Poshmark data breach: what happened and how to secure your account

Most of us shop through online marketplaces and retail apps — in fact, about 86% of purchases now happen there. This makes platforms like Amazon and Poshmark especially attractive to cybercriminals looking to steal customer data.
In 2018, a Poshmark data breach exposed account details for millions of users. Then in 2025, researchers uncovered a third-party cloud leak affecting multiple marketplaces including Poshmark, highlighting how vendor misconfigurations—not just direct hacks—can put shoppers at risk. For a broader look at this trend, see our guide on third-party breaches affecting Amazon users and an overview of the recent Walmart data security incidents.
This article explains the Poshmark incidents: what happened, what data was exposed, who is at risk, and the exact steps buyers and sellers can take right now to secure their accounts and reduce future exposure.
Overview of the Poshmark data breach incidents: 2018 and 2025 in focus
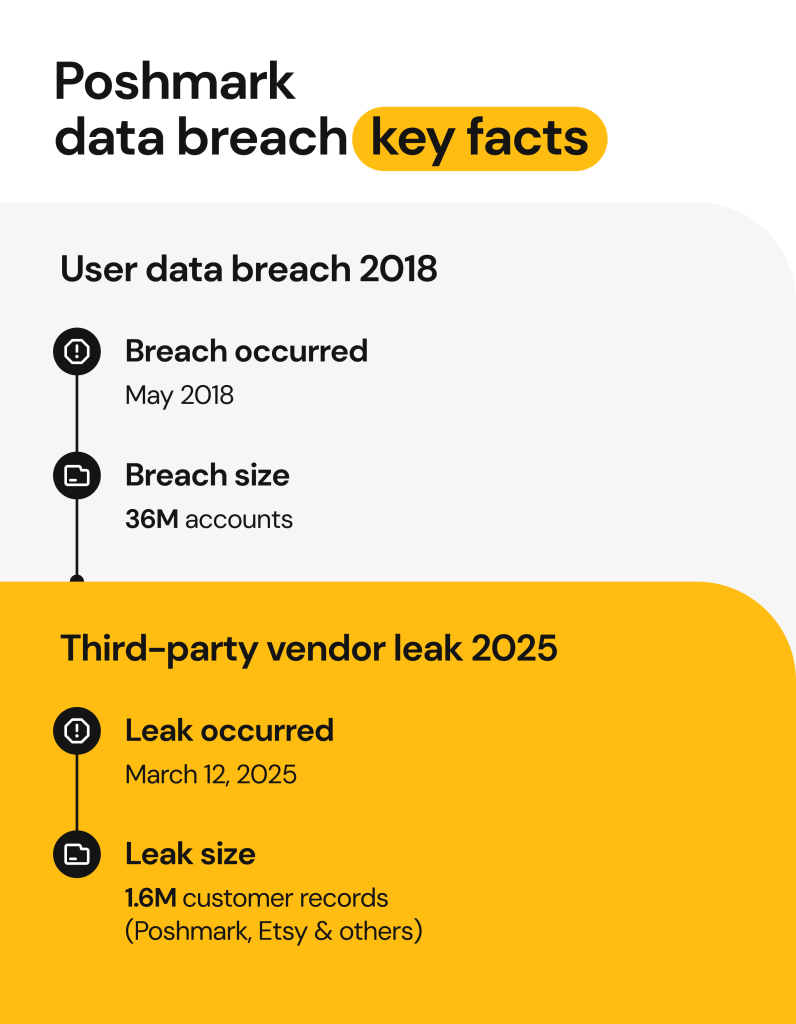
The Poshmark hack of 2018: 36M accounts exposed
Poshmark is a social marketplace where users can buy and sell fashion items from their mobile devices. The company disclosed a security incident in 2018 involving unauthorized access to its U.S. users’ database. While they didn’t reveal any details about the attack method publicly, officials believed the compromise was a result of password reuse.
Multiple cybersecurity news sites, including TechCrunch, confirmed that roughly 36 million user accounts were affected by this Poshmark data breach. The cyberattack exposed user information, including:
- Email addresses
- Full names
- Poshmark usernames
- Genders
- Limited location information
Threat actors also accessed data involving bcrypt-hashed passwords with unique salts. While bcrypt encryption is designed to resist brute-force attacks, some hashed passwords were later cracked and used in attempted account takeovers. A subsequent BleepingComputer report confirmed the scale of the Poshmark breach, crediting researcher Jim Scott and his collaboration with Have I Been Pwned for uncovering over one million cracked Poshmark accounts being sold for $750.
Fortunately, attackers did not access any financial data or home addresses. Still, the incident underscored how storing personal information on e-commerce platforms can expose users to risk—and how password reuse amplifies the damage.
Poshmark data leak 2025: vendor misconfiguration exposes details
Third-party vendors have an essential role in e-commerce operations. They typically manage cloud storage or handle shipping confirmations. No matter their role, these vendors sometimes fail to secure their systems.
Cybernews researchers uncovered an example of this vendor-related issue in 2025 after finding two unsecured Microsoft Azure Blob Storage containers that held shipping confirmations from several online retailers in HTML format. That means that this Poshmark data breach stems from an interconnected cyberattack, affecting the TikTok Shop and several other platforms.
The most affected individuals came from the U.S., but bad actors also targeted accounts in Canada and Australia. Compromised data includes:
- Full names
- Physical addresses
- Email addresses
- And limited Poshmark order details
Cybercriminals didn’t access any credit card information, and there was no indication the leak came from the company’s internal systems.
The 2025 Poshmark leak reinforces the reality that sensitive data may be at risk even when platforms aren’t connected. For comparison, the Ally data breach and DoorDash data breach are further proof of how unsecured databases managed by vendors or weak data safety protocols lead to data compromise.
What data was compromised in the Poshmark breaches, and why it matters
The unfortunate trend of vendors storing unencrypted data continues to impact consumers across the e-commerce industry. In Poshmark’s case, two security incidents highlighted risks for both buyers and sellers. A table below shows how numerous breaches magnify the risk of exposure.
| Exposure Incident | Incident Type | Data Compromised | Exposure Risk Notes |
|---|---|---|---|
| 2018 Breach | Unauthorized system access | Email addresses, usernames, full names, genders, clothing size preferences, locations, some bcrypt-hashed passwords, Poshmark preferences (email and push notifications) | Even with encrypted passwords, criminals can reuse or cross-reference exposed details with other breaches, increasing the odds of identity-correlation or credential-stuffing attacks. |
| 2025 Leak | Vendor storage misconfiguration | Full names, physical addresses, emails, shipping confirmations | When combined with earlier breach data, exposed emails and order details provide attackers with more context to craft convincing scams. |
For sellers, exposed order details make them a high-value target for refund scams, fake “buyer issue” messages, or impersonation attempts. Leaked addresses and order confirmations also raise the risks of phishing emails, malicious links, and social-engineering attempts for buyers. Financial data is a high-priority target for threat actors.
Even without it, the Poshmark data breach gives scammers everything they need to impersonate trusted shopping platforms. When third-party vendors fail to enforce proper data protections, each compromised dataset adds new context for cybercriminals, allowing them to target consumers effectively with tailored scams.
How did Poshmark respond to the security incidents?
The 2019 response
Once company officials confirmed and publicly disclosed the 2018 Poshmark security breach, they hired cybersecurity firm Kroll to investigate it. Following a thorough investigation, Poshmark stated that no financial data or physical addresses were exposed. Since sensitive user profile information was compromised, the company advised users to change passwords immediately, later forcing password resets for users who hadn’t accessed their accounts recently.
Poshmark also reminded users to set up two-factor authentication, stop reusing passwords on multiple websites, and stay alert to suspicious messages attempting to exploit exposed information. According to a report from HaveIBeenPwned, the company strengthened its defenses against cyberattacks by improving internal monitoring systems, applying stronger encryption methods, and auditing its network security controls.
2025 challenges
Cybersecurity risks have evolved since the 2018 Poshmark breach. Still, the recent incident presented a different kind of challenge: protecting user data in a connected environment where vendors manage critical storage and communication systems. E-commerce companies like Poshmark may secure their networks, but a vendor mistake puts customers at risk.
The Cybernews research team found that several industry heavy-weights, including Etsy, Embroly, and Poshmark, had over 1.6 million customer records compromised by the breach. A Vice article confirmed that the breach occurred on March 12th, 2025, though it didn’t compromise Poshmark’s systems.
Further challenges arose when researchers couldn’t determine the owner of the exposed data. This development raises concerns about accountability and leaving users uncertain about how their data is being handled, or if similar vulnerabilities exist elsewhere.
Public frustration about the security breaches
Poshmark’s official response to the breach was polished and measured. It emphasized response measures, including robust encryption and limiting exposure, but on Reddit, the tone was different. Consumers often turn to the platform first when security breaches happen.
Users debated over data retention policies, focusing on what happens if criminals expose those records in future breaches. The incidents left many wondering how much information platforms hold and how little visibility there is for long-term data handling practices.
Ongoing threats to Poshmark users
Your Poshmark account hacked
Having your Poshmark account hacked can be more damaging than it first appears. Beyond losing access to your listings, attackers may access your connected bank accounts, stored payment details, and private conversations. Some individuals report hackers using their compromised accounts to message other users, post fake listings, or redirect packages.
Recovering your account can be time-consuming and sometimes, users never regain control of their data.
Credential stuffing attacks or account takeovers
Even if the breaches didn’t affect you, you’re still vulnerable from reusing the same login across multiple sites. A Bitwarden study on password management evolution, states that 52% of users reuse the same password on various sites. This makes credential-stuffing attacks a frequent cause of account takeovers, allowing attackers to change linked bank accounts, steal payment info, and even forward payments elsewhere.
Phishing and social engineering campaigns
When scammers steal data, they can use it to create more convincing messages. They exploit order confirmation numbers, addresses, or Poshmark messages, to send emails designed to trick users into clicking malicious links or sharing login credentials. For more guidance on spotting and avoiding these schemes, read this post on Poshmark scams.
Identity or address-based fraud
The Poshmark breaches left attackers a treasure trove of sensitive data ideal for launching impersonation, refund, or shipping scams. Sellers are more at risk of fraud concerning fake “buyer issues” because these requests cite privileged shipping details. Buyers may face shipping scams where items are redirected or swapped for items not on the listing.
Exposed addresses can lead to larger identity risks, as attackers compile information from breaches and open sources to build more complete target profiles. Learn more about what you can do to limit exposure in this guide about the hidden impact of data brokers on privacy and security.
What to do if your Poshmark account was hacked and your data was exposed
Signs your account may be compromised
Warning signs that your account was compromised may be subtle at first, but ignoring them may lead to consequences that aren’t so easy to miss. Spotting unusual activity early will help you prevent further damage. Some red flags may include:
- Unauthorized login notifications claiming “someone changed your password.”
- Missed earnings, notifications of changed payout methods, or altered banking details.
- New listings you don’t recognize, messages from buyers and sellers you didn’t contact, or purchase orders you didn’t create.
- Being locked-out of your account or receiving a request to verify your identity.
- Other Poshmark users reporting suspicious messages coming from your profile.
Take these steps immediately
- Change your password on Poshmark and any other websites where you reused the password. Always use a random set of uppercase and lowercase letters, symbols, and numbers to create unique passwords.
- Schedule a malware and antivirus scan, especially if you use Apple devices as they are linked. Criminals may use infostealer malware, which contributed to the recent Apple data leak.
- Setup two-factor authentication from your Poshmark settings. Authenticator apps and trusted hardware keys offer stronger protection than SMS methods.
- Relink your payment accounts to Poshmark. Re-syncing the payment methods on your Poshmark account means a chance to review your bank account or PayPal details for evidence of tampering.
- Report the incident to the Poshmark support team. Always include proof of unauthorized activity. The faster you do this, the better your recovery options may be.
- Be ready to receive more spam messages or deal with other scam attempts. Attackers will likely reference real order details to trick you. Don’t interact with any messages unless you confirm it’s from the app.
Tips to protect your Poshmark account going forward
- Schedule your password changes. Set a notification on your calendar to change them every 90 days to reduce the risk of exposure.
- Avoid connecting Poshmark to your social media accounts. The platform connects to Pinterest, X, Facebook, and more. If one account is compromised, threat actors may gain single-sign-on access to the others.
- Audit and remove app permissions, especially from platforms you aren’t using anymore. This will remove access for tracking and automation tools that increase your risk.
- Verify Poshmark-related URLs and emails before logging in or replying to messages. Phishing campaigns use this tactic to trick individuals with similar domain names.
- Use different emails for buying and selling items as this may help contain the impact of a data leak.
- Start managing your personal data exposure risks. Reduce the information linked to your identity and make yourself less visible to cybercriminals.
Explore 15 efficient ways to protect your privacy.
How Onerep helps reduce your personal data exposure
Data brokers quietly collect, store, and sell personal information—often without your knowledge or consent. When cybercriminals access that data, they can combine it with breached records to craft convincing phishing scams or commit identity theft. It’s a recurring pattern: once your information enters the digital marketplace, reclaiming privacy becomes an ongoing effort, not a one-time fix.
Onerep continuously scans over 230 data broker and people-search sites to identify where your personal details are exposed. It then submits automated removal requests on your behalf and keeps monitoring until each removal is verified. Regular re-scans ensure that any new or relisted records are detected and deleted promptly.
Clearing these records significantly reduces your chances of becoming a cybercriminal’s next target. While no service can eliminate risk entirely, minimizing your data exposure online remains one of the most effective ways to protect your privacy long-term.




Mikalai is a Chief Technical Officer at Onerep. With a degree in Computer Science, he headed the developer team that automated the previously manual process of removing personal information from data brokers, making Onerep the industry’s first fully automated tool to bulk-remove unauthorized profiles from the internet.