What is a data leak? Definition, examples, and cybersecurity impact

Has your data ever been leaked? If yes, you know that haunting feeling of expecting the worst—your accounts compromised, your identity stolen, your data exploited. But if not, how do you even check? How do you ensure your personal information never floats up on the dark web or mentioned in security reports?
Data gets exposed online all the time, sometimes accidentally, sometimes intentionally. Privacy Rights Clearinghouse estimates that data breaches have impacted more than 9 billion individuals so far. With millions of user records leaked monthly, it’s easy to see how pervasive data-related incidents are.
This guide will walk you through the data leak definition, its difference from data breaches, key reasons why data leaks happen, and what you can do to protect your online information from exposure and exploitation.
What does a data leak mean?
In short, a data leak is an accidental exposure of one’s sensitive data online or in the physical world. The data leak meaning is encompassing and covers incidents caused by negligence, human error, poor technological infrastructure, as well as lack of proper security protections. It’s like leaving a file cabinet unlocked in plain sight—it doesn’t mean the information gets stolen but it does increase the risks manifold.
Even though many data leaks aren’t malicious or intentional at the start, cybercriminals may take advantage of the leaked data once it’s discovered.
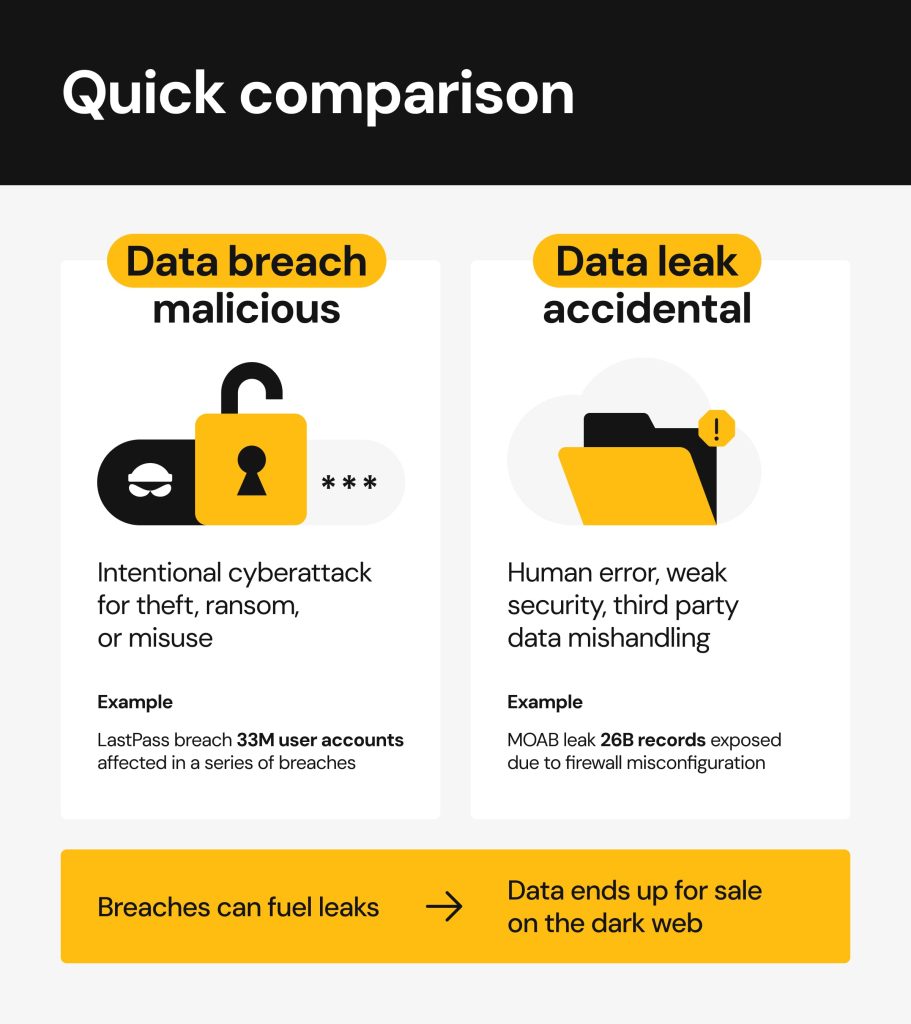
Data leak vs data breach: is there a difference?
Yes, there’s a difference between a data leak and a data breach, even though the two terms are often used interchangeably.
The key difference is intent: data leaks happen accidentally, mostly due to human error or security deficiencies, while data breaches have a malicious intent at the core and involve unauthorized data access as a result of a hacking operation or an exploited vulnerability.
An example of a data leak would be a cloud storage folder left unprotected and indexed by Google. This was the reason behind the Netflix data leak in May 2025, when an unprotected Elastic database exposed 184 million records, including login credentials for Netflix, Microsoft, and Google accounts.
A data breach example would be hackers breaking into a retailer’s system to steal customers’ credit card data. This is what happened in the infamous Target data breach of 2013. As a result of a successful cyberattack, hackers were able to steal 40 million credit card details and get access to personal information of 70 million customers.
In most cases, data leaks are the result of data breaches. Once cybercriminals steal personal data, they may exploit it for identity theft and fraud, or post it on the dark web—in breach dumps and darknet marketplaces—to sell it to other cybercriminals for further abuse.
Types of information exposed in data leaks
Leaks can feature many types of data belonging to employees, contractors, vendors, and users. Depending on the type of the information exposed, it can affect the company’s competitive advantage, legal compliance status, partner relationships, and, most importantly, its reputation with its customers:
- Personally identifiable information (PII), such as names, birthdates, addresses, phone numbers, Social Security numbers.
- Financial data, such as credit card data, banking account credentials, credit scores.
- Login credentials, such as email and password combinations and two-factor authentication codes for various digital accounts.
- Health records, including medical history, prescriptions, lab test results, and Medicare numbers.
- Intellectual property, such as trade secrets, business strategies, and confidential corporate information.
How do data leaks happen?
Human error and insider threats
Mimecast’s State of Human Risk 2025 report shows that 95% of data breaches are caused by human error. This includes data leaks, which can happen when an employee sends sensitive information to a wrong email address by mistake. This is exactly what happened in the Merrill Lynch 401(k) data leak that exposed the sensitive information of Walmart employees. That’s why such risks are often grouped as insider threats coming from within the organization, even if the incident occurred without malicious intent.
Misconfigured cloud storage
When cloud databases and storage buckets are left open without proper user permissions, anyone on the internet can come across and access the information stored. An example of this type of data incident is the 2024 Amazon user data leak through an unprotected HipShipper cloud storage basket.
Weak or missing access controls
When companies lack strong authentication and role-based access controls, unauthorized users can gain access to sensitive data. Weak or reused passwords also make accessing internal systems easier from the outside. In one recent case, a massive user database was left unencrypted and without a password, exposing PayPal login credentials and 184 million user records from other services, apps, email providers, Microsoft products, and many more.
Outdated, unpatched, or shadow IT systems
Old software with known security flows may leave the information open to the public or even accidentally indexed by search engines. The sprawling “shadow IT” applications that are installed and used by employees without their IT department knowing or managing them may also pose data exposure risks.
Third parties mishandling data
Third-party or supply chain risks may lead to sensitive data leaks when a company’s partner or vendor suffers a data breach, or when they mishandle the information in any other way, leaving the other company’s data open for access and exploitation. For example, Bank of America faced at least two data leak incidents tied to third parties mishandling customer records. While such risks are often contained quickly, their impact is far-ranging, affecting multiple companies at a time.
Notable data leakage examples
In May 2025, Facebook suffered a massive data leak as a result of scraping the data of more than 1.2 billion users via an API. The information leaked included usernames, full names, email addresses, birthdates, phone numbers, gender, and geolocation. That same month, Facebook login credentials were also discovered among the unprotected database of 184 million records mentioned above.
In August 2024, MC2 Data, a U.S.-based company running background check services and multiple people-search websites, potentially exposed personal data of one-third of the U.S. population. The data leak occurred due to human error and left 106 million private records openly accessible on the internet via a passwordless database.
But the greatest leak of all times called “Mother of All Breaches” (MOAB) was discovered in January 2024, aggregating 26 billion user records across a dozen of affected platforms, including X.com (Twitter), LinkedIn, Venmo, Tencent, and more. Originally, the MOAB data was attributed to a misconfigured firewall used by Leak-Lookup, a data leak search engine, and thus containing many records that have been exploited previously and that now have only been compiled within the MOAB dataset. However, a later analysis revealed the leak also contained data from 270+ new data breaches, making it the biggest data leak in history.
Data leakage in cybersecurity
As a user of many digital services, you may wonder what the companies behind them do to protect user data. From the consumer perspective, data leakage in cybersecurity is about how companies handle data that you entrust to them.
Behind the scenes, organizations invest heavily in the technological infrastructure and legal compliance to prevent leaks. Not everything may go to plan, as many product companies rely on interconnected networks of third-party services and technologies, but when a company takes cybersecurity seriously, it lowers the chance your personal data ends up in the wrong hands.
Some of the most effective security controls employed by companies to protect their user data include:
- Data encryption
- Zero-trust access controls
- Data loss prevention tools
- Incident response plans
- Regular compliance audits and monitoring
Check if your digital service provider has stated any public commitments to safeguard their customer data and look up their online trust centers for more details on how they secure data in practice.
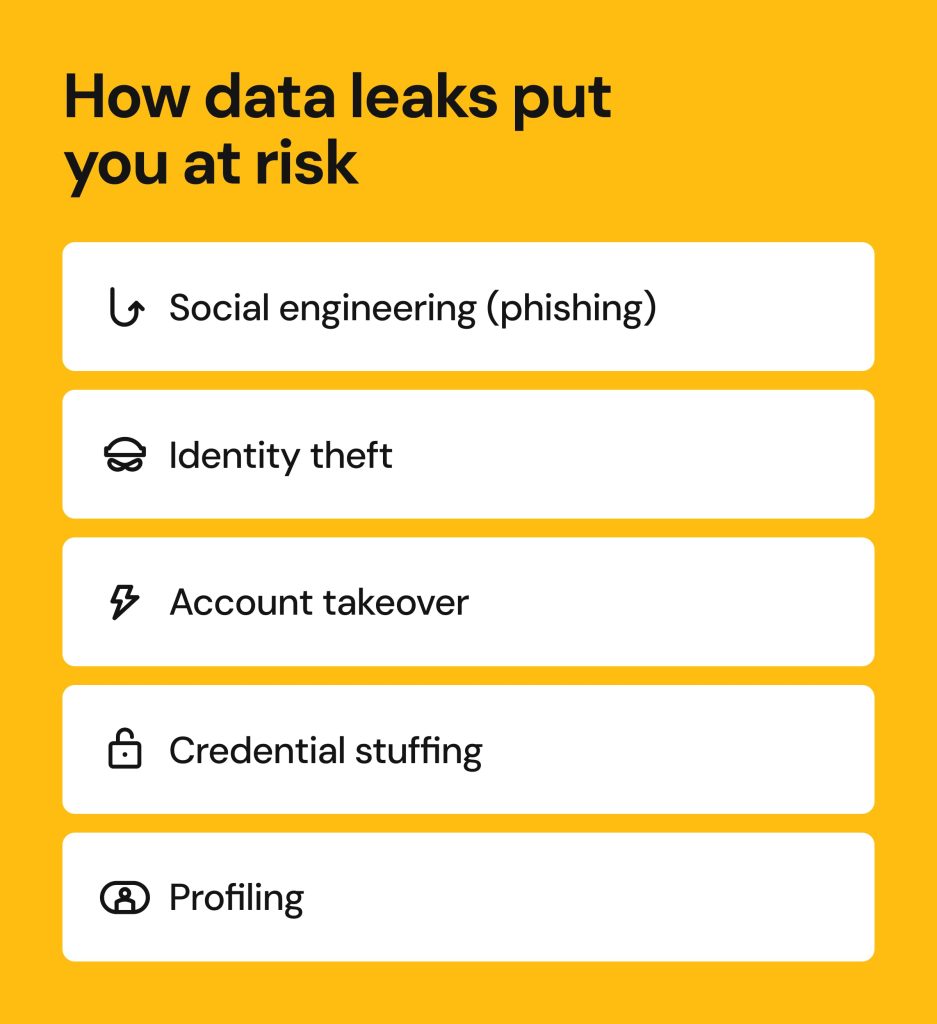
How cybercriminals can exploit leaked data
Once your personal data is exposed, cybercriminals can exploit it in many ways:
- Phishing and social engineering scams: crafting convincing emails, text messages, and phone call scripts to trick you into sharing more sensitive information and banking account data.
- Identity theft to open bank accounts, take loans in your name, or use your insurance.
- Account takeover fraud, involving hijacking your online accounts with leaked credentials, locking you out of them, and making use of the stored data, contacts, and linked credit cards.
- Doxxing and blackmail: bad actors can use your personal information to harass, intimidate, dox or even blackmail you in case they hold private materials about you.
- Credential stuffing: using even a single leaked password, criminals can unleash credential stuffing attacks to gain access to other accounts, which is effective in case of reused passwords.
- Profiling: as a dangerous consequence of leaked personal records, cybercriminals can combine data from multiple leaks and breaches, enrich it with information found on public data brokers and people-search websites, and compile highly detailed profiles to target people in sophisticated personalized scams or just sell these profiles to other scammers on the dark web.
How to check if your information has leaked
One of the simplest ways to see if your email has ever been leaked online is to use Have I Been Pwned. This free service scans across known data leaks and breaches and shows if your email has ever been disclosed in any of them.
You can take the next step and sign up for dark web monitoring software that automatically searches for your personal records mentioned or dumped on the dark web, so you can take timely action and protect your digital accounts and identity.
What to do if your data has been leaked
If you find out your information has been leaked, take the following simple steps to protect yourself:
- Change your passwords for all the affected accounts, avoid reusing passwords, and use a reliable password manager to keep your credentials secure.
- Set up two-factor authentication so cybercriminals have a hard time accessing your accounts unless they somehow obtain your verification code (watch out for strange code requests, too).
- Notify your bank or payment card issuer if your financial and payment information has been exposed. You’ll be able to reissue the card and set up fraud alerts in case a fraudster attempts to exploit your information.
- Stay alert for phishing emails, suspicious messages pretending to be from well-known companies, requests for your personal information, or suspicious banking account activity.
Cybersecurity tips your build resilience moving forward
In addition to the best practices mentioned above, it helps to adopt security habits to minimize your personal data exposure online. While accidental data leaks are often beyond our control as consumers, we can still take precautions to reduce potential risks:
- Minimize the amount of personal information you share online, so it’s harder for cybercriminals to piece together your identity.
- Regularly audit your accounts and delete the ones you no longer use.
- Don’t store your credit card information on third-party services.
- Use a strong unique password for each account.
- Keep your devices updated with the latest security patches.
- Consider subscribing to privacy and data protection tools such as VPNs, security services for email, ad blockers and others.
How Onerep helps you reduce online exposure and stay protected
Public people-search websites and data brokers make data leaks more dangerous as bad actors use these websites to enrich leaked profiles with extra details, such as addresses, phone numbers, family members, and more.
Onerep locates and removes your personal records from 230+ websites, continuously monitoring for new data exposures on your behalf. This means attackers will have less third-party information for your identity profile enrichment, which in turn:
- Reduces your online footprint
- Makes it harder for scammers to identify and target you
- Gives you peace of mind by reducing your attack surface in case of a data leak.
FAQs
What does it mean if you have a data leak?
It means your personal or financial account details have been unintentionally exposed online, leaving you vulnerable to scams and fraud.
Why is Apple saying my password was in a data leak?
Apple’s built-in password manager scans for your credentials in known data leaks. If you see this alert, change this password immediately.
Are data leaks serious?
Yes, even accidental data leaks put your identity, finances, and privacy at risk in case cybercriminals get hold of your leaked records.
How do I stop data leaks?
You can’t prevent companies from accidentally leaking your data, but you can adopt safety practices to minimize your data exposure online, such as using strong passwords and 2FA, monitoring your accounts for suspicious activities, and reducing your online footprint with data removal services like Onerep.





Mikalai is a Chief Technical Officer at Onerep. With a degree in Computer Science, he headed the developer team that automated the previously manual process of removing personal information from data brokers, making Onerep the industry’s first fully automated tool to bulk-remove unauthorized profiles from the internet.