TransUnion data breach: what happened, how to safeguard yourself and prevent your data exposure

In late July 2025, TransUnion—one of the three major U.S. credit bureaus alongside Equifax and Experian—confirmed a data breach that impacted over 4.4 million customers, including residents. The company revealed that the attacker, linked to the ShinyHunters hacking gang, gained unauthorized access to a third-party application for customer support storing personal data.
This security incident is especially alarming as the credit bureau handles financial and identity data of over a billion consumers worldwide, including 260+ million U.S. citizens. Even limited leaks from such data-rich entities can affect personal data security and privacy.
This guide breaks down what happened in the TransUnion data breach, why it matters, and how to safeguard your credit and identity from misuse in the wake of such incidents.
Overview of the latest TransUnion security breach
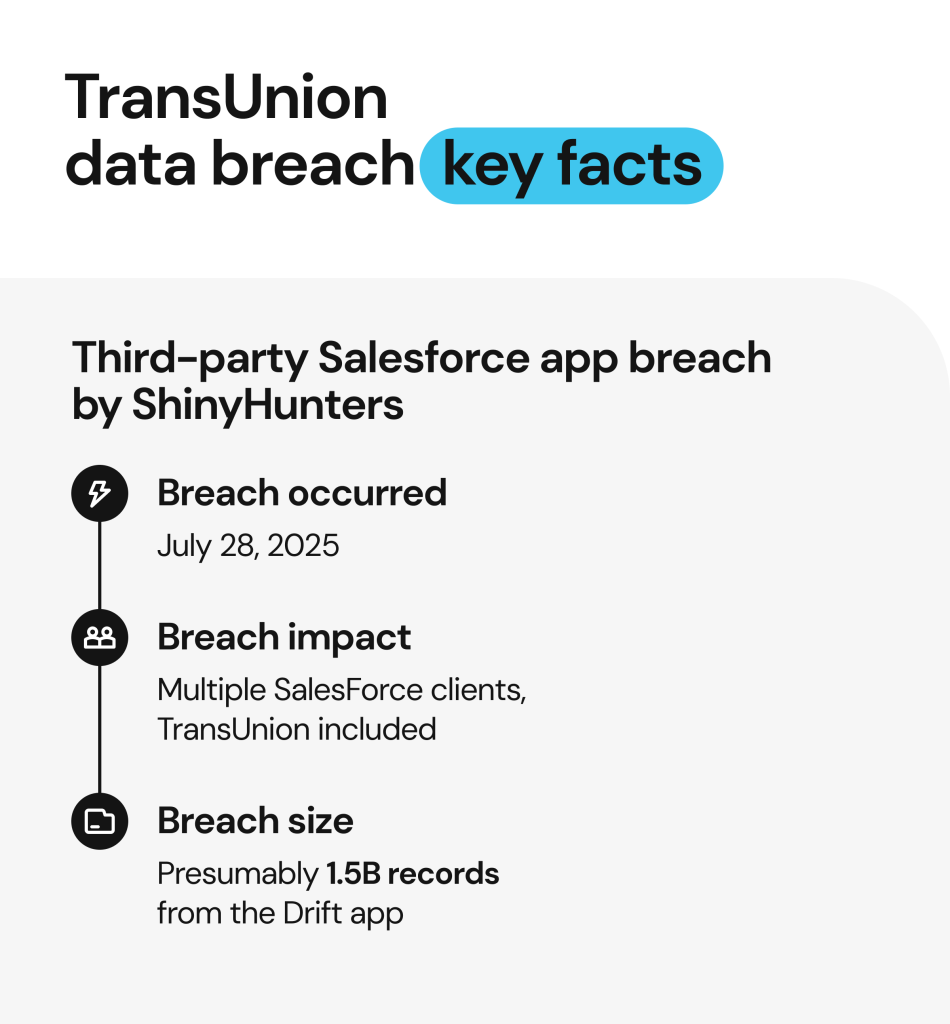
What happened in the TransUnion data breach?
The latest TransUnion data breach happened on July 28, 2025, and was discovered two days later on July 30. The threat actors claimed 13 million records were exposed in total, with about 4.4 million U.S. consumers affected according to the official data breach notification.
TransUnion cited unauthorized access through a third-party Salesforce-connected app as a cause of the breach. The incident is attributed to ShinyHunters—the same hacking group behind the 2024 Twilio hack and the recent Google data breach, as well as the ones targeting Ticketmaster, Allianz, AT&T, and other global firms.
Salesforce confirmed that their core application hasn’t been compromised. However, the breach happened through a broader OAuth token theft and social engineering exploiting Salesforce integrations with the third-party Salesloft Drift application and targeting multiple corporate clients over the course of July-August 2025. Salesforce has since disabled Drift integrations and removed the app from its AppExchange cloud marketplace.
In October 2025, it became known that the attackers behind this large-scale breach issued a ransom demand to Salesforce, threatening to publish the stolen data publicly. In response, Salesforce refused to pay the ransom, while the hackers launched a dark web data leak website listing 39 out of 760 allegedly breached companies as their extortion victims. The stolen data is said to contain a compilation of the records stolen from the Drift app with presumably 1.5 billion records.
Was TransUnion hacked directly?
Officially, TransUnion hasn’t been hacked directly. The company has since confirmed their core credit database and customers’ credit score data hasn’t been compromised. However, the hackers were able to obtain unauthorized access to a third-party app and steal millions of personal data records related to the company’s customer support function, making it an indirect yet successful hacking attempt.
The TransUnion breach shows how third-party technology and compromised internal access controls are becoming a growing risk vector across enterprise ecosystems. As a result, even such “support-level” data leaks can lead to serious harm including phishing, impersonation, and identity theft, especially as fraudsters combine this data with other public or leaked information.
Who was affected and what information was exposed?
| How many people affected | 4,461,511 U.S. consumers |
| Data exposure scope | Customers who interacted with TransUnion customer support or requested free credit reports |
| Global exposure | Possible. The hacked Salesforce instance may have contained limited international data |
| Exposed data fields | NamesBirthdatesPhone numbersEmail addressesBilling addressesUnredacted Social Security numbers |
| Not affected | Credit reportsCore credit informationCredit scores |
What TransUnion is doing in response
According to TransUnion’s sample data breach letter to consumers, the company is engaging in “robust and proactive security measures” to minimize the potential risks of a similar incident happening in the future. They’re also conducting a forensic investigation with third-party cybersecurity firms and law enforcement.
While Salesforce has done their part of securing third-party integrations, TransUnion is also reviewing its third-party access controls and tightening app configurations, as are many other high-profile companies affected by the breach.
In addition, TransUnion is offering 24 months of free credit monitoring and fraud assistance through Cyberscout (a TransUnion company). This is a standard remediation measure that’s often required from the affected companies by law. For example, IDX data breach notifications also contain a free offer of 24 months of credit monitoring for victims of data theft.
Consumer letters detailing the data breach and available remediation measures were mailed to all affected TransUnion customers starting from August 26, 2025.
TransUnion data breach reactions and expert commentary
The cybersecurity community has been quick to respond—and criticise—this high-level data breach at a company that was supposed to guard their customers’ most sensitive information.
Reddit and cybersecurity communities criticized TransUnion’s decision to outsource its customer support centers to India and Costa Rica, suggesting that offshored IT operations might have weakened the company’s ability to withstand advanced social engineering attacks.
Security experts have looked into the technical side of the breach, emphasizing the social engineering nature of the incident and confirming that the Salesforce platform itself was not compromised.
Many expressed frustration that credit bureaus and financial services companies routinely leak their customers’ sensitive data, the Truist data hack and PayPal data breach being just a few examples. At the same time, affected companies typically offer only 1-2 years of free credit monitoring for their data breach victims, which leaves them vulnerable to long-term data exploitation. This pushes victims to opt for credit freezes as a permanent solution instead of temporary monitoring.
Not the first time: TransUnion’s history of breaches
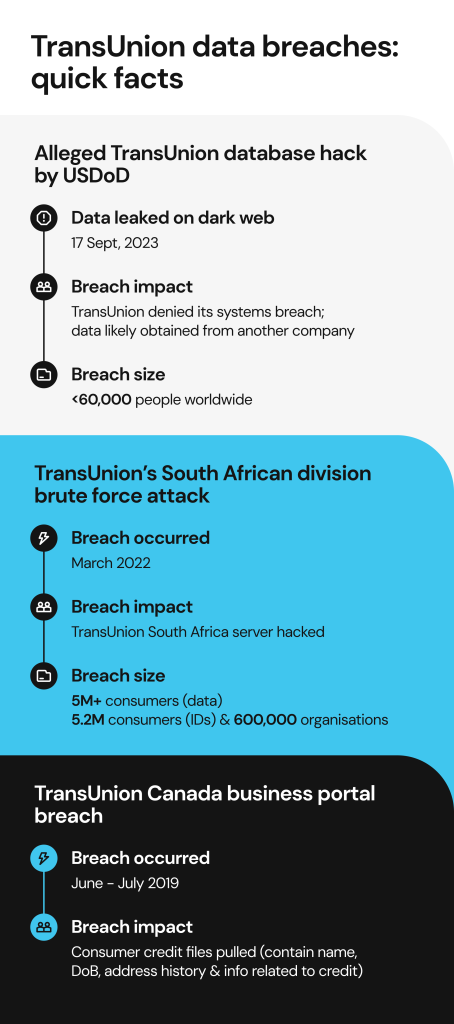
It’s not the first time TransUnion’s digital systems have been compromised.
In 2023, the company denied an alleged hack after a data leak that was later linked to a third party.
In 2022, TransUnion’s South African division suffered a data breach on one of their servers via a brute force attack that allegedly succeeded by using the “password” password to gain access to the system. The attackers then requested a $15 million ransom in exchange for not publishing the stolen data, but TransUnion refused to pay it and engaged cybersecurity, forensic and law enforcement experts instead.
In 2019, a hacker was able to gain unauthorized access to the TransUnion Canada business portal and look up multiple credit files by stealing credentials from a business customer.
Such repeated incidents show a trail of weak vendor management, poor access controls, and recurring third-party vulnerabilities affecting TransUnion customers’ data security.
Why the TransUnion breach matters
The TransUnion data breach is a cautionary tale as it’s not just another tech company losing their users’ emails but one of the most data-rich credit bureaus in the U.S.
Credit bureaus like TransUnion are data brokers by design, holding a vast range of identity data (Social Security numbers, financial behavior, contact information) on almost all U.S. citizens over 18 years old.
This means that even a limited breach can lead to grave consequences. Even if no credit files were affected, exposed personal identifiers can instigate identity theft, phishing, and social engineering attacks on common consumers.
It also signals long-term and far-reaching risks of data exploitation. Criminals can combine data from TransUnion with openly available data and other leaks to build detailed victim profiles for social engineering scams and synthetic identity fraud. For example, adding the full name, birthdate and address to the leaked SSN from TransUnion creates a complete profile ready for exploitation.
How to check if your data was exposed
If you haven’t received an official data breach notification from TransUnion (they started sending them out on August 26, 2025), call their Fraud Victim Assistance Department at 1-800-680-7289. Beware of phishing and stay cautious—legitimate TransUnion reps won’t ask for your full SSN or payment over email or phone.
You can also use breach monitoring tools to check if your data has been leaked in the TransUnion data breach as well as other data breaches:
- Check your email via services like Have I Been Pwned.
- Use services like Onerep for data breach monitoring to scan known leak repositories for signs of your personal records appearing there.
- Combine email monitoring with free weekly reports at AnnualCreditReport.com.
What to do if your information was compromised
Take the following steps to secure your data if it was compromised in the TransUnion breach
- Consider signing up for the free credit monitoring and fraud assistance offered by TransUnion as a temporary protective measure.
- For long-term protection, freeze your credit and place a fraud alert with all the three bureaus (TransUnion, Experian, Equifax).
- Notify your bank and set up fraud alerts in addition to monitoring your financial activity for any suspicious transaction attempts.
- Change passwords and set up two-factor authentication for all major digital accounts.
- Beware of data breach recovery scams as fraudsters frequently exploit breach news to send fake alerts and “compensation” service offers.
For long-term personal data security, consider adopting the following best practices
- Get an IRS IP PIN to prevent tax-return fraud and create a my Social Security account to block unauthorized access.
- Avoid oversharing on social media and elsewhere on the internet as this data is scanned and collected by data brokers and people-search websites for further sale.
- Don’t grant excessive permissions to phone apps, delete your unused online accounts and old data stored in apps and cloud services.
- Remove your publicly available data to reduce your digital footprint and prevent data brokers from collecting your information.
How Onerep can help you stay protected
Onerep removes your personal data from over 230 data brokers and people-search sites that list your personal information, including home address and family relations. Our service automates data opt-outs and continuously monitors new data appearances and relistings.
Data broker databases are frequently exploited by cybercriminals for identity theft and personalizing their phishing attacks. In addition, if any such websites get hacked, Onerep directly prevents your data from being compromised by removing it.
Sign up to Onerep to protect your privacy
FAQs about the TransUnion breach
How do I know if I was part of the TransUnion data breach?
Check for an official mailed letter or contact TransUnion at 1-800-680-7289.
How to check if credit was breached?
Review your free credit reports for unusual accounts or requests at AnnualCreditReport.com.
Can I sue TransUnion for a data breach?
It’s possible to start a class action, although outcomes may vary. One victim of the recent TransUnion data breach has already filed a class action, citing the company’s inability to properly secure the personally identifiable information.
Does a credit freeze stop all fraud?
Credit freeze prevents new accounts from being opened in your name, but it doesn’t stop existing account misuse or related scams.
How long should I monitor my credit after a breach?
It’s advised to monitor your credit for at least 24 months, though continuous monitoring, preferably automated, is recommended.





Mikalai is a Chief Technical Officer at Onerep. With a degree in Computer Science, he headed the developer team that automated the previously manual process of removing personal information from data brokers, making Onerep the industry’s first fully automated tool to bulk-remove unauthorized profiles from the internet.