Truist data breach: how to secure your financial information after a bank hack

Truist, one of America’s top 10 largest banks, got tangled up in two alarming cybersecurity scandals in the past two years. The 2023 data breach affected approximately 65,000 people, while the 2024 third-party incident put a few million people at risk.
The breaches may have compromised both personal and financial information of Truist employees and customers, including bank transactions, dates of birth (DOBs), social security numbers (SSNs), and more. Security incidents like these significantly increase the risk of ID theft and financial loss for those affected. This article will break down how the Truist data breach played out and discuss what you can do to protect your financial and personal information.
Understanding the Truist data breach incidents
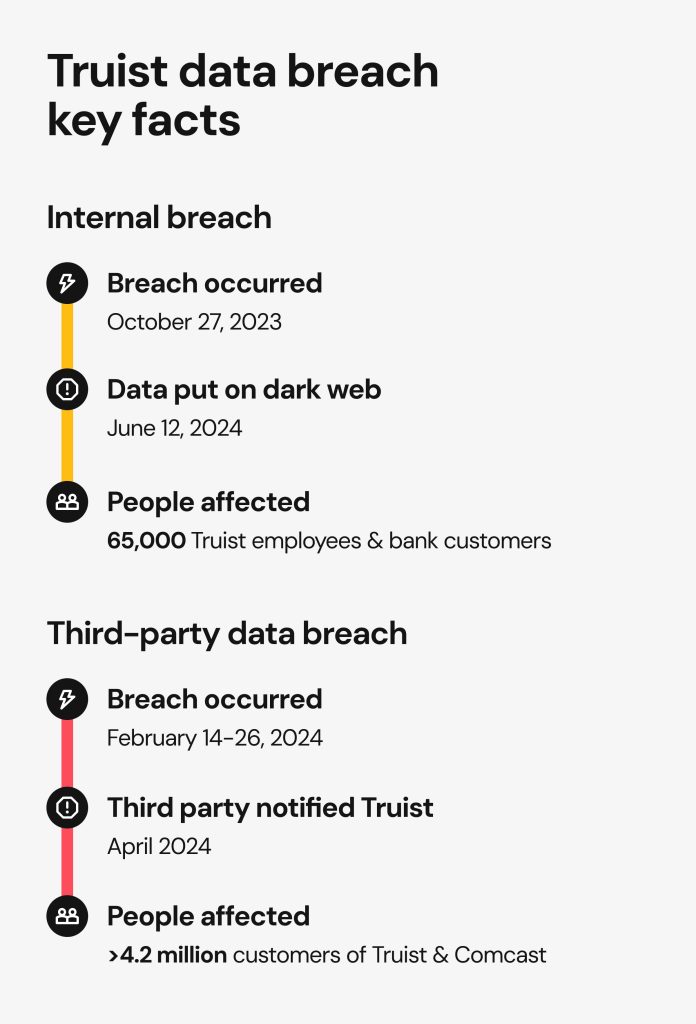
Internal data breach
- Date(s) the breach occurred: October 27, 2023
- Date(s) stolen data appeared on sale: June 12, 2024
Third-party data breach
- Date(s) the breach occurred: February 14-26, 2024
- Date(s) the breach was discovered by the third party: February 26, 2024
- Date(s) the third party notified Truist Bank: April 2024
What happened in the 2023 Truist Bank scandal?
Truist Bank systems fell victim to the hacking attack on October 27, 2023, exposing the private data of 65,000 bank employees and a smaller number of bank customers.
Stolen information resurfaced on the dark web in June 2024, when the hacker group Sp1d3r put the entire bulk of the stolen info on sale for $1 million. They claimed to have accessed not only confidential professional and personal information of Truist Bank employees but also the customers’ bank transaction details and Interactive Voice Response (IVR) source code for the bank’s IVR funds transfer system, which could be exploited to elicit more data and carry out phone-based scams.
How did the 2024 Truist data breach happen?
Financial Business and Consumer Solutions (FBCS), a debt collector affiliated with Truist Bank, experienced a data breach between February 14 and 26, 2024. The company notified Truist Bank of the incident in April 2024, warning that sensitive information of about 1.9 million people may have been compromised.
Further investigation revealed the number to be far larger. According to a data breach notification submitted by FBCS to the Maine attorney general’s office, over 4.2 million customers of Truist and Comcast were affected.
What types of information were exposed?
The following sensitive information may have been compromised during the two Truist security breaches:
- Personal identifiers, like names, street addresses, DOBs, SSNs, driver’s license numbers, and other state identification info.
- Financial information, such as account numbers, balances, and bank transaction history.
- Truist internal data (2023 breach), including the files of 65,000 employees, along with the source code for the bank’s IVR funds transfer system.
- Health-related information (2024 FBCS breach), like medical claims information, provider information, clinical information (such as medical diagnoses, treatment, and medications), and/or health insurance information.
When both your identity and financial details are exposed, impersonation becomes much easier. For example, someone can use your DOB/SSN and the last four digits of your account number to bypass identity verification and reset your online banking password.
Truist’s response after the breaches: did they do enough?
After the 2023 Truist data breach scandal, the company hired outside security consultants to carry out a thorough investigation and make sure their systems were protected. The bank initially notified a small number of clients and sent out additional notifications later on. The impacted customers were offered free identity protection services. It’s still unclear what kind of security issue got Truist hacked, as the company never provided details.
In response to the 2024 incident, FBCS stated in its breach notification that it launched an immediate investigation. “This matter has also been reported to federal law enforcement. As part of FBCS’s ongoing commitment to the security of information on our platform, we also implemented additional safeguards in a newly built environment,” the report says.
Truist began notifying customers about the breach several months after the incident. They offered their users credit monitoring services by Experian, Equifax, and TransUnion, along with two years of free protection services. The exact number of affected customers was never disclosed.
Because the breach occurred within the FBCS systems, not its own, Truist downplayed the attack and shifted responsibility to the third-party vendor. This approach, combined with limited transparency and inconsistent communication, stirred public trust and raised broader concerns about how financial institutions handle cybersecurity risks. Similar patterns in other recent financial and banking breaches involving loanDepot, Amex, Ally and Chase highlight a growing need for clearer breach response protocols and better safeguards to protect sensitive financial data.
Truist customers’ reactions: confusion, frustration, and class actions
The two Truist data breach incidents led to significant public concern, particularly among customers who turned to Reddit and other social media platforms to share their experiences and frustration about the incident, the delay in breach notifications, and inconsistent customer support. One Reddit user described calling Truist to verify the legitimacy of the breach notification letter: “…the rep said it was NOT LEGIT. Seemed odd to me, and so I asked to talk to someone in the operations/risk management/fraud/identity theft division. The CS rep resisted this, told me there was nothing in my account about any such letter, etc., so I had to insist. Repeatedly. With voice raised, etc. Finally, the CS rep gave me a Truist ID theft number to call – and that rep verified that the data breach letter WAS LEGIT.”
Customers also noticed unauthorized devices being added to their accounts, as well as PayPal accounts getting linked. Some got locked out of banking apps due to too many login attempts. Others ended up moving funds or closing their accounts.
Truist Bank faced two class action lawsuits filed in the North Carolina federal court (by Stephen Ruffin and Marshall Boyd) related to the 2023 data breach.
Although FBCS faced several lawsuits and filed for bankruptcy after the 2024 security breach, there are no publicly reported class action lawsuits against Truist Bank as of April 2025. Given the scale of that data breach, people might still take legal action in the future.
Why banking data breaches are a major risk
The exposure of highly sensitive information poses significant privacy risks, including:
- Identity theft, where criminals use stolen personal data to open new accounts, apply for loans, or file false tax returns in your name.
- Unauthorized access to bank accounts or account takeover, when attackers use personal identifiers and financial data to bypass basic security checks and directly access your banking accounts.
- Fraudulent transactions, which may involve cybercriminals using stolen banking or credit card information to make transactions and wire transfers.
- Phishing scams, where detailed personal information allows social engineers
to create convincing emails or messages designed to trick you into revealing credentials or clicking malicious links. - Repeated targeting, where your breached data can resurface multiple times on the dark web, leaving you vulnerable to ongoing scams and fraud. Criminals may also commit synthetic identity theft by combining your real personal details with fake information to create new identities, which can then be used for criminal activities.
- Credit damage, which inevitably occurs when scammers use your information to open new credit cards, apply for loans, or even attempt to secure mortgages. All this damages your credit score and may prevent you from getting legitimate funding in the future.

Has your data been exposed? Here’s how to find out
If you are not sure whether you’ve been affected by the Truist data breach, look for a breach notification letter that the bank sent to its customers. When you do this, make sure you check all official channels of communication your financial institution uses and keep in mind that these notifications may arrive a few months late.
Here is what to do if you suspect that your sensitive personal or financial information has been exposed:
Check for suspicious activity on your accounts
Keep a close eye on your bank activity, accounts, and new credit inquiries. Charges for things you didn’t buy or withdrawals you didn’t make could be a sign of identity theft.
Monitor the dark web
Stolen confidential information is likely to surface on the dark web, sooner or later. Check if your email address has been part of a data breach by visiting haveibeenpwned.com.
You can also set up a dark web monitoring profile with Google. This way, Google will send you a notification if your personal information, such as your name, address, phone number, email, username, and password, is detected on the dark web.
Steps to protect your banking and financial data after a breach
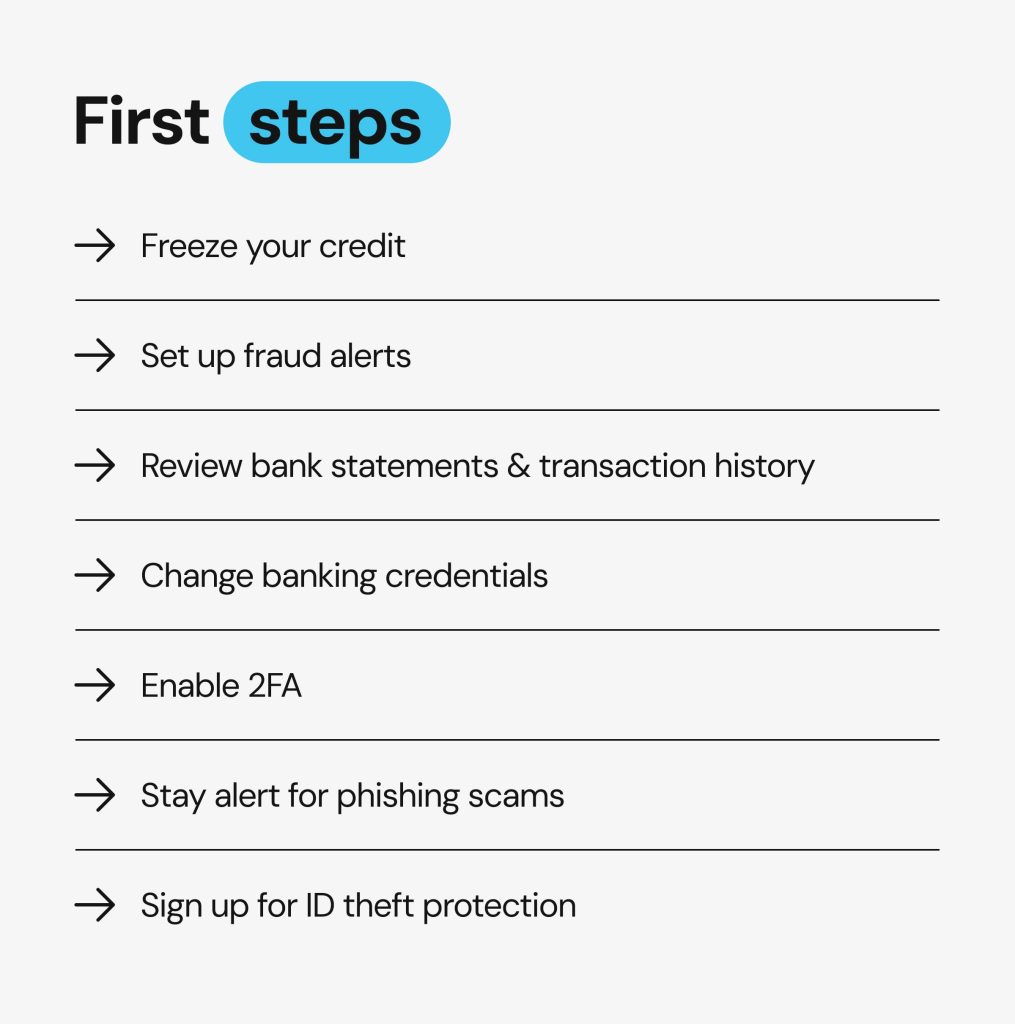
Freeze your credit
Freezing your credit makes your credit report unavailable to creditors and prevents bad actors from getting new credit cards, loans, or mortgages in your name. The freeze is free, can be lifted temporarily, and is probably the best protection against fraud when your data has already been compromised.
You will need to request a credit freeze with each of the three major credit bureaus (Equifax, Experian, and TransUnion) via phone call, email, or online form.
Set up fraud alerts
If you set up fraud alerts, potential lenders will receive an alert note attached to your credit report and conduct additional verification and security checks before approving your credit. You can enable fraud alerts for free with all three major credit reporting agencies via phone or online.
Review bank statements and transaction history
Regularly review your bank and credit card statements for any suspicious or unfamiliar activity, transactions, new cards issued, or new credit opened. If you notice any odd activity, report it to your bank immediately.
Change banking credentials
After a breach, make sure to update your banking credentials (online banking password, PIN, and security questions). Choose a password that is strong and unique, ideally using a password manager, and avoid reusing it on different platforms.
Enable 2FA
Two-factor authentication (2FA) adds an extra layer of security to your online accounts and banking apps. It requires a second verification step (like a code sent to your phone) when logging in. Whenever possible, use authenticator apps (like Google Authenticator) instead of SMS codes.
Stay alert for phishing scams
There is often a rise in phishing attempts after a data breach. Bad actors may pose as your bank, credit bureau, or even government agency to lure you into revealing additional confidential information. Be wary of any emails, texts, or phone calls that contain unknown links or attachments, request urgent action, or ask for sensitive data.
Sign up for ID theft protection
While identity theft protection services don’t prevent identity theft, they can be useful when it happens. A specialized service provider can help you with setting up fraud alerts or freezing your credit, dealing with banks and creditors, restoring your account, and even provide you with insurance coverage against potential financial losses.
Long-term measures for financial cybersecurity and personal data protection
Here is how you can protect your personal and financial information and make it as difficult as possible for criminals to access or misuse it.

Avoid storing card info online
Storing card info on your browser and favorite shopping sites is convenient, but may put you at risk of fraud if that platform ever gets breached. Instead of storing the info, enter your credit card details manually.
Use virtual cards
Virtual cards generate a temporary card number that hides your actual bank account or physical card number. If your bank offers this feature, you may be able to create a unique number for each online transaction. Third-party apps also let you set spending limits, restrict usage to a single merchant, set expiration dates, or cancel the card at any time, which adds extra layers of control and protection.
Audit your digital footprint (and take back control)
Your digital footprint is made of all the information shared (by you and others) on the internet. To strengthen your safety, it’s critical to review it regularly and make sure the readily available information on you is as limited as possible.
1. Search yourself online
First, find out what is out there.
- Google your name, email addresses, phone numbers, and usernames.
- Use quotation marks for more accurate results.
- Search in image and news tabs, and across different search engines (Google, DuckDuckGo, Bing).
2. Review social media posts and privacy settings
Social media platforms are a treasure trove of personal information that cybercriminals can exploit to gather more data about you.
- Set profiles to private wherever possible (especially Facebook, Instagram, and TikTok).
- Remove or hide sensitive details like your DOB, children’s names, etc., as they can make password guessing easy.
- Delete old posts or photos that expose too much personal information.
3. Revisit old accounts
- Use a password manager or email search to find old accounts you’ve forgotten.
- Delete or deactivate any you no longer use (look for a “close account” option in settings).
- Reclaim usernames from unused platforms to prevent impersonation.
4. Check people-search and data broker sites
Look for your personal information on people-search sites like Spokeo, MyLife, Whitepages, and BeenVerified that aggregate and display your details like addresses, phone numbers, relatives, credit scores, and plenty of other data bits.
These websites are publicly accessible, which means cybercriminals can use them, too. Once a fraudster gets a few pieces of your highly sensitive financial data from a breach or the dark web, they can dig up more personal bits on broker sites. A combination of such details makes it easier to steal your identity, access your accounts, and otherwise defraud you.
Onerep offers a free data broker scan that checks 200+ people-search sites to show where your data appears. To protect your privacy, you can manually request removal or use Onerep’s automated service to do it for you.
FAQs
What should I do if my information was exposed in the Truist data breach?
If your data has been exposed in the Truist data breach, you can take immediate action by freezing your credit or setting up fraud alerts, monitoring your bank statements and transaction history, changing your banking credentials and enabling 2FA, staying alert for phishing scams, and signing up for ID theft protection. In the long run, you can protect yourself by not storing card info online, using virtual cards, and reducing your digital footprint.
How do I know if my banking data is at risk?
To verify whether your data has been compromised, contact your bank and check if you received any official notifications, keep a close eye on your accounts, and monitor the dark web.
Can I remove my personal information from the internet?
Yes, you can remove (or at least reduce) your personal information from the internet, but it takes time, effort, and persistence. The first step is to identify what data is publicly available, then follow the opt-out procedures on people-search and data broker websites. However, removing your data from the dark web is far more difficult, and in many cases, impossible once it has been exposed.





Mikalai is a Chief Technical Officer at Onerep. With a degree in Computer Science, he headed the developer team that automated the previously manual process of removing personal information from data brokers, making Onerep the industry’s first fully automated tool to bulk-remove unauthorized profiles from the internet.