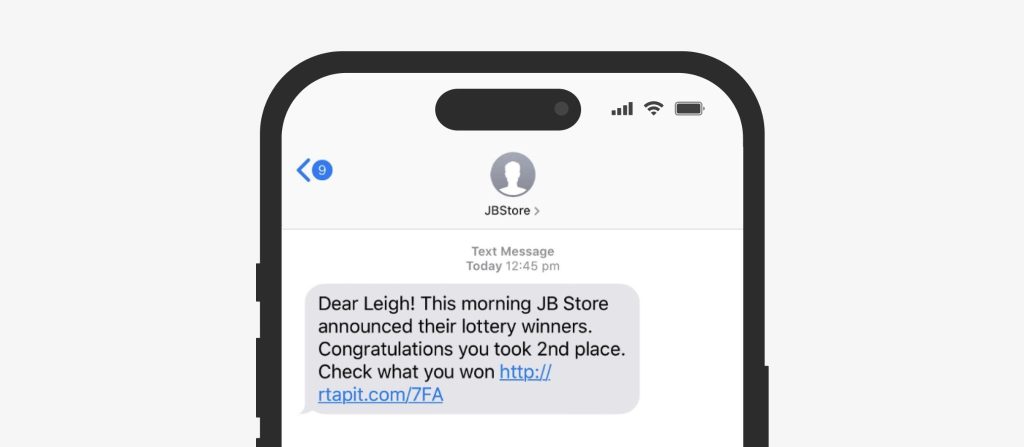
Prize and lottery smishing
To lure victims in, scammers craft exciting messages announcing a sudden lottery or giveaway win. The promise of an unexpected reward, as well as the urgency, nudges people to click without thinking, and this is what scammers are looking for. They direct their targets to malicious websites and request them to enter personal information, download an app to “unlock” their prize, or even pay for “processing” or “shipping” fees in exchange for the prize. Of course, there’s no prize—the only outcome is personal information and money stolen for nothing.
Why smishing is dangerous
There are many contributing factors that make smishing so dangerously effective.
On average, SMS texts have an astounding 98% open rate—much higher than that of emails, which linger at around 2-3% at best. This makes scammers’ exploits all the more effective when done through this medium.
At the same time, sending out smishing messages is automated and fairly cheap, so attackers are able to send out massive amounts of fraudulent messages at a low cost. At such a scale, smishing attacks are capable of producing dramatic financial results for scammers. For example, Chinese smishing syndicates are reported to have compromised about 115 million U.S. payment cards between 2023 and 2024.
Because people are used to short informal texts as well as occasional SMS-based communication from brands, they may overlook red flags that would stand out in an email or phone call. Older and less tech-savvy people are particularly vulnerable to this type of attack, as they might not recognize a threat.
Finally, smishing scams are getting more convincing, adapting to what works best with millions of victims worldwide. Generative AI technologies are also at play here, helping scammers craft more and more effective and realistic messages.
How to recognize a smishing scam
If you see an unsolicited text message that raises your suspicion, here are the warning signs to confirm it’s smishing:
- The sender’s number is generic, unfamiliar, or looks spoofed. It may display a generic company name like “Delivery Services” or just be a phone number. You can double-check by verifying the official contact details of the sender’s alleged company online.
- There’s a link you’re prompted to click or a request to respond to the message with “yes” or “no.” The link is typically disguised via a link shortener or has extra characters and words uncommon for the real company’s website. In some cases, you’ll be asked to copy and paste the link URL in your browser.
- The message creates urgency and asks you to act immediately. There might be alarming language, a deadline for your action, and threats in case you don’t respond.
- The message contains typos, weird grammar, or language that feels off for official branded communication.
How to protect yourself from smishing
Smishing scammers prey on easy targets that show low cybersecurity awareness, act impulsively, or are driven by fear, curiosity, or greed. To make sure you’re not one of these targets, make sure to follow these simple yet effective practices:
- Don’t click on links in suspicious and unexpected messages from unknown senders. Even if the sender poses as a legitimate business, don’t trust such links anyway.
- Verify information independently. For example, if you get a fraud alert from your bank, contact the phone number on the back of your payment card to verify if it was compromised.
- Keep your phone updated and enable spam filters. Install the latest security patches to make sure no software loophole can be exploited by scammers. Many smartphones and carriers support spam filters that can block smishing texts automatically.
- Never respond to texts with your personal information, be it PINs, one-time verification codes, credit card data, or account credentials.
- Report suspicious texts to your carrier and/or local regulatory and anti-fraud bodies so they can maintain an up-to-date database of scammers’ phone numbers and domains.
What to do if you fall for a smishing scam
If you think you’ve been scammed by smishers, act immediately to minimize the potential damage:
- Stop interacting with the text, don’t click any links or reply.
- Take a screenshot of the text and the sender’s ID for further scam reporting.
- Block the sender and report the text as spam by copying and forwarding it to 7726 (SPAM), then delete the message.
- If you clicked the link in the smishing message and entered your credentials, change them for all the affected accounts, including any reused passwords.
- If you shared your financial details or banking account login with the scammers, contact your bank to set up fraud alerts and disable and reissue any affected payment cards.
- If you sent money to the scammers, you may be able to dispute the transaction as fraudulent with your bank.
- Report the scam to the Federal Trade Commission in the U.S. or your local anti-fraud or consumer protection authority.
- In case the smishing text impersonates a real company, you may contact this company directly and file an impersonation report with them.
- If your personal data has been stolen, monitor your bank account, email, and credit card transactions for suspicious activity.
- Run a trusted antivirus to detect any potential malware that could have been installed on your device.
FAQs about smishing
What is smishing in simple terms?
Smishing is a phishing scam delivered as a text message that tricks you into sharing your sensitive information and payment card details with the scammers or into unknowingly downloading malware to your device.
What happens if I click a smishing link?
If you click on a malicious smishing link, you might be taken to a spoofed website that steals your login credentials or payment card information, or you might inadvertently authorize a transaction, or install harmful malware on your device.
How do I report a smishing text?
You can report it as spam by forwarding it to 7726 or file a complaint with your local anti-fraud authority, such as the Federal Trade Commission in the U.S. or Action Fraud in the U.K.
How can I tell if a text message is a smishing attempt?
If the message is unsolicited, is from an unknown sender or a phone number that looks spoofed, contains a link disguised with a link shortener, requires urgent action from you, and asks for your personal information, it almost always is a smishing scam.
Is smishing the same as phishing?
Smishing is phishing done through text messages, so yes—smishing is a sub-type of phishing and thus technically is a phishing scam.




Dimitri is a tech entrepreneur and founder of Onerep, the first fully automated data removal service. Top cybersecurity CEO of 2021 by The Software Report.