Social engineering scams: How they work and how to stay safe

Social engineering scams are crimes that target people above all, not just computers or data. Instead of hacking the code, scammers emotionally manipulate their victims, exploiting trust, fear, anxiety, and curiosity to trick them into handing over money or sensitive information.
These scams are rising because we leave digital trails in everything we do online—via email, cloud services, and messaging apps, giving scammers endless opportunities to impersonate someone we trust.
In this guide, you’ll learn what social engineering is, how it works step by step, its most common signs and types, and how you can protect yourself from social engineering attacks.
What are social engineering scams?
Social engineering scams are criminal exploits that use psychological manipulation instead of technical hacking. Scammers typically pretend to be a trusted person or business representative (your manager, bank, a courier, or tech support) and push you to reveal sensitive information such as digital account credentials, credit card information, identity details, give access to your data or system, or send money to them under a plausible excuse.
These scams come in many forms—via emails, text messages, DMs, phone calls, or in-person contacts, but all of them exploit human trust and fallibility, crafting convincing, often personalized scenarios that make the target more likely to believe them.
Social engineering scammers target both regular people and businesses, so it’s recommended that everyone learn to recognize the common social engineering tactics and the variety of scams to dodge the attacks.
The mechanics of social engineering scams
How do social engineering scams work?
The first step is gathering intel. Scammers research their targets online or in real life, gathering details (full name, job roles, vendors, digital services used) from social media, data broker sites, data breach dumps on the dark web, and company pages.
The second step is creating the pretext. Scammers craft a believable story (pretext) explaining why they’re contacting you and why the action they require from you is justified.
The third step is contact and pressure. They reach out via a suitable communication channel (phone, email, DM, etc.), often creating a sense of urgency, fear, or exclusivity to make you lower your guard and respond with the desired action.
The fourth step is hook and interaction. Unknowingly following the scammer’s instructions, you click a link, open a file, share a code, or send money, granting them access to the information or funds they’re after. In other words, taking a small action with big consequences.
The fifth step is extraction or access. As a result of your action, scammers get access to sensitive data, account credentials, or money, exploiting it for their personal and financial gain.
The sixth and final step is escaping. Scammers vanish after a successful exploit, sometimes after just one interaction, in other cases after continuous abuse or by exploiting the initial target’s network of social connections and colleagues.
Common types of social engineering scams
Here are the top types and examples of social engineering scams that run across the internet, sometimes spilling over into real life. They target all sorts of individuals and businesses, sometimes taking as little as 60 seconds for the victim to fall for them. Recognizing them early is key to preventing potential damage.
Phishing, smishing, vishing, quishing
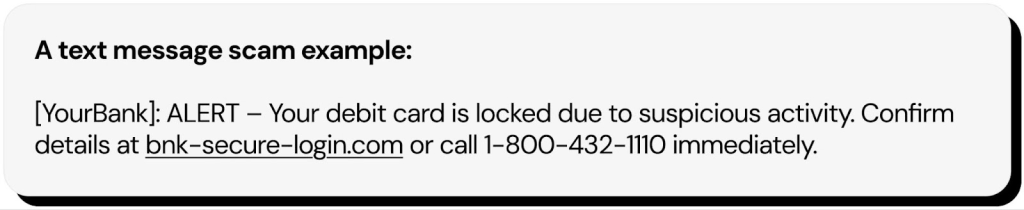
By far the largest category of social engineering scams, phishing, smishing, vishing, and quishing all feature a malicious message disguised as legitimate, often impersonating a common digital service or a well-known company that the user is likely to trust without extra verification.
- Phishing uses fake emails urging password resets, fake invoice payments, or responses to urgent notifications. Some well-publicized examples of social engineering scams include Norton LifeLock scam emails and Best Buy’s Geek Squad subscription renewal emails.
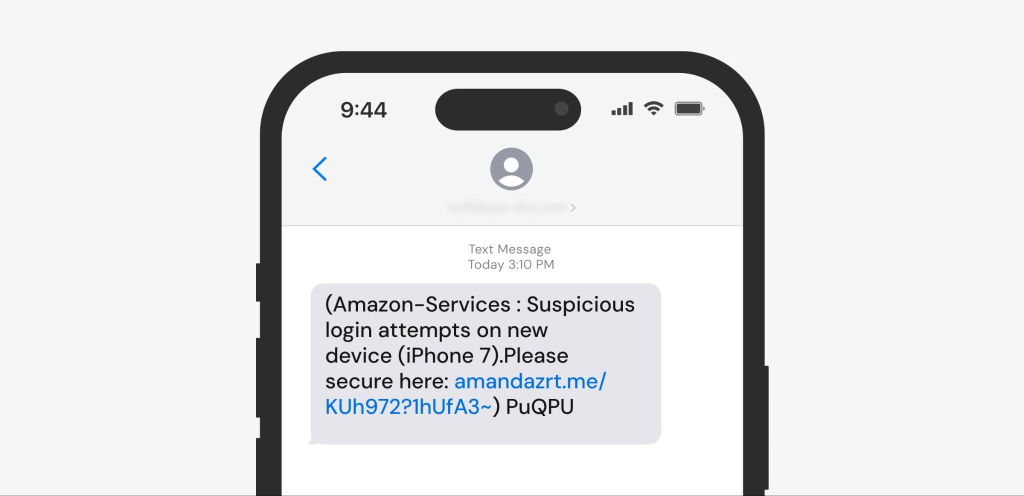
- Smishing uses SMS texts that mimic banks, government agencies, postal services, or commercial companies, warning users of issues with their order or account. Examples include Xfinity impersonation scams and USPS scam texts.
- Vishing uses voice messages and phone calls to press targets into sharing their personally identifiable information that can be further used for identity theft or to persuade them to transfer money. Some examples include Medicare scams and scams targeting timeshare owners.
- Quishing is the category of QR code scams that run across social media, messenger apps, online marketplaces, and public places. Scammers share fake QR codes or place them over the real ones to mislead users and redirect them to malicious websites that steal money or information. This technique is often used in Facebook Marketplace scams and those involving instant payment methods, such as in Zelle scams.
Business email compromise (BEC)
A form of spear-phishing, or a phishing attack targeting a particular person(s) versus mass targeting, BEC can be devastating for businesses. According to the IC3’s Internet Crime Report, business email compromise was the second most expensive crime type in 2024, accounting for over $2.7 billion in losses.
A common BEC scenario is CEO fraud, where a scammer impersonates an executive and asks an employee to wire money, send gifts, or update a vendor’s payment details. Coming from a high-profile manager, such requests are more likely to be followed through without the recipient questioning their legitimacy.
AI deepfake impersonation
With the rise of artificial intelligence-based deepfakes, executive impersonation has taken an alarming turn, as scammers are now able to convincingly impersonate real people in phone and video calls. Last year, a multinational company from Hong Kong lost $25.6 million due to a deepfake impersonation of their Chief Financial Officer during a video conference call.
Baiting
Baiting uses attractive hooks to “bait” victims, such as free software downloads, “exclusive” media files, or mysterious USB drives left in public. Once used or downloaded, these files secretly install malware or allow scammers to access digital systems.
For example, you might find a USB drive in your office parking lot. If you plug it into your work computer, you might unknowingly install spyware that steals your corporate system credentials.
Romance and sextortion scams
Romance scammers, or catfishers, start by building an emotional connection online, then ask for money under false pretenses. In some cases, this scam takes the form of sugar daddy, momma or baby scams, where victims are exploited financially in return for a promise of companionship or intimacy that is never fulfilled.
Sextortion scammers trick or coerce victims into sharing intimate content with them and then threaten to expose it to the victim’s friends, relatives, and colleagues unless paid.
Investment scams
Investment scams can start on social media, through an “accidental” contact in a messenger app, or on a dating platform, and quickly develop into investment advice promoting a fraudulent scheme, often involving cryptocurrency. These schemes are said to offer “guaranteed high returns” and encourage victims to send money to what later turns out to be scammers’ accounts.
A long-term variation of an investment scam is called pig butchering, where scammers develop a close emotional connection over time only to gain just enough trust to persuade the victim to invest more and more before disappearing with the money.
Money mule schemes
Criminals recruit people through fake job posts or other means to transfer or hold funds in their bank accounts, turning them into unwitting participants in money laundering schemes. In many cases, these funds come from scamming other people, and the victims of money mule schemes may face real legal consequences for acting as accomplices, even if they didn’t know what they were involved in.
Quid pro quo (tech support swap) scams
In this social engineering scam, attackers pose as IT staff or tech support providers, offering an upgrade, a free fix, or a prize in exchange for sharing login credentials or verification codes, or for installing software. In some cases, these tech support impersonators may request remote access to your device, like in AnyDesk scams, and guide you through installing spyware or stealing your personal information during the remote session.
Tailgating, or piggybacking
Tailgating, or piggybacking, is a variation of physical social engineering where scammers follow authorized personnel into secure areas on-site, pretending to be delivery workers, contractors, IT staff, or colleagues, thereby bypassing security checks. They may carry boxes, wear uniforms, or act rushed to avoid suspicion.
Watering-hole attacks
Hackers compromise a legitimate site frequented by company employees (for example, a vendor portal, a corporate intranet, or industry association). Visitors are tricked into entering their login credentials or downloading malware that compromises and spies on their devices. As a result, cybercriminals can gain access to internal systems, lock the owners out, and demand ransom in return for data access.
How to recognize a social engineering attack
Despite the variety of social engineering attacks, it’s still possible to catch them in time if you know their common red flags. Look out for the following signs:
- Urgency and scare tactics. Scammers use language like “act now,” “deal ends in 15 minutes,” “account locked” or similar phrases to make you act fast without thinking.
- Unusual sender or communication channel. Be wary of unsolicited emails, texts, phone calls, DMs from strangers, and email domains that appear misspelled or unusual.
- Unusual or sensitive requests. If an unexpected message or a stranger you’ve never met in person asks you to click a link, enter your personal information, grant them remote access to your device, or send a payment, it’s most likely a scam.
- Pressure for secrecy and confidentiality. Social engineers often ask that you keep communication confidential and private, especially in corporate environments to avoid exposure.
- Inconsistencies and weird language. Scammers don’t always get the details right. Look out for gaps in their story, mismatched details, poor grammar and spelling, and unusual wording, especially if they’re trying to impersonate someone you know.
- “Too good to be true” offers. To ignite their targets’ curiosity or fear of missing out, scammers may offer exclusive deals that expire soon, discounts, refunds, giveaway and lottery prizes, or items that are priced greatly below the market.
How to protect yourself from social engineering scams
The following best practices apply whether you’re targeted as an individual or a company employee:
- Always verify the sender, caller ID, and message contents by stopping the communication and contacting the official channel independently.
- Verify the email domain and link URLs by hovering over them without clicking. Look for signs of misspelling and addresses that don’t match the official ones.
- Use strong unique passwords in combination with a trusted password manager.
- Enable phishing-resistant multi-factor authentication (MFA) using passcodes or app-based codes instead of SMS.
- Keep your devices updated and run trusted antivirus software in the background at all times.
- Lock down social media by setting your profiles to private and limiting the information publicly available about you.

What to do if you’ve fallen for a social engineering scam
If you’ve fallen for social engineering fraud, stop engaging with the scammers immediately. Don’t reply, click more links, continue with a remote access session, or install software.
After disengaging, take the following steps to secure your identity, accounts, and information:
- Disconnect from the internet and run a full malware scan.
- Change passwords for any affected accounts.
- Contact your bank or credit institution to freeze your credit and cancel or reverse any unauthorized transactions.
- Set up fraud alerts with your bank or payment card provider if you shared your financial data.
- Notify your workplace if the fraud involved your corporate system or data.
- Collect evidence and report the fraud to the respective authorities. In the U.S., these are the Federal Trade Commission, The FBI’s Internet Crime Complaint Center, and IdentityTheft.gov.
- Monitor for suspicious activity. Watch out for unexpected password resets, account logins, or signs of identity theft. For the latter, you can set up automated identity theft monitoring using specialized services.
- Warn others. Share the incident with your family, friends, and colleagues so they can raise their guard.
How Onerep helps you stay safe online
Social engineers leverage their victims’ personal details to craft convincing pretexts, and in many cases they don’t even have to steal that information as it freely resides on people-search and public data broker websites.
Onerep reduces your risk of exposure to social engineering scams by finding and removing your personal information from 230+ websites. With less data available, it’s harder for scammers to:
- Impersonate companies or services you use as a customer
- Target you with personalized phishing scripts
- Mimic your boss or vendor convincingly
- Answer your account recovery questions
Start your free scan with Onerep now.
FAQs
What is social engineering fraud?
Social engineering fraud uses psychological manipulation and deception to trick people into giving access, sensitive information, or money to malicious actors without the victim knowing they’re dealing with criminals.
How do social engineering scams work?
Attackers research their victims, create convincing pretexts for reaching out, contact them using pressure and urgency, and manipulate them into taking a desired action, such as clicking a malicious link or transferring money to scammers’ accounts.
What are some examples of social engineering scams?
Social engineering scams vary from basic phishing and smishing attacks to sophisticated CEO fraud, romance scams, money mule schemes, and fraudulent investment advice that result in the victim losing money and/or compromising their personal data.
How can I recognize a social engineering attack?
Watch out for messages using urgency, secrecy, unusual requests, lookalike web addresses, unsolicited notifications, and unexpected attachments. Verify via a second channel before acting.
Why are social engineering scams so effective?
Social engineering is effective because it exploits people’s innate qualities and emotions such as trust, curiosity, fear, anxiety, and desire to be loved. In just under a minute, scammers can hook their targets with a carefully crafted message, getting what they want almost instantly.





Dimitri is a tech entrepreneur and founder of Onerep, the first fully automated data removal service. Top cybersecurity CEO of 2021 by The Software Report.